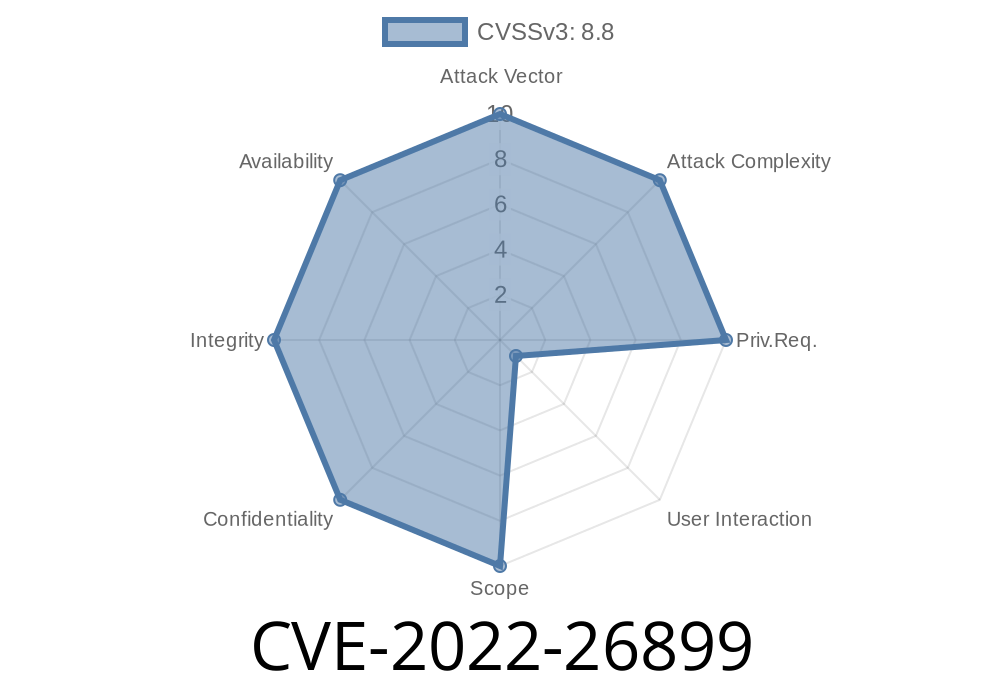
In spring 2022, Microsoft published a security advisory for a new vulnerability discovered in its Chromium-based Edge browser, officially tracked as CVE-2022-26899. This flaw, categorized as an “Elevation of Privilege” issue, created a pathway for attackers to potentially run code or gain privileges they wouldn’t normally have on a target system. Below, we break down what CVE-2022-26899 means, how it works at a technical level, and what you can do about it—including example snippets for those wanting a security deep dive.
What is CVE-2022-26899?
CVE-2022-26899 affects Microsoft Edge that is based on the Chromium project. An attacker could exploit this vulnerability to elevate their privileges—escalating from a restricted context to something far more dangerous, like administrator level.
Official advisory from Microsoft:
Microsoft Security Response Center
Chromium security tracker:
Chromium Issue 1310862
How Does The Vulnerability Work?
The root of CVE-2022-26899 lies in *improper security checks when handling certain operations within Edge's process management code*. If a malicious website is visited, it could potentially trigger behaviors in Edge that cause it to execute code at a higher privilege than intended.
Where is the Problem?
Some browser internals communicate between low-privilege (sandboxed) and high-privilege (broker) processes. There was a logical flaw where user-controlled input wasn’t sanitized properly, allowing attackers to escape the tight security sandbox.
For simplicity, let’s imagine a pseudo-code version of a vulnerable handler
void VulnerableHandler(Message msg) {
if (msg.type == "RunCommand") {
// missing: privilege check!
RunOnHost(msg.command); // Dangerous! Executes on the host.
}
}
A more secure version would double-check the sender’s privilege
void SecureHandler(Message msg) {
if (msg.type == "RunCommand" && msg.sender.IsTrusted()) {
RunOnHost(msg.command);
}
}
Exploit Example: Proof of Concept
Most public exploits involve sending crafted inter-process messages. While the actual exploit code is not released publicly for obvious reasons, here’s a conceptual Python snippet showing how an untrusted "guest" script might try to exploit the flaw (note: for educational purposes and NOT a real exploit):
import socket
def send_malicious_message():
# Connect to Edge's IPC socket (Localhost example, pseudocode)
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect(('127...1', 9222))
payload = {
"type": "RunCommand",
"command": "powershell -Command 'Start-Process calc.exe'"
}
s.send(str(payload).encode())
s.close()
send_malicious_message()
> In reality, the actual exploit would be more complex and browser-specific, but the concept is similar: trick the higher-privilege process into running something dangerous.
Mitigations and Updates
Microsoft responded quickly:
Edge auto-updates for most users, and the vulnerability was patched in Edge version 102..1245.30. To check if you’re protected:
Make sure your version is up-to-date.
More info:
- Microsoft release notes on the bug
- CVE Details
Key Takeaways
- Always keep browsers updated—modern browsers update themselves, so just closing and relaunching Edge is often enough.
Final Words
CVE-2022-26899 mattered because it highlighted the importance of privilege separation in browsers and the risk when it's violated. By understanding how such bugs work, we can better spot them—and defend against them—in the wild.
Timeline
Published on: 06/29/2023 02:15:00 UTC
Last modified on: 07/07/2023 14:25:00 UTC