This issue is due to the way that the PowerShell engine handles objects. When a user creates a new object in the system, the object is created with a user-defined constructor. The constructor is where the object’s security profile is set. If an attacker can find a way to inject code into a user’s constructor, then he can elevate his privileges on the system.
In the case of the PowerShell Elevation of Privilege Vulnerability, the attacker injects malicious constructor code into the system. The malicious code then runs when the user creates a new object. The attacker now has full access to the system and the victim’s data, due to the attacker’s elevated privilege. Microsoft has released a patch for this issue, which you can find here.
CVE-2023-26824
This issue is due to the way that Internet Explorer handles objects. When an object is created in IE, it has a default constructor. The default constructor is where the object’s security profile is set. If an attacker can find a way to inject code into a user’s default constructor, then he can elevate his privileges on the system.
In the case of I-E Elevation of Privilege Vulnerability, the attacker injects malicious default constructor code into the system. The malicious code then runs when a new object is created in IE. The attacker now has full access to the system and the victim’s data, due to the attacker’s elevated privilege. Microsoft has released a patch for this issue, which you can find here.
Windows Hosts and Services:
What You Need to Know
Protecting your Windows Hosts and Services is essential for the security of your organization. If you are not following best practices, then you are leaving your system vulnerable to attacks. Attackers know that Windows is a popular operating system and they might attack your system in order to steal sensitive data or take control of the whole network.
In order to stay protected, you need to follow these best practices:
- Monitor all patches and updates that arrive on your Windows Hosts and Services
- Keep the OS up-to-date with the latest service pack, hot fixes, and patches
- Restrict access to only those users who absolutely need administrative privileges - Enable strong passwords on all accounts of Windows Hosts and Services
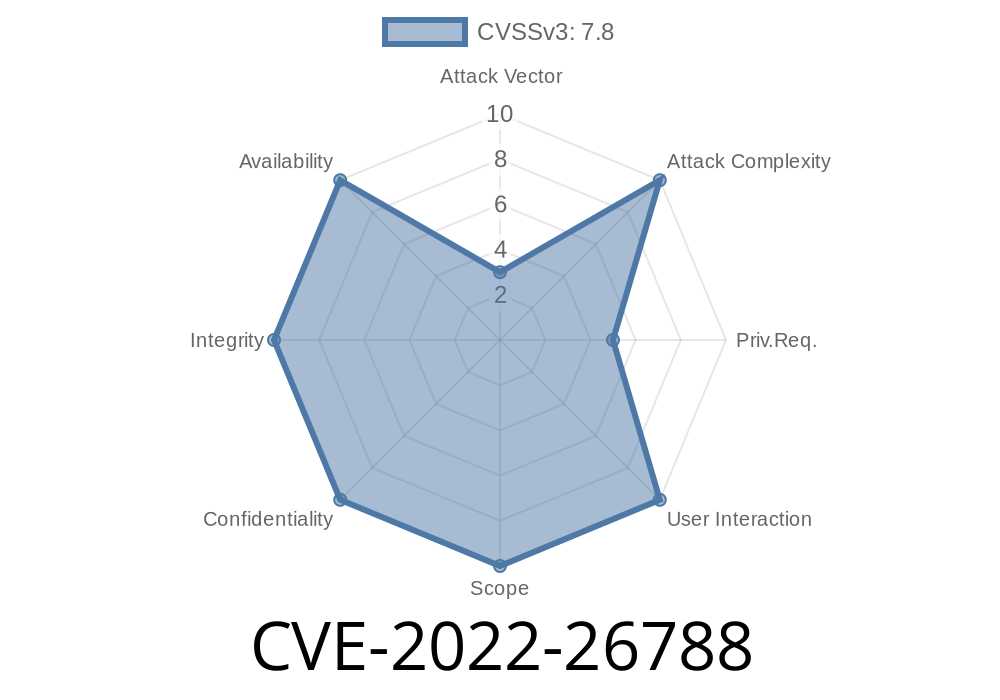
Microsoft PowerShell Vulnerability - CVE-2021 -26788
This issue is due to the way that the PowerShell engine handles objects. When a user creates a new object in the system, the object is created with a user-defined constructor. The constructor is where the object’s security profile is set. If an attacker can find a way to inject code into a user’s constructor, then he can elevate his privileges on the system.
In the case of Microsoft PowerShell Elevation of Privilege Vulnerability, the attacker injects malicious constructor code into the system. The malicious code then runs when the user creates a new object. The attacker now has full access to the system and the victim’s data, due to his elevated privilege. Microsoft has released a patch for this issue, which you can find here.
Microsoft Office Document Information Disclosure Vulnerability
The Microsoft Office Document Information Disclosure Vulnerability is one of the most serious vulnerabilities that has been found in a recent time. This vulnerability affects every version of Microsoft Office, from 2003 to 2016. The vulnerability is caused by a flaw in how Microsoft Office handles objects. When a user creates a new object in the system, the object is created with a user-defined constructor. The constructor is where the object’s security profile is set. If an attacker can find a way to inject code into a user’s constructor, then he can elevate his privileges on the system.
This issue was fixed by Microsoft with their Patch Tuesday update on March 14th, 2018. There are two ways to protect your computer: you can update your software or use alternative software such as LibreOffice or OpenOffice. A safe alternative would be to have both programs installed on your computer at once and switch between them when necessary.
Microsoft Outlook Vulnerability
The Microsoft Outlook vulnerability is another example of the importance of using the latest patch updates. This issue is due to Microsoft’s “Outlook Social Encoder Tool,” which allows users to send out an email that contains a link to content stored on a social media platform. When this tool is used, it sends out the email with the malicious code in the body, allowing an attacker to take control over your system.
This security issue was fixed by Microsoft in September 2017 and you can get more information here.
Timeline
Published on: 04/15/2022 19:15:00 UTC
Last modified on: 04/25/2022 16:29:00 UTC