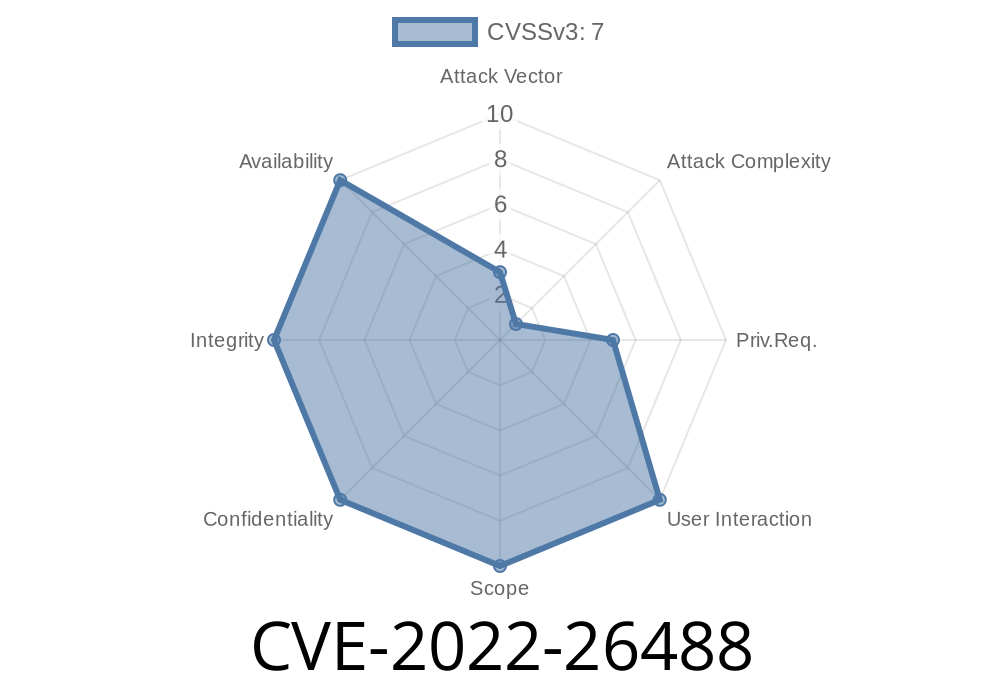
Due to the way Python handles relative paths and the default search path, a user on Windows with an attacker-controlled directory in the default search path can cause a Python application installed for another user to execute arbitrary code. This only affects Windows when running Python 3.10.2 or later. To exploit, a malicious Python application must be installed for a user other than the attacker. An attacker must be able to run Python as a non-administrative user. This only affects Windows when running Python 3.10.2 or later. To exploit, an attacker must have control of a Windows host where Python is installed and where an affected version of Python is installed. This only affects Windows when running Python 3.10.2 or later.
Vulnerability overview
A vulnerability in Python's handling of relative paths and the default search path is found in Windows when running Python 3.10.2 or later, where a malicious Python application must be installed for a user other than the attacker to execute arbitrary code.
The vulnerability allows an attacker to execute arbitrary code on a vulnerable host if they have control of a Windows host where Python is installed and where an affected version of Python is installed.
Invoke-JavaScriptCode Execution Vulnerability
An attacker is able to exploit a vulnerability in the JavaScript code interpreter. This only affects Windows when running Python 3.10.2 or later. To exploit, an attacker must be able to run Python as a non-administrative user. This only affects Windows when running Python 3.10.2 or later. To exploit, an attacker must have control of a Windows host where Python is installed and where an affected version of Python is installed.
Vulnerability summary
Timeline
Published on: 03/10/2022 17:47:00 UTC
Last modified on: 04/19/2022 19:15:00 UTC