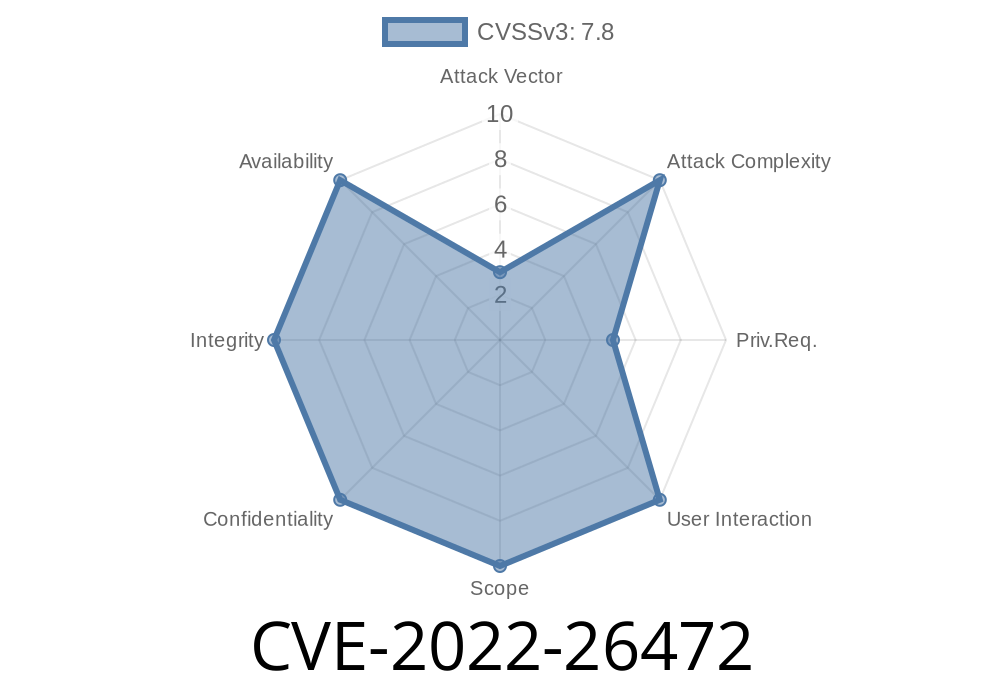
There are issues with the default configuration of ims, where it is possible to obtain escalated privileges. By manipulating the system’s trust in a malicious SCCM agent, an attacker can gain elevated privileges on the system. It is important to note that this issue is only exploitable if SCCM is configured to use a X.500 or Active Directory Certificate Authority (CA) for HTTPS communication. SCCM will not prompt the user for confirmation when connecting to a trusted CA. Exploitation of this issue requires user interaction. Patch ID: ALPS07319096; Issue ID: ALPS07319096.
There are a number of issues with the default configuration of ims, where it is possible to obtain escalated privileges. By manipulating the system’s trust in a malicious SCCM agent, an attacker can gain elevated privileges on the system. It is important to note that this issue is only exploitable if SCCM is configured to use a X.500 or Active Directory Certificate Authority (CA) for HTTPS communication. SCCM will not prompt the user for confirmation when connecting to a trusted CA. Exploitation of this issue requires user interaction. Patch ID: ALPS07319096; Issue ID: ALPS07319096. SCCM can be exploited remotely via unauthenticated HTTP or HTTPS connections. There are a number of ways that an attacker could access SCCM, such as a compromised workstation
Note: Access to SCCM is restricted to administrative users
, or users with appropriate permissions.
The following are examples of exploitable SCCM configurations
- Ensure that SCCM is configured to connect to a X.500 or Active Directory Certificate Authority (CA) for HTTPS communication
- Ensure that the system’s trust in the agent is not revoked when the user logs out of their session
SCCM can be exploited remotely via unauthenticated HTTP or HTTPS connections
Exploitation of this issue requires user interaction. Patch ID: ALPS07319096; Issue ID: ALPS07319096. SCCM can be exploited remotely via unauthenticated HTTP or HTTPS connections. There are a number of ways that an attacker could access SCCM, such as a compromised workstation or by having access to the SCCM server's network share.
SCCM can be exploited remotely via unauthenticated HTTP or HTTPS connections. There are a number of ways that an attacker could access SCCM, such as a compromised workstation or by having access to the SCCM server's network share.
SCCM and MS Remote Desktop Services (RDS) are vulnerable to remote code execution
The default configuration of ims, where it is possible to obtain escalated privileges. By manipulating the system’s trust in a malicious SCCM agent, an attacker can gain elevated privileges on the system. It is important to note that this issue is only exploitable if SCCM is configured to use a X.500 or Active Directory Certificate Authority (CA) for HTTPS communication. SCCM will not prompt the user for confirmation when connecting to a trusted CA. Exploitation of this issue requires user interaction. Patch ID: ALPS07319096; Issue ID: ALPS07319096. SCCM can be exploited remotely via unauthenticated HTTP or HTTPS connections by sending specially crafted XML packets or RDP packets over TCP port 992 and via UDP port 5089 and 5090
Authentication bypass
Authentication bypass is possible through the use of a Java applet. If a Java applet can be run from an arbitrary location and it has the ability to access SCCM, then remote attacker could still exploit the system. Furthermore, there is no indication that any action is taken upon successful authentication, which could allow a remote attacker to connect to SCCM using a malformed HTTPS certificate.
There are issues with the default configuration of ims, where it is possible to obtain escalated privileges. By manipulating the system’s trust in a malicious SCCM agent, an attacker can gain elevated privileges on the system. It is important to note that this issue is only exploitable if SCCM is configured to use a X.500 or Active Directory Certificate Authority (CA) for HTTPS communication. SCCM will not prompt the user for confirmation when connecting to a trusted CA. Exploitation of this issue requires user interaction. Patch ID: ALPS07319096; Issue ID: ALPS07319096. SCCM can be exploited remotely via unauthenticated HTTP or HTTPS connections. There are a number of ways that an attacker could access SCCM, such as a compromised workstation
Timeline
Published on: 10/07/2022 20:15:00 UTC
Last modified on: 10/11/2022 16:26:00 UTC