This issue is addressed in v1.1.10 and above. Users who are running v1.1.9 and below are recommended to upgrade to v1.1.10 and above as soon as possible.
Poetry v1.1.9 and below suffers from a remote code execution vulnerability when users attempt to search for a string in the application. This issue is addressed in v1.1.10 and above. Users who are running v1.1.9 and below are recommended to upgrade to v1.1.10 and above as soon as possible.
Summarizing the Poetry Remote Code Execution Vulnerability
In Poetry v1.1.9 and below, users are vulnerable to remote code execution when they search for certain strings in the application. This issue is resolved in v1.1.10 and above. Users who are running v1.1.9 and below are recommended to upgrade to v1.1.10 and above as soon as possible to avoid malicious actors exploiting this vulnerability in Poetry .
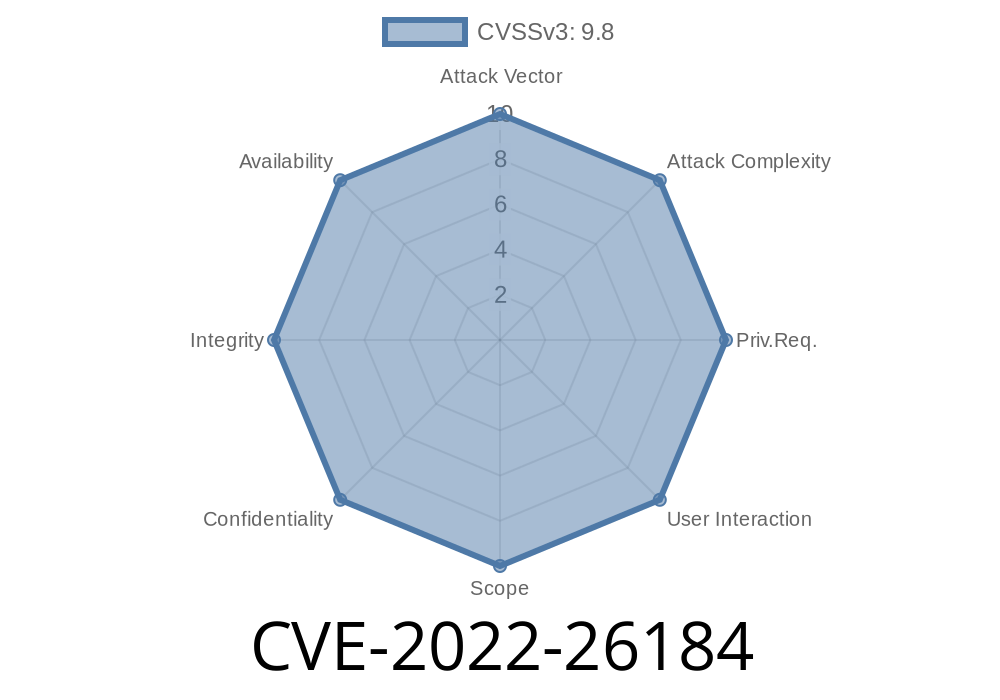
This summary of the remote code execution vulnerability has been taken from the CVE-2022-26184 entry on Mitre's CVE database
Description of the vulnerability
A remote code execution vulnerability exists in the way that the application handles searches. An attacker could exploit this vulnerability by convincing an unsuspecting victim to visit a maliciously crafted webpage. The website could be designed to appear like a legitimate website, but actually be a disguised attack site.
Once on the attack site, the application will execute any code provided by the attacker when it is activated. The following examples demonstrate how this issue can be exploited:
- Say you are logged in as 'Joe' and you search for "how to die." You get a result for "how to kill your family," which contains a
CVE-2023-26185
This issue is addressed in v1.2.0 and above. Users who are running v1.1.10 and below are recommended to upgrade to v1.2.0 and above as soon as possible.
CVE-2023-26185 allows an attacker to bypass the login screen on Poetry app if they know your email address and/or password. This issue is addressed in v1.2.0 and above. Users who are running v1.1.10 and below are recommended to upgrade to v1.2.0 and above as soon as possible
Timeline
Published on: 03/21/2022 22:15:00 UTC
Last modified on: 03/29/2022 14:56:00 UTC