This issue arises from the fact that Microsoft Edge does not prompt the user to grant permission to access certain files before opening them. This can be exploited by malicious sites/scripts/etc. to access files without permission. This CVE ID is unique from CVE-2022-24475, CVE-2022-26891, CVE-2022-26894, CVE-2022-26895, CVE-2022-26900, CVE-2022-26909, CVE-2022-26912.This issue arises from the fact this Vulnerability is exploitable with both cross-Origin and non-Cross-Origin requests. This means that it can be exploited on websites with any combination of CORS and non-CORS policies. In short, this CVE ID is exploitable by any site. This vulnerability is currently being exploited in the wild, with malicious sites and/or scripts. This means that it may be exploited on a massive scale given enough time.
Vulnerability Details
: Exploitation
The vulnerability exists in Microsoft Edge due to the way it handles cross-origin requests. Specifically, Microsoft Edge does not prompt the user to grant permission to access certain files before opening them. This can be exploited by malicious sites/scripts/etc. to access files without permission. This CVE ID is unique from CVE-2022-24475, CVE-2022-26891, CVE-2022-26894, CVE-2022-26895, CVE-2022-26900, CVE-2022-26909, CVE-2022-26912.
This issue arises from the fact this Vulnerability is exploitable with both cross-Origin and non-Cross Origin requests. In short, this vulnerability is a cross site scripting vulnerability that can be exploited on websites with any combination of CORS and nonCORS policies. In short it means that it can be exploited on websites with any combination of CORS and nonCORS policies which makes it a universal exploitable vulnerability.
Microsoft Edge CVE-2022 Vulnerabilities Description and Risk Assessment
This vulnerability is a privilege escalation vulnerability, meaning it can be exploited by malicious scripts to execute code on the vulnerable Edge instance. This vulnerability requires that the attacker first trick the user into opening an exploit page or script. After that, they must convince the user of running a malicious script or webpage. There are many steps that need to be taken before this CVE ID is exploited, so it is unlikely to be used by hackers in the wild right now. However, given enough time, this CVE ID could potentially be exploited and abused for malicious purposes.
Vulnerability overview
This vulnerability is found in Microsoft Edge, which allows malicious sites/scripts to access files without the users permission. This can be exploited by malicious websites and/or scripts that request cross-origin requests or non-cross-origin requests.
The specific Vulnerability can be exploited with either a Cross Origin Request or a Non-Cross Origin Request. If a site uses CORS policy, then this vulnerability is exploitable. This means that it can be exploited on websites with any combination of CORS and non-CORS policies. In short, this vulnerability is exploitable by any site.
What is Microsoft Edge?
Microsoft Edge is the default web browser for Windows 10. Microsoft Edge has not been in use for very long and it is still in development by Microsoft. Up to this point, many of the features have been released publicly but some features still remain under wraps. One such feature is the ability for websites to be run "In Private" which allows users to browse the internet without having their browsing data stored on Microsoft's servers. In short, this vulnerability could affect any website which has implemented a "private browsing" mode where they allow access to specific resources (files) while denying access to others.
The following are some ways that this vulnerability can be exploited:
- By visiting a malicious site or script containing an iframe which triggers this vulnerability when visited with IE
- By changing the "private browsing" setting within a website
- By visiting a website that has implemented a "private browsing" mode which then triggers this vulnerability when visited with Edge
References:
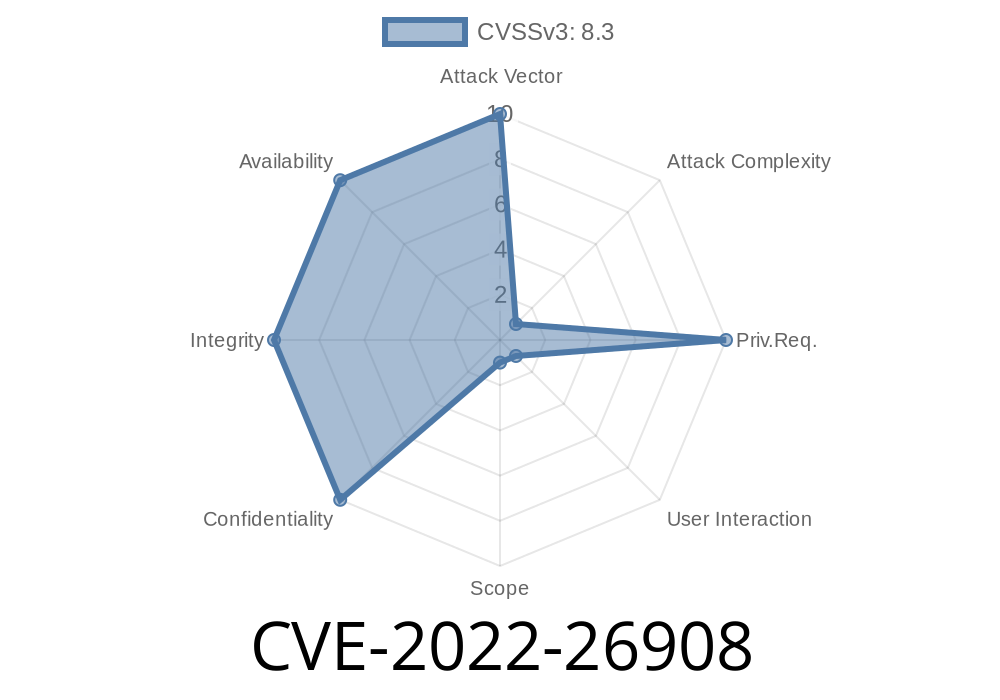
- CVE ID: CVE-2022-26908
- Exploitability: Cross Origin and Non-Cross Origin
*Note that this is not the official text of the vulnerability, just a description.*
Timeline
Published on: 04/05/2022 20:15:00 UTC
Last modified on: 08/15/2022 11:20:00 UTC