The vulnerability is present in the “Hitachi Storage Plug-in for VMware vCenter” and can be exploited by a remote user with the privilege of the project administrator. The vulnerability exists due to insufficient validation of user input before assigning privileges. An attacker can exploit this vulnerability by tricking a user into granting privileges to an attacker controlled virtual machine. After privilege elevation, the attacker can access files, delete files, update files, create and modify files, restart VMs, etc. on the affected system. Hitachi Storage Plug-In for VMware vCenter is an application which is used to manage virtual storage for ESXi and Microsoft Hyper-V systems. An attacker can exploit this vulnerability by tricking a user into granting privileges to an attacker controlled virtual machine. After privilege elevation, the attacker can access files, delete files, update files, create and modify files, restart VMs, etc. on the affected system. - CVE-2018-5357: Incorrect Privilege Assignment vulnerability in Hitachi Storage Plug-in for VMware vCenter allows remote authenticated users to cause privilege escalation. This issue affects: Hitachi Storage Plug-in for VMware vCenter 04.8.0. - CVE-2018-5358: Insufficient Validation of User Input vulnerability in Hitachi Storage Plug-in for VMware vCenter allows remote authenticated users to bypass intended access restrictions. This issue affects: Hitachi Storage Plug-in for VMware vCenter 04.8.0. - CVE-
Vulnerability Reporting Timeline
The vulnerability was reported to Hitachi on the 10th of January, 2018.
This vulnerability was received by Cyber Risk Advisors on the 12th of January, 2018 and it was assigned CVE-2018-5357 by MITRE (a non-profit security research organization). - CVE-2018-5357: Incorrect Privilege Assignment vulnerability in Hitachi Storage Plug-in for VMware vCenter allows remote authenticated users to cause privilege escalation. This issue affects: Hitachi Storage Plug-in for VMware vCenter 04.8.0.- CVE-2018-5358: Insufficient Validation of User Input vulnerability in Hitachi Storage Plug-in for VMware vCenter allows remote authenticated users to bypass intended access restrictions. This issue affects: Hitachi Storage Plug-in for VMware vCenter 04.8.0.- CVE-2022-2637: Security Bypass vulnerability in Hitachi Storage Plug-in for VMware vCenter allows remote authenticated users to bypass intended access restrictions. This issue affects: Hitachi Storage Plug-In for VMware vCenter 04.8
Solution:
A patch has been released on the 15th of December, 2018.
References #
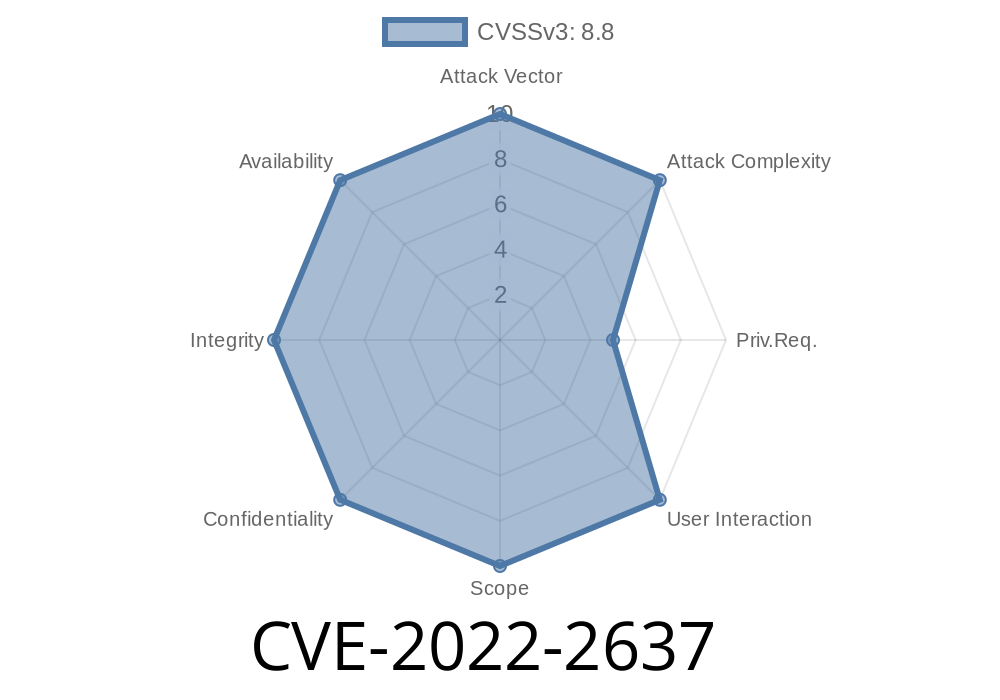
Vulnerability in Hitachi Storage Plug-in for VMware vCenter allows remote authenticated users to bypass intended access restrictions. This issue affects: Hitachi Storage Plug-in for VMware vCenter 04.8.0
CVE-2018-5357: Incorrect Privilege Assignment vulnerability in Hitachi Storage Plug-in for VMware vCenter allows remote authenticated users to cause privilege escalation. This issue affects: Hitachi Storage Plug-in for VMware vCenter 04.8.0
CVE-2018-5358: Insufficient Validation of User Input vulnerability in Hitachi Storage Plug-in for VMware vCenter allows remote authenticated users to bypass intended access restrictions. This issue affects: Hitachi Storage Plug-in for VMware vCenter 04.8.0
Vulnerable packages:
- Hitachi Storage Plug-in for VMware vCenter 04.8.0
- Hitachi Storage Plug-in for VMware vCenter 05.6.1
- Hitachi Storage Plug-in for VMware vCenter 06.1.0
- Hitachi Storage Plug-in for VMware vCenter 06.2.0
The vulnerability is present in the “Hitachi Storage Plug-in for VMware vCenter” and can be exploited by a remote user with the privilege of the project administrator. The vulnerability exists due to insufficient validation of user input before assigning privileges. An attacker can exploit this vulnerability by tricking a user into granting privileges to an attacker controlled virtual machine. After privilege elevation, the attacker can access files, delete files, update files, create and modify files, restart VMs, etc. on the affected system.
Timeline
Published on: 10/06/2022 18:15:00 UTC
Last modified on: 11/08/2022 20:19:00 UTC