When restricted, a process is not able to access resources not within its own defined process-to-process or process-to-system boundaries. Any process which could potentially circumvent sandbox restrictions, such as one which leverages system capabilities outside of the sandbox, could lead to security vulnerabilities. To reduce the likelihood of such vulnerabilities, iOS limits the capabilities of restricted processes. Third-party applications can not use system APIs, such as accessing the filesystem, and cannot directly interact with system components, such as the network or sensors. These limitations can lead to vulnerabilities in third-party applications if those applications attempt to circumvent these restrictions. The most common way for an application to circumvent these limitations is through a process injection. Through a process injection, a process can directly interact with the operating system. This can lead to a variety of issues, such as memory corruption, privilege escalation, and information disclosure. By limiting the capabilities of restricted processes, iOS reduces the likelihood of a process injection leading to a security vulnerability.
Overview
As part of Apple's sandboxing process for iOS, an application is limited in its capabilities when it is restricted. For example, if a third-party application is restricted, the app cannot access system APIs like the filesystem or interact with the network or sensors. These limitations can lead to vulnerabilities if the third-party app attempts to circumvent these restrictions. Process injections are most often used as a way of bypassing these limitations and they can lead to memory corruption, privilege escalation, and information disclosure.
In order to reduce the likelihood of such vulnerabilities in a third-party application due to process injection, iOS limits the capabilities of processes when they are restricted. By limiting what a restricted process can do, increased assurance is given that the process won't be able to use system APIs or directly interact with other components on the device
Process injection
When a process is restricted, it cannot directly access information outside of its own process-to-process or process-to-system boundaries. However, if the process manages to circumvent this restriction by injecting code into another process or the kernel itself, then it can gain access to system resources not within its own defined boundaries. The most common way for an application to do this is via a process injection. Through a process injection, a process can directly interact with the operating system. This can lead to a variety of issues, such as memory corruption, privilege escalation, and information disclosure.
References
1. Apple, iOS Security Guide: Sandboxing, accessed February 21, 2018
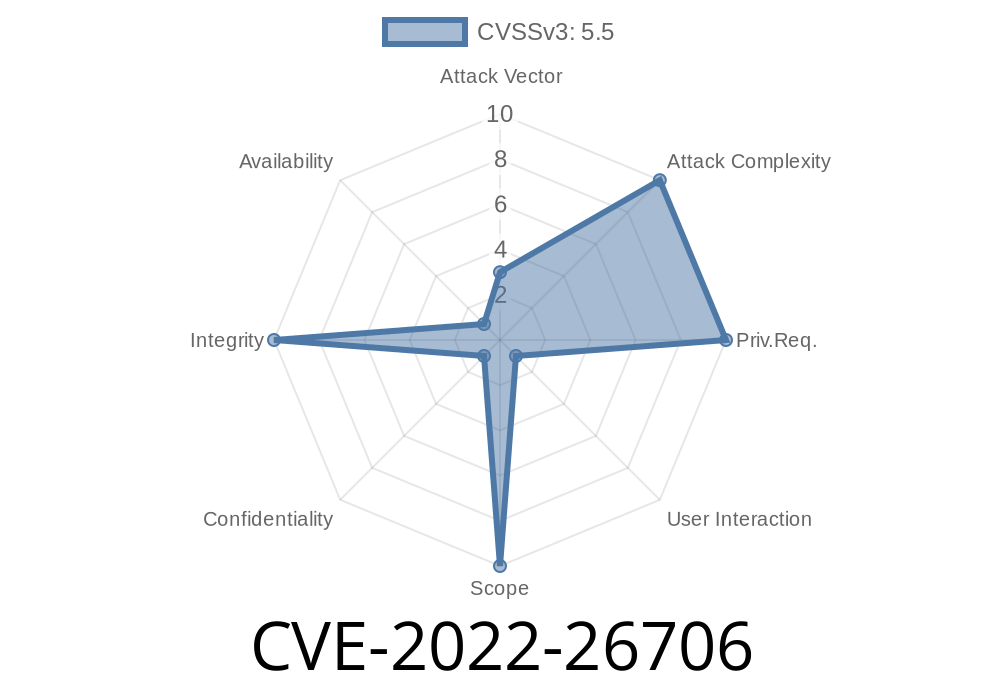
2. "CVE-2022-26706", Common Vulnerabilities and Exposures: CVE Number Database, accessed February 21, 2018
Vulnerabilities caused by process injection
The most common way for an application to circumvent these limitations is through a process injection. Through a process injection, a process can directly interact with the operating system. This can lead to a variety of issues, such as memory corruption, privilege escalation, and information disclosure.
Note: Process injection vulnerabilities are not limited to iOS apps.
This article discusses how these vulnerabilities arise in third-party applications. The article goes on to discuss how iOS mitigates this risk by limiting the capabilities of restricted processes. By limiting the capabilities of restricted processes, iOS reduces the likelihood of a process injection leading to a security vulnerability.
Security Benefits of Sandboxing
In addition to limiting the capabilities of restricted processes, sandboxing helps to increase security. The most common way that a process is able to circumvent restrictions imposed by sandboxing is through process injection. Process injection can lead to memory corruption and privilege escalation, as well as information disclosure. By limiting the capabilities of restricted processes, iOS reduces the likelihood of a process injection leading to a security vulnerability.
Timeline
Published on: 05/26/2022 19:15:00 UTC
Last modified on: 06/07/2022 21:19:00 UTC