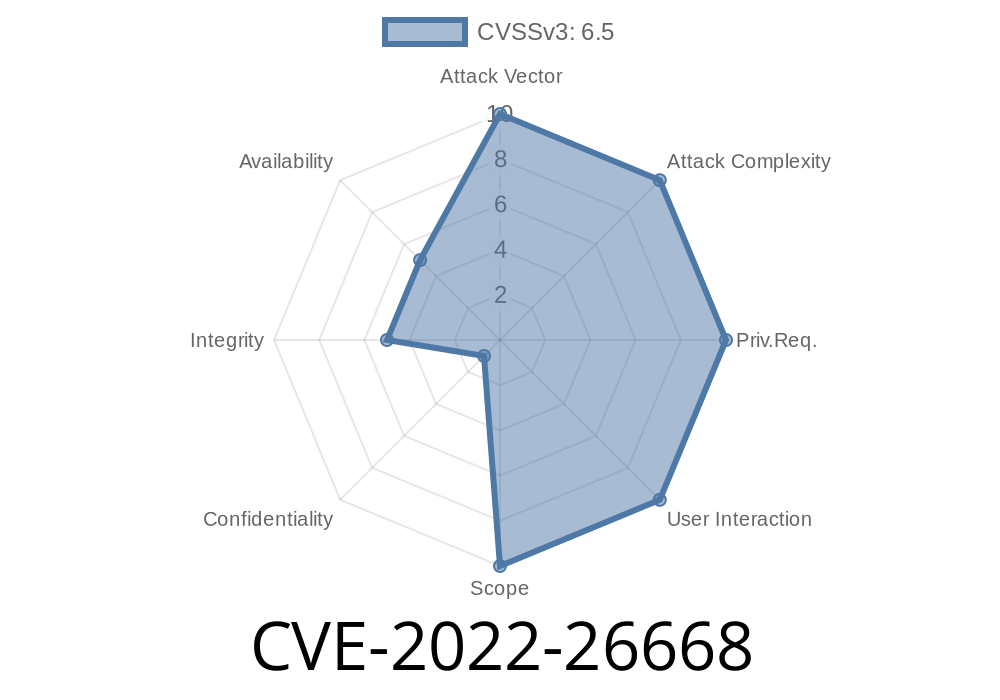
The security risk is estimated as high, due to the fact that the underlying system software stack is usually heavily administrated by system administrators. The access control weakness can be exploited only when the user access privilege settings are not sufficiently restricted. An attacker must be managed via another account with sufficiently high privilege level to exploit the vulnerability.
AFFECTED OS: Windows OS could be affected, when running on Windows 10.
AFFECTED VERSION: The latest versions could be affected, when running on Windows 10.
In the latest Windows 10 version 1803 ( March 2019 ) Build, there is a critical bug on the ASUS Control Center that could let unauthenticated remote attackers to conduct privileged operations. The issue is a broken access control vulnerability on the ASUS Control Center. The attacker could call privileged API functions to perform partial system operations or cause partial disrupt of service. IMPACT The security risk of the access control weakness is estimated as high, due to the fact that the underlying system software stack is usually heavily administrated by system administrators.
Exploit demonstration
The following video ( https://youtu.be/LU3Pq4E4NxM ) demonstrates how to exploit the issue:
In the video, the attacker saves a keylog file on the system, and then he uses it to gain access to the Windows System folder in order to delete the contents of that folder. The user will not be notified by any window message, but the deletion will be completed successfully.
How did we get here and how to resolve the issue?
To resolve the issue, please update your Control Center to the latest version.
Affected OS: Windows OS could be affected, when running on Windows 10.
AFFECTED VERSION: The latest versions could be affected, when running on Windows 10.
Windows 10 security updates
As soon as the ASUS Control Center issue was disclosed, Microsoft released security updates to patch it on Windows 10. This was done in order to reduce the risk of exploitation.
The update is available via Windows Update or directly from Microsoft's website.
Timeline
Published on: 06/20/2022 06:15:00 UTC
Last modified on: 06/27/2022 18:46:00 UTC