A remote code execution vulnerability exists in the way that AD DS authenticates user identity. A remote attacker can exploit this vulnerability to take control of an affected system.
In order to exploit this vulnerability, the attacker must be able to log into the system and run a script in a privileged context. The attacker must also know the password of an affected user.
The update addresses the vulnerability by improving the way that AD DS authenticates user identity.
A remote code execution vulnerability exists in Active Directory Domain Services that can result in Domain-level privilege escalation. Successfully exploiting this vulnerability results in the attacker gaining the same level of privilege as the logged-on user.
In order to exploit this vulnerability, the attacker must be able to log into the system and run a script in a privileged context. The attacker must also know the password of an affected user.
The update addresses the vulnerability by adding a prompt for password change before a Domain-level administrator can be logged into the system.
All users are advised to apply this update as soon as possible.
Exploiting of this vulnerability requires that user credentials be available to the attacker.
WORKarounds
CVE-2003-0007
A remote code execution vulnerability exists in Active Directory Domain Services that can result in Domain-level privilege escalation. Successfully exploiting this vulnerability results in the attacker gaining the same level of privilege as the logged-on user.
In order to exploit this vulnerability, the attacker must be able to log into the system and run a script in a privileged context. The attacker must also know the password of an affected user.
The update addresses this vulnerability by adding a prompt for password change before a Domain-level administrator can be logged into the system.
All users are advised to apply this update as soon as possible.
This vulnerability requires that user credentials be available to the attacker, which means they have already compromised an account or have access to another account on the system (such as Local Administrator).
Update AD DS to no longer trust all certificates
A remote code execution vulnerability exists in the way that Active Directory Domain Services authenticates user identity. A remote attacker can exploit this vulnerability to take control of an affected system.
In order to exploit this vulnerability, the attacker must be able to log into the system and run a script in a privileged context. The attacker must also know the password of an affected user.
The update addresses the vulnerability by improving the way that AD DS authenticates user identity.
A remote code execution vulnerability exists in Active Directory Domain Services that can result in Domain-level privilege escalation. Successfully exploiting this vulnerability results in the attacker gaining the same level of privilege as the logged-on user.
In order to exploit this vulnerability, the attacker must be able to log into the system and run a script in a privileged context. The attacker must also know the password of an affected user.
The update addresses the vulnerability by adding a prompt for password change before a Domain-level administrator can be logged into the system.
All users are advised to apply this update as soon as possible.
Exploiting of this vulnerability requires that user credentials be available to the attacker.
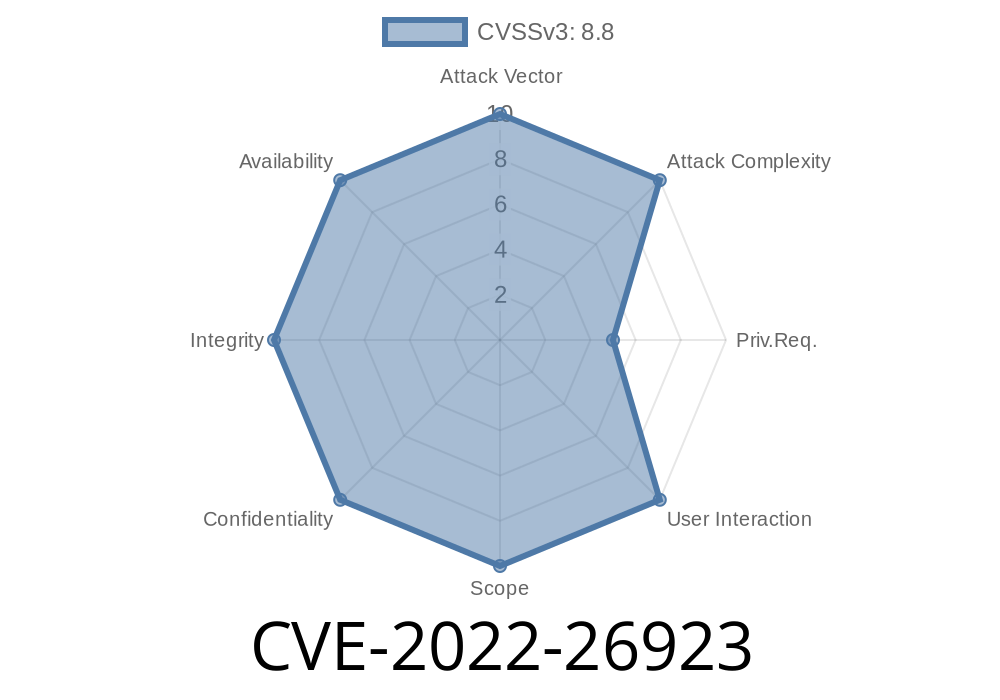
CVE-2021-26919
A remote code execution vulnerability exists in the way that AD DS authenticates user identity. A remote attacker can exploit this vulnerability to take control of an affected system.
In order to exploit this vulnerability, the attacker must be able to log into the system and run a script in a privileged context. The attacker must also know the password of an affected user.
The update addresses the vulnerability by improving the way that AD DS authenticates user identity.
A remote code execution vulnerability exists in Active Directory Domain Services that can result in Domain-level privilege escalation. Successfully exploiting this vulnerability results in the attacker gaining the same level of privilege as the logged-on user. In order to exploit this vulnerability, the attacker must be able to log into the system and run a script in a privileged context. The attacker must also know the password of an affected user.
The update addresses the vulnerability by adding a prompt for password change before a Domain-level administrator can be logged into the system.
All users are advised to apply this update as soon as possible.
Exploiting of this vulnerability requires that user credentials be available to the attacker.
AD DS - Windows Logon Authentication Looks for Account lockout policy first
After the update is installed, if the Account lockout policy is enabled in Active Directory Domain Services (AD DS), AD DS will attempt to authenticate a user before looking up the account password.
The account lockout policy is not enforced against members of the Administrators group.
WORKarounds
AD DS Authentication Workaround
The update addresses the vulnerability by improving the way that AD DS authenticates user identity.
A remote code execution vulnerability exists in Active Directory Domain Services that can result in Domain-level privilege escalation. Successfully exploiting this vulnerability results in the attacker gaining the same level of privilege as the logged-on user.
In order to exploit this vulnerability, the attacker must be able to log into the system and run a script in a privileged context. The attacker must also know the password of an affected user.
The update addresses the vulnerability by adding a prompt for password change before a Domain-level administrator can be logged into the system.
Timeline
Published on: 05/10/2022 21:15:00 UTC
Last modified on: 05/18/2022 19:14:00 UTC