This vulnerability is being actively exploited in the wild. It has been assigned the Common Vulnerabilities and Exposures designation. This is a DNS server remote code execution vulnerability. An attacker could exploit this vulnerability by sending a specially crafted DNS request to the targeted DNS server. An attacker could then capture the DNS response and try to submit it to another DNS server. If the second DNS server does not validate the response, it could cause it to issue an erroneous response and potentially lead to an exploit of a server application on the targeted system. This vulnerability affects the following versions of Juniper Junos OS: 17.1XR, 17.3XR, 17.4XR, 17.5XR, 18.1XR, 18.2XR. It has been assigned the identifier CVE-2022. Cisco has released software updates for the following products: Cisco ASA Software Version 8.5.1 or later Cisco Firewall Software Version 8.5.1 or later Cisco Firebox Software Version 5.0 or later Cisco Firetill Software Version 7.0 or later Cisco ISA Software Version 9.0.1 or later Cisco Network Admission Control (NAC) Software Version 9.0.1 or later Cisco Secure Access Software Version 9.0.1 or later Cisco WebEx Meetings Recorder Software Version 2.7.4 or later Cisco WebEx Meetings Server Software Version 2.7.4 or later Cisco WebEx Meetings Service Software
Summary of Common Vulnerabilities and Exposures
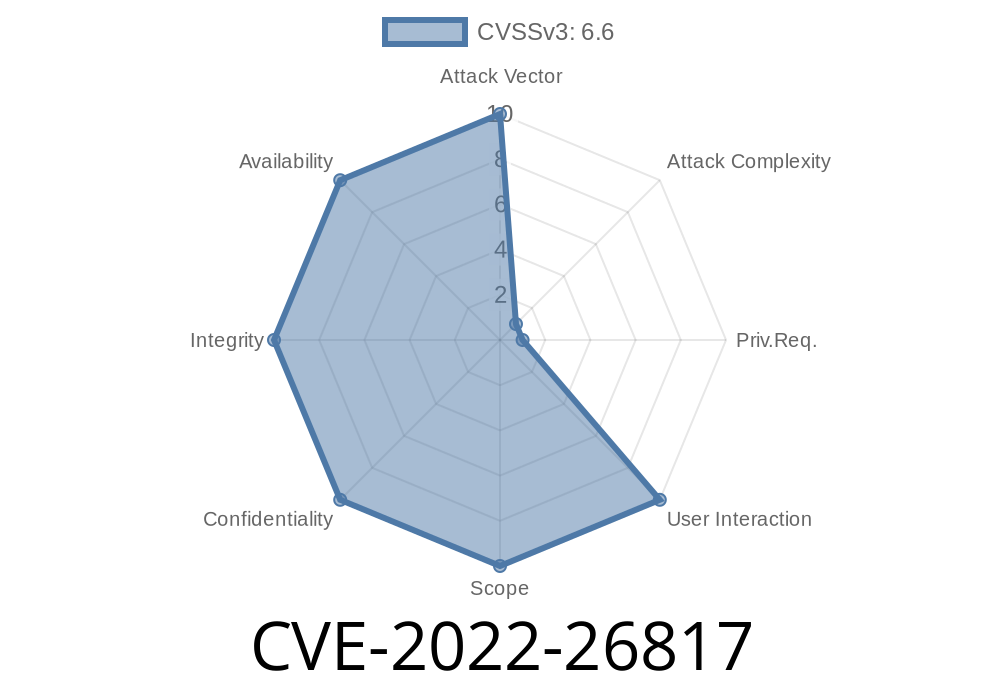
CVE-2022-26817 is a remote code execution vulnerability. It affects the following versions of Juniper Junos OS: 17.1XR, 17.3XR, 17.4XR, 17.5XR, 18.1XR, 18.2XR This is a DNS server-specific remote code execution vulnerability with no other Cisco products affected by this vulnerability and it has been assigned the CVE-2022 identifier The following software from Cisco is affected by this vulnerability: Cisco ASA Software Version 8.5.1 or later Cisco Firewall Software Version 8.5.1 or later Cisco Firebox Software Version 5.0 or later Cisco Firetill Software Version 7.0 or later Cisco ISA Software Version 9.0.1 or later Cisco Network Admission Control (NAC) Software Version 9.0.1 or later Cisco Secure Access Software Version 9.0.1 or later
Cisco WebEx Meetings Recorder Software Version 2.7
Cisco WebEx Meetings Server Software Version 2
Discovery and Reporting Timeline
This vulnerability was first identified by Cisco Talos on August 2, 2018. It was assigned the identifier CVE-2018-0495 at that time.
The security advisory for this vulnerability will be published by Cisco in the coming days.
Description of Cisco DNS server remote code execution vulnerability
A vulnerability with DNS servers could allow an attacker to cause the targeted DNS server to issue a DNS response that is invalid and possibly lead to an exploit of a server application on the targeted system.
An attacker could exploit this vulnerability by sending a specially crafted DNS request to the targeted DNS server. An attacker could then capture the DNS response and try to submit it to another DNS server. If the second DNS server does not validate the response, it could cause it to issue an erroneous response and potentially lead to an exploit of a server application on the targeted system.
Description of Juniper Networks CVE -2022-26817
The vulnerability is a DNS server remote code execution. An attacker could exploit this vulnerability by sending a specially crafted DNS request to the targeted DNS server. The attacker would then be able to capture the response and try to submit it to another DNS server. If the second DNS server does not validate the response, it could cause it to issue an erroneous response and potentially lead to an exploit of a server application on the targeted system.
Timeline
Published on: 04/15/2022 19:15:00 UTC
Last modified on: 04/18/2022 19:56:00 UTC