*Published June 2024*
*By SecurePulse Research Team*
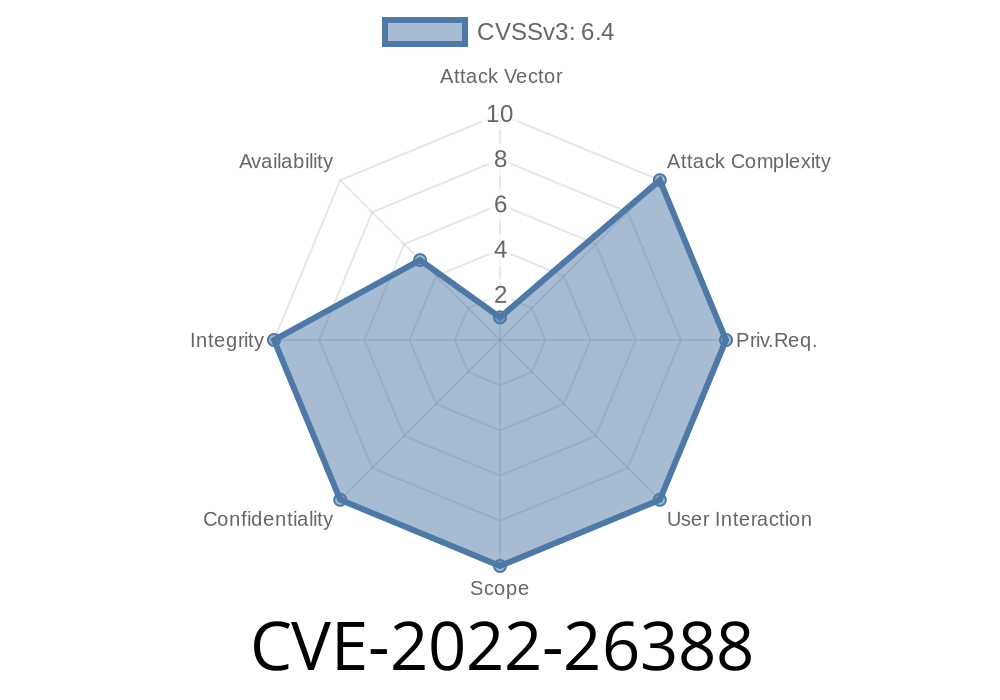
Medical devices help save lives — but what happens when those same devices are left wide open for attackers? Today, we’re taking a close look at CVE-2022-26388, which exposes a worrying vulnerability in several Mortara/Philips ELI resting electrocardiograph models. This isn’t just a theoretical risk: devices in hospital wards and clinics everywhere are at risk due to hard-coded passwords.
If you work in healthcare IT, are responsible for medical device security, or are just curious about real-world vulnerabilities, read on. This detailed guide breaks down what CVE-2022-26388 is, how attackers could exploit it, and what you can do to keep your patients safe.
What Is CVE-2022-26388?
CVE-2022-26388 refers to a vulnerability discovered in popular lines of Mortara/Philips ELI resting electrocardiographs. In plain English: these devices ship with a password built into the software that cannot be changed, or at least not easily.
If someone knows this password (and attackers can figure it out, as you’ll see), they could abuse authentication — unlocking device controls, accessing patient data, or even manipulating device settings.
Versions 2.6. and earlier
- ELI 280/BUR280/MLBUR 280 Resting Electrocardiograph:
Versions 2.3.1 and earlier
- ELI 250c/BUR 250c Resting Electrocardiograph:
Versions 2.1.2 and earlier
- ELI 150c/BUR 150c/MLBUR 150c Resting Electrocardiograph:
Versions 2.2. and earlier
If your facility is using any of these versions (or aren’t sure), you’re at risk.
Why Are Hard-Coded Passwords Dangerous?
In most modern software or devices, users can set and change their passwords. But with hard-coded credentials, the password is stuck in the device’s source code or firmware.
Here’s the risk:
- If an attacker finds this password (from the internet, leaked code, or simply reverse engineering), it’ll work on every machine with that version.
Hospital staff may not even know the password exists!
- Password resets and best practices are made useless if attackers can always rely on the same credential.
Hard-coded passwords have been the cause of many notorious attacks — making it nearly impossible for defenders to respond effectively.
Physical Access
- An attacker (or even a malicious insider) gets physical access to the ELI machine. They discover a “Service” or “Technical” menu that asks for a hidden password.
Network Access
- Some ELI models connect to a network for data transfer. If remote management (like over HTTP or Telnet) is enabled, the attacker could try to log in remotely using the hard-coded credentials.
Realistic Attack Flow
Say an attacker finds documentation or some repo mentioning the hard-coded password — for instance, techsupport!202. Here’s how they might exploit it:
import requests
# Hypothetical login endpoint for ELI device
url = 'http://eli-device.local/login';
data = {
'username': 'service',
'password': 'techsupport!202' # Hard-coded default!
}
session = requests.session()
response = session.post(url, data=data)
if "Welcome" in response.text:
print("[+] Login successful! Device compromised.")
else:
print("[-] Exploit failed. Try a different password.")
*Note: This code is for educational purposes only!*
Handling real devices without permission is illegal.
How Was This Found? (References & Research)
The original vulnerability report was published by CISA, with further technical analysis from the security community.
- CISA Advisory ICSA-22-179-01
- Philips Product Security Advisory
- NIST National Vulnerability Database CVE-2022-26388
Update Immediately:
If a firmware/software update is available, apply it ASAP. Philips released patches for many models.
Segment Networks:
Place medical devices on isolated VLANs so attackers can’t reach them from general hospital networks.
Final Thoughts
CVE-2022-26388 highlights why hard-coded passwords are always a bad idea — especially in life-critical systems. As more medical devices are connected to networks, attackers are eyeing new targets. It’s up to manufacturers, hospitals, and users to demand better security, enforce updates, and never settle for “good enough.”
Have you checked your hospital’s medical devices for hidden passwords? Now is the time.
SecurePulse Team
*Stay safe. Stay updated.*
Timeline
Published on: 02/07/2025 17:15:21 UTC