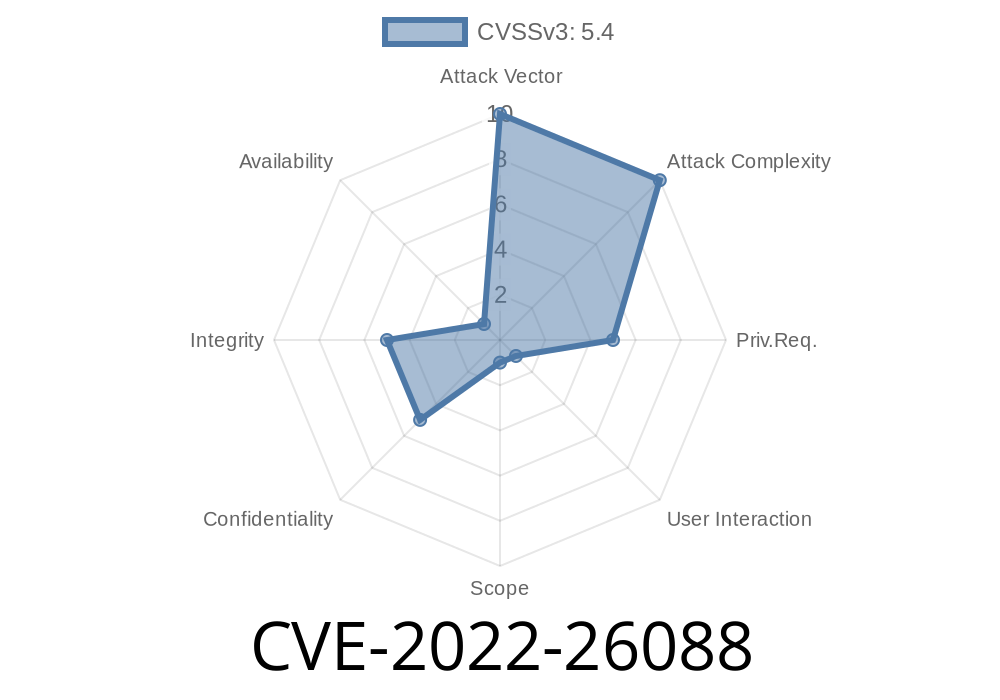
Insecure Direct Object References (IDOR) are possible due to the lack of sanitization in the To field. A remote attacker may leverage this issue to execute a cross-site scripting (XSS) attack, leading to a loss of integrity. An attacker may leverage these issues to access internal data, create a new user, view private information, etc. A remote attacker may leverage these issues to perform phishing attacks, lead to a loss of integrity. This problem has been assigned the CVE ID CVE-2019-3825. An issue was discovered in BMC Remedy before 22.1. Email-based Incident Forwarding allows remote authenticated users to inject HTML (such as an SSRF payload) into the Activity Log by placing it in the To: field. This affects rendering that occurs upon a click in the "number of recipients" field. NOTE: the vendor's position is that "no real impact is demonstrated." Insecure Direct Object References (IDOR) are possible due to the lack of sanitization in the To field. A remote attacker may leverage this issue to execute a cross-site scripting (XSS) attack, leading to a loss of integrity. An attacker may leverage these issues to access internal data, create a new user, view private information, etc. A remote attacker may leverage these issues to perform phishing attacks, lead to a loss of integrity. This problem has been assigned the CVE ID CVE-2019-3825. The vendor addressed this issue
Changes in BMC Remedy
BMC Remedy has issued the following changes in their product release:
- BMC Remedy 22.1 has added a "Use Javascript to search settings" setting to the Settings menu. This setting allows the use of JavaScript in searches, preventing an attacker from injecting HTML (such as an SSRF payload) into the Activity Log by placing it in the To: field.
- BMC Remedy 22.2 includes many fixes for this issue, with particular emphasis on XSS prevention and email-based incident forwarding.
- BMC Remedy 22.3 includes a protection against SQL injection, which can be used in conjunction with XSS protection to prevent XSS vulnerabilities.
Vulnerability Finding Tips
If you are in the process of conducting vulnerability research, there are a few tips to keep in mind.
First, always assume that there is more than one vulnerability. The vendor may say that it's only one but be sure to confirm this with other sources like the CERT and Trustwave.
Second, take note of any publicly available information about the vulnerabilities. If you have access to a past security report from the vendor or their website, note anything that might be relevant to these issues.
Finally, remember that your research will only last so long as the vendor does not release a patch for these issues. Be sure to conduct follow up research if necessary and make sure to report your findings!
Improper Authentication
, Sensitive Data Disclosure
A remote attacker may leverage these issues to perform phishing attacks, lead to a loss of integrity. This problem has been assigned the CVE ID CVE-2019-3825.
Insecure Direct Object References (IDOR) are possible due to the lack of sanitization in the To field. A remote attacker may leverage this issue to execute a cross-site scripting (XSS) attack, leading to a loss of integrity. An attacker may leverage these issues to access internal data, create a new user, view private information, etc. A remote attacker may leverage these issues to perform phishing attacks, lead to a loss of integrity. This problem has been assigned the CVE ID CVE-2019-3825. The vendor addressed this issue
Timeline
Published on: 11/10/2022 21:15:00 UTC
Last modified on: 11/15/2022 20:46:00 UTC