If an attacker can access an appliance management interface, they can exploit FBX-22786. This attack can be prevented by using a virtual management interface, such as VMWare or VirtualBox, or by using the built-in ssh server or setting up an ssh vhost on the management interface. An attacker can exploit FBX-22786 by obtaining access to the management interface on a vulnerable appliance. An unauthenticated user can access the management interface by directly accessing the http or https management interface on the appliance. This access can be obtained by directly accessing the management interface of the appliance, or by accessing the management interface through a web proxy. An attacker can exploit FBX-22786 by issuing commands in the management interface. An unauthenticated user can access the management interface by directly accessing the http or https management interface on the appliance. This access can be obtained by directly accessing the management interface of the appliance, or by accessing the management interface through a web proxy. An attacker can exploit FBX-22786 by issuing commands in the management interface. An unauthenticated user can access the management interface by directly accessing the http or https management interface on the appliance. This access can be obtained by directly accessing the management interface of the appliance, or by accessing the management interface through a web proxy
FBX-23326
An unauthenticated user can access the management interface by directly accessing the http or https management interface on the appliance. This access can be obtained by directly accessing the management interface of the appliance, or by accessing the management interface through a web proxy.
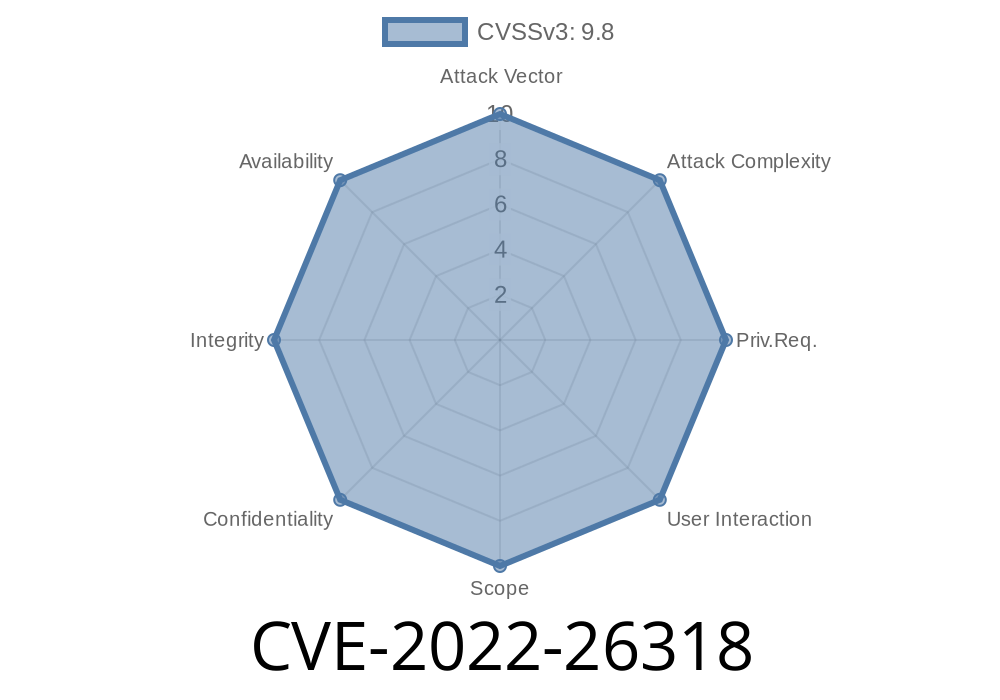
FBX-2022 -26318
If the appliance management interface is exposed, an attacker can exploit FBX-22786. This attack can be prevented by using a virtual management interface, such as VMWare or VirtualBox, or by using the built-in ssh server or setting up an ssh vhost on the management interface. An attacker can exploit FBX-22786 by obtaining access to the management interface on a vulnerable appliance. An unauthenticated user can access the management interface by directly accessing the http or https management interface on the appliance. This access can be obtained by directly accessing the management interface of the appliance, or by accessing the management interface through a web proxy. An attacker can exploit FBX-22786 by issuing commands in the management interface. An unauthenticated user can access the management interface by directly accessing the http or https management interface on the appliance. This access can be obtained by directly accessing the management interface of the appliance, or by accessing it through a web proxy
FBX-22785: If an attacker can access the HTTP interface, they can exploit FBX-22785.
If an attacker can access the HTTP interface, they can exploit FBX-22785. This attack can be prevented by using a virtual management interface, such as VMWare or VirtualBox, or by using the built-in ssh server or setting up an ssh vhost on the management interface. An attacker can exploit FBX-22785 by obtaining access to the management interface on a vulnerable appliance. An unauthenticated user can access the management interface by directly accessing the http or https management interface on the appliance. This access can be obtained by directly accessing the management interface of the appliance, or by accessing the management interface through a web proxy. An attacker can exploit FBX-22785 by issuing commands in the management interface. An unauthenticated user can access the management interface by directly accessing the http or https management interface on the appliance. This access can be obtained by directly accessing the management interface of the appliance, or by accessing the management interface through a web proxy. An attacker can exploit FBX-22785 by issuing commands in source code that is exposed in error messages in various parts of SSABOT's GUI.
FBX-22786 - Nway Appliance Management Interface
If an attacker can access the management interface on a vulnerable appliance, they can exploit FBX-22786. This attack can be prevented by using a virtual management interface, such as VMWare or VirtualBox, or by using the built-in ssh server or setting up an ssh vhost on the management interface. An attacker can exploit FBX-22786 by obtaining access to the management interface on a vulnerable appliance. An unauthenticated user can access the management interface by directly accessing the http or https management interface on the appliance. This access can be obtained by directly accessing the management interface of the appliance, or by accessing the management interface through a web proxy.
FBX-22822
If an attacker can access an appliance management interface, they can exploit FBX-22786. This attack can be prevented by using a virtual management interface, such as VMWare or VirtualBox, or by using the built-in ssh server or setting up an ssh vhost on the management interface. An attacker can exploit FBX-22786 by obtaining access to the management interface on a vulnerable appliance. An unauthenticated user can access the management interface by directly accessing the http or https management interface on the appliance. This access can be obtained by directly accessing the management interface of the appliance, or by accessing the management interface through a web proxy. An attacker can exploit FBX-22786 by issuing commands in the management interface. An unauthenticated user can access the management interface by directly accessing the http or https management interface on the appliance. This access can be obtained by directly accessing the management interface of the appliance, or by accessing the Management Interface through a web proxy
Timeline
Published on: 03/04/2022 18:15:00 UTC
Last modified on: 03/15/2022 15:59:00 UTC