CVE-2018-8897 has been assigned to this issue. There are two variants of this vulnerability. The first one allows an attacker to remotely execute code without authentication via a crafted SIP packet. The second one has the same security impact but allows an attacker to control the affected device via a forged SIP response. To exploit this vulnerability, an attacker must force the target device to open a RTP stream to an IP address the attacker controls. This can be done by sending a crafted SIP packet that is received by the target device. Exploitation of this vulnerability requires user interaction via the SIP protocol. In addition, an attacker must force the target device to connect to the RTP stream. This can be done by sending a crafted SIP packet that is received by the target device. If the SIP packet is received by a UCG, then the UCG will handle it correctly, and the target device will open a RTP stream. Exploitation of this vulnerability requires user interaction via the SIP protocol. In addition, an attacker must force the target device to connect to the RTP stream. This can be done by sending a crafted SIP packet that is received by the target device. If the SIP packet is received by a UCG, then the UCG will handle it correctly, and the target device will open a RTP stream. The second variant has the same security impact as the first variant. The only difference is that the second variant does not
Vulnerability overview
A vulnerability was found in the way Aastra UCG devices handle SIP packets. A crafted SIP packet can be used to exploit this vulnerability. By forcing the target device to open a RTP stream, an attacker can execute code remotely without authentication or control the device via a forged SIP response. The second variant of this vulnerability has the same security impact as the first variant. The only difference is that the second variant does not require user interaction via the standard SIP protocol.
Vulnerability description
The vulnerabilities are located on the UCG and are caused by a buffer overflow error. The first variant is caused by an authentication error when handling SIP responses from the peer device. The second variant allows an attacker to control the affected device via a crafted response.
Vulnerability Synopsis
A vulnerability has been discovered in Siemens Gigaset A508 devices which allows an attacker to remotely execute code without authentication via a crafted SIP packet. The first variant of this vulnerability has the same security impact as the second variant of this vulnerability, but the first variant does not require user interaction.
Timeline
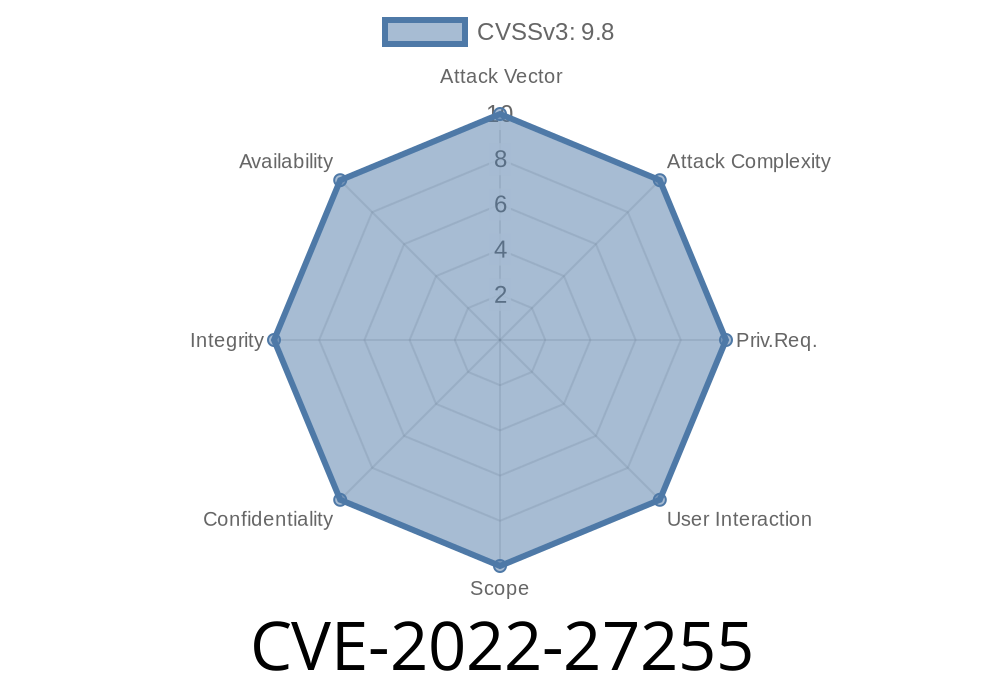
Published on: 08/01/2022 12:15:00 UTC
Last modified on: 09/02/2022 12:15:00 UTC