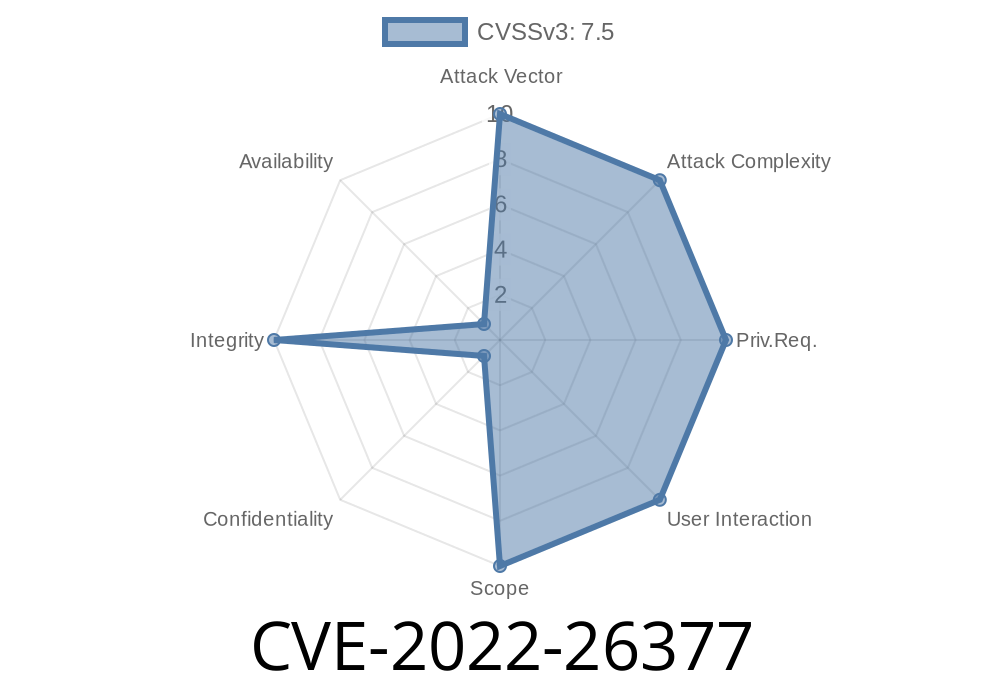
mod_proxy_ajp is a module that enables proxying of requests to one or more remote servers. This module is enabled by default in Apache. When enabled, mod_proxy_ajp generates an HTTP request and forwards it to the specified remote server. This issue occurs due to the fact that mod_proxy_ajp does not check the protocol scheme of the request it forwards. An attacker can leverage this vulnerability to inject any scheme that he wants, by choosing the desired scheme of the forwarded request.
Hackers can exploit this vulnerability to inject malicious requests to vulnerable Apache installations. These requests can be anything and do anything. The only limitation is imagination of the hacker. An attacker can exploit this vulnerability to perform any action, as the forwarded request reaches the intended destination. End-users are not likely to be impacted, as most of the end-user-facing components are not vulnerable. However, it is possible for a malicious user to exploit this vulnerability to perform any action on the target server. Mitigation In order to mitigate this issue, ensure that the Apache HTTP Server is running the latest version.
Update Apache HTTP Server to the latest version
The latest version of Apache HTTP Server is 3.4.3.
Apache HTTP Server Is Up To Date
This is an issue with the Apache HTTP Server, rather than a vulnerability on specific Apache modules. It is recommended to update your version of the Apache HTTP Server to the latest version available.
Since this issue is associated with the Apache HTTP Server and not a specific module, updates are required across all modules that are enabled in order to ensure that you can mitigate against this issue. Updates should be downloaded from the official website for your distribution or use one of the package managers available in your operating system.
Timeline
Published on: 06/09/2022 17:15:00 UTC
Last modified on: 08/24/2022 18:25:00 UTC
References
- http://www.openwall.com/lists/oss-security/2022/06/08/2
- https://httpd.apache.org/security/vulnerabilities_24.html
- https://security.netapp.com/advisory/ntap-20220624-0005/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/YPY2BLEVJWFH34AX77ZJPLD2OOBYR6ND/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/7QUGG2QZWHTITMABFLVXA4DNYUOTPWYQ/
- https://security.gentoo.org/glsa/202208-20
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-26377