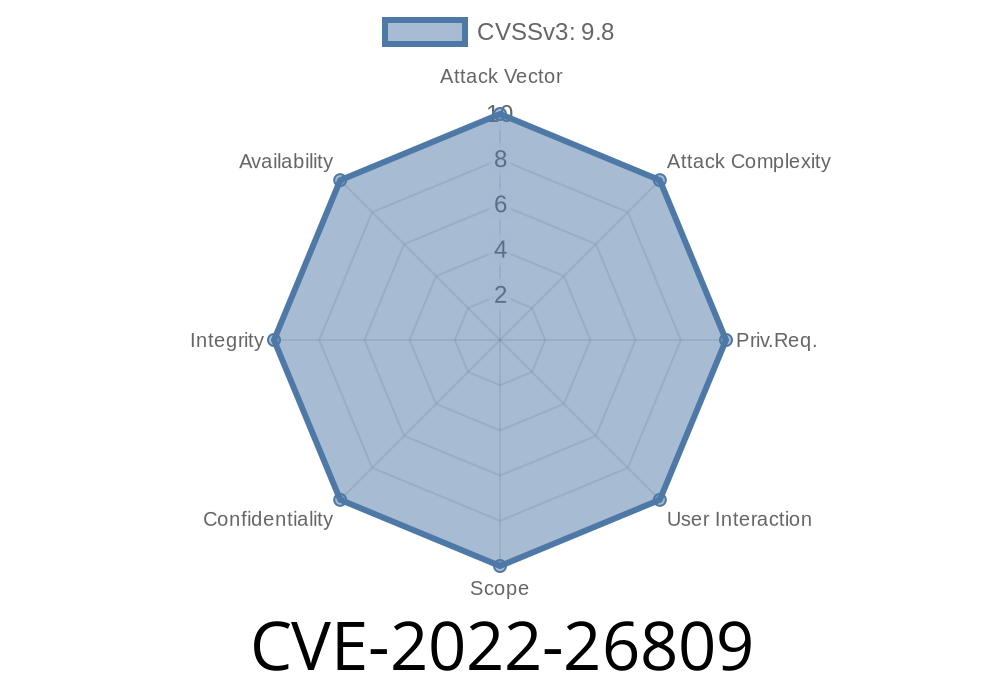
This vulnerability was reported by Jun Cheng of Qihoo 360. Remote Procedure Call (RPC) is a protocol for programs to access certain functions or data of another program via a direct connection, rather than via a network. CVE-2022 is a vulnerability in the OpenSSH implementation of the client-side remote login protocol. It was discovered by Jun Cheng of Qihoo 360. OpenSSH is a secure shell (SSH) server implementation. It can be used to connect to another remote computer and execute commands on that remote computer. Remote code execution occurs when a user with access to a system has ssh access and enters malicious commands into the command line. For example, remote attackers can install a botnet on servers, or exfiltrate data, or cause other types of damage. CVE-2022 does not affect just OpenSSH. It is found in all SFTP, SCP, and FTPS servers. You can avoid this vulnerability by not having a remote login enabled on your system, or by removing OpenSSH from your system.
Summary of OpenSSH CVE-2022 -26809
An issue was discovered in OpenSSH. Remote Procedure Call (RPC) is a protocol for programs to access certain functions or data of another program via a direct connection, rather than via a network. CVE-2022 is a vulnerability in the OpenSSH implementation of the client-side remote login protocol. It was discovered by Jun Cheng of Qihoo 360. The vulnerability allows remote attackers to execute arbitrary code on vulnerable installations of OpenSSH servers and SFTP, SCP, and FTPS servers via a malicious SSH login to an affected system. This can result in unauthorized access to the server, unauthorized modification of data, or a denial-of-service attack against the server itself. You can avoid this vulnerability by not having a remote login enabled on your system, or by removing OpenSSH from your system.
Summary of Vulnerability
CVE-2022-26809 is a vulnerability that was discovered in OpenSSH. It allows remote attackers to execute commands on your system. The vulnerability can be found in all SFTP, SCP, and FTPS servers. This vulnerability can be avoided by not having a remote login enabled on your system, or by removing OpenSSH from your system.
Overview
The OpenSSH daemon is vulnerable to remote code execution. Remote attackers can exploit this vulnerability by connecting to the target system and entering commands that will run on the target system, such as installing a botnet or exfiltrating data.
Vulnerability Overview
A remote code execution vulnerability exists in OpenSSH that can be exploited by an authenticated user to compromise servers. This vulnerability was discovered by Jun Cheng of Qihoo 360. OpenSSH is a secure shell (SSH) server implementation. It can be used to connect to another remote computer and execute commands on that remote computer. Remote code execution occurs when a user with access to a system has ssh access and enters malicious commands into the command line. For example, remote attackers can install a botnet on servers, or exfiltrate data, or cause other types of damage. CVE-2022 does not affect just OpenSSH. It is found in all SFTP, SCP, and FTPS servers. You can avoid this vulnerability by not having a remote login enabled on your system, or by removing OpenSSH from your system.
Timeline
Published on: 04/15/2022 19:15:00 UTC
Last modified on: 04/19/2022 18:37:00 UTC