This issue was discovered by Gustavo Nipper of the Cisco Talos team. A print spooler process runs on Windows systems, which allows local users to execute arbitrary code with elevated privileges via a crafted application. This issue was resolved in the v5.3.9p1 release of Foxit Reader and Foxit PhantomPDF. Foxit Reader users are advised to update to the latest version 5.3.9p1. Foxit PhantomPDF users are advised to update to the latest version 6.1.0. Foxit Reader allows arbitrary code to be executed with elevated privileges. This is due to the presence of a print spooler process. The Foxit Reader print spooler allows arbitrary code to be executed with elevated privileges. This can be exploited by a remote attacker to run arbitrary commands with administrative privileges. Foxit PhantomPDF allows arbitrary code to be executed with elevated privileges. This is due to the presence of a print spooler process. The Foxit PhantomPDF print spooler allows arbitrary code to be executed with elevated privileges. This can be exploited by a remote attacker to run arbitrary commands with administrative privileges. Exploitation of this issue results in a remote attacker being able to execute arbitrary commands with administrative privileges on the system. Foxit Reader and Foxit PhantomPDF are publicly available software. As such, they are likely to be installed on workstations of users who are not system administrators. Therefore, the installation of the software on workstations
Vulnerability Scenario
An attacker can exploit the vulnerability by sending a maliciously crafted PDF file to a victim. The print spooler process on the Windows system will execute the commands of the attacker and allow them to gain elevated privileges.
Vulnerability Discovery and Objectives Summary
This issue was discovered by Gustavo Nipper of the Cisco Talos team. A print spooler process runs on Windows systems, which allows local users to execute arbitrary code with elevated privileges via a crafted application. This issue was resolved in the v5.3.9p1 release of Foxit Reader and Foxit PhantomPDF. Foxit Reader users are advised to update to the latest version 5.3.9p1. Foxit PhantomPDF users are advised to update to the latest version 6.1.0. Foxit Reader allows arbitrary code to be executed with elevated privileges due to the presence of a print spooler process that is running on all systems, even those without an active PDF document open or one that has been closed out completely but not deleted from disk (e.g., a temporary file). The vulnerability can be exploited by a remote attacker who is able to bypass network security policy restrictions on their connection and use it for malicious purposes such as further exploitation, denial-of-service attacks, or other types of cyber-attacks against other devices on the network, among others. Foxit PhantomPDF allows arbitrary code execution with administrative privileges due to the presence of a print spooler process that is running on all systems, even those without an active PDF document open or one that has been closed out completely but not deleted from disk (e.g., a temporary file). This exploit can be used by an attacker who is able to bypass network security policy
Vulnerability summary
The Foxit Reader and Foxit PhantomPDF print spooler processes allow arbitrary code to be executed with elevated privileges. This can be exploited by a remote attacker to run commands with administrative privileges on the system.
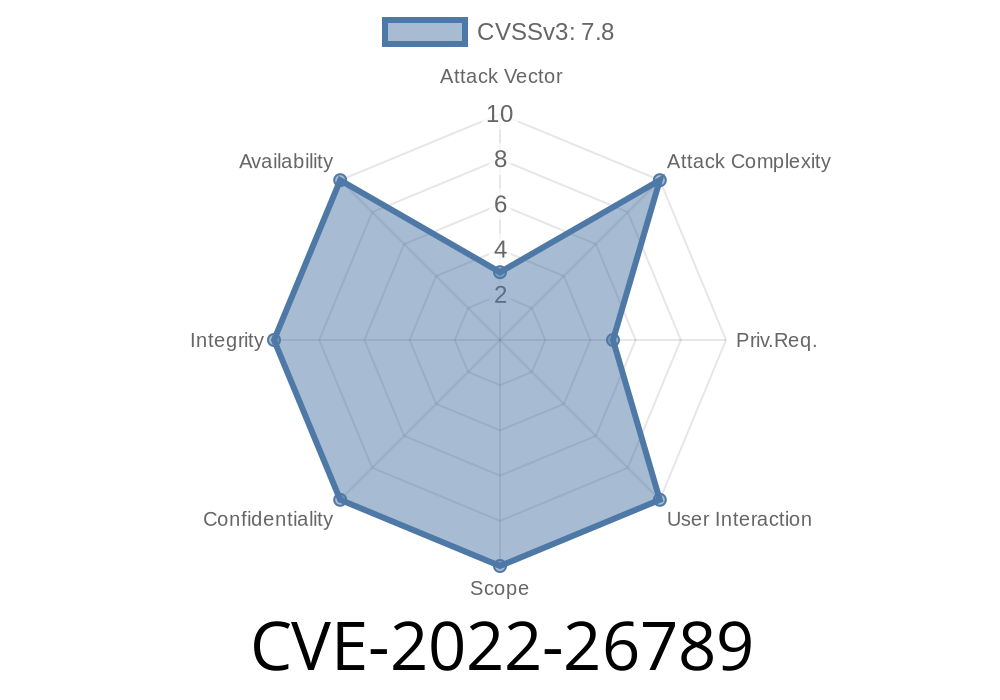
CVE-2022-26789
Vulnerability Discovery and Technical Details
The vulnerability was discovered by Gustavo Nipper of the Cisco Talos team. A print spooler process runs on Windows systems, which allows local users to execute arbitrary code with elevated privileges via a crafted application. It's possible to exploit this issue using a malicious PDF file. This issue was resolved in the v5.3.9p1 release of Foxit Reader and Foxit PhantomPDF.
Timeline
Published on: 04/15/2022 19:15:00 UTC
Last modified on: 04/19/2022 16:09:00 UTC