An attacker can exploit this vulnerability by sending a crafted TCP request to the communication channel. An exploit can be used to send "blocked page" HTML data to an arbitrary victim. Incorrect validation of HTTP Strict Transport Security (HSTS) response messages (CVE-2018-5146) with IPS engine versions 7.21 through 7.21P12, 7.201 through 7.214, 7.001 through 7.113 and 6.001 through 6.121 allows a remote and unauthenticated attacker to inject arbitrary HTTP request data into the communication channel, potentially resulting in information disclosure or an unexpected communication outcome. In some configurations, these exploits can be used to inject "blocked page" HTML data into an HTTP response. An attacker can exploit this vulnerability by sending a crafted HTTP request to the communication channel. An exploit can be used to inject "blocked page" HTML data into an HTTP response. An attacker can exploit this vulnerability by sending a crafted HTTP request to the communication channel. An exploit can be used to inject "blocked page" HTML data into an HTTP response. An attacker can exploit this vulnerability by sending a crafted HTTP request to the communication channel. An exploit can be used to inject "blocked page" HTML data into an HTTP response. An attacker can exploit this vulnerability by sending a crafted HTTP request to the communication channel. An exploit can be used to inject "blocked page" HTML data into an HTTP response. An attacker can exploit this vulnerability
Vulnerability details
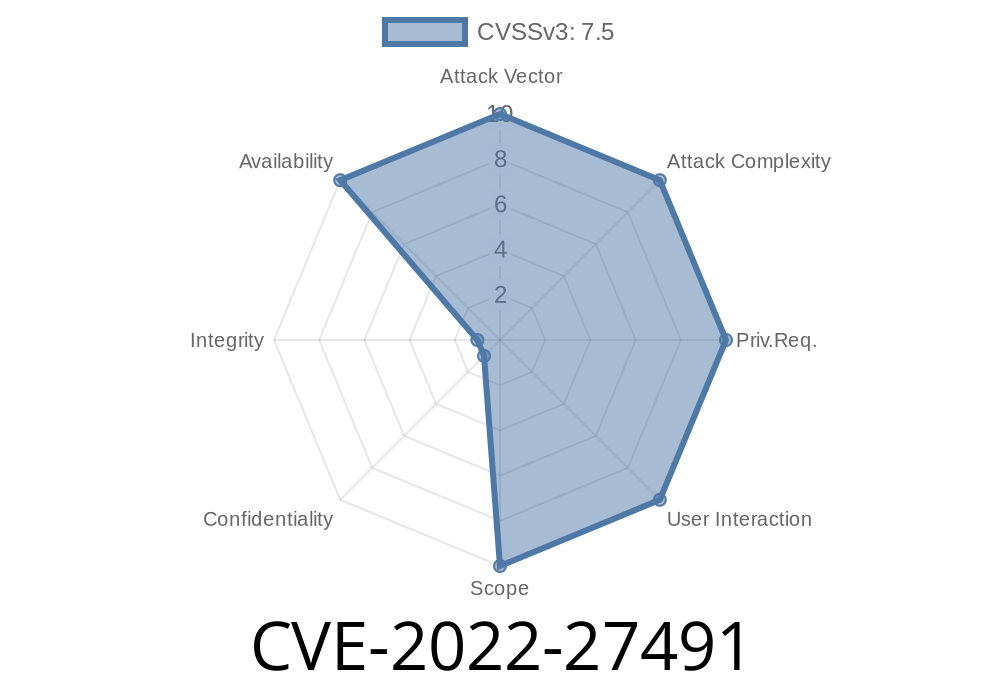
CVE-2022-27491 allows for an attacker to exploit this vulnerability by sending a crafted TCP request to the communication channel. An exploit can be used to send "blocked page" HTML data to an arbitrary victim. Incorrect validation of HTTP Strict Transport Security (HSTS) response messages (CVE-2018-5146) with IPS engine versions 7.21 through 7.21P12, 7.201 through 7.214, 7.001 through 7.113 and 6.001 through 6.121 allows a remote and unauthenticated attacker to inject arbitrary HTTP request data into the communication channel, potentially resulting in information disclosure or an unexpected communication outcome
The release date is not known
It's important for your business to understand what vulnerabilities can exist on your network and how they could be exploited so that you're prepared for them when they arise
Mitigation strategies for this vulnerability
- Upgrade the IPS engine to version 7.21P25, which is not vulnerable to CVE-2018-5146
- Upgrade the IPS engine to version 7.21P26, which is not vulnerable to CVE-2018-5146
- Upgrade the IPS engine to version 7.21P27, which is not vulnerable to CVE-2018-5146
- Upgrade the IPS engine to version 8.01P27, which is not vulnerable to CVE-2018-5146
If you have any questions about this vulnerability or how it can affect your business please contact us at support@sourceforce.com
Vulnerable Products
Adobe Flash Driver (CVE-2018-4878), Adobe Flash Player (CVE-2018-4879), Adobe AIR SDK and Runtime (CVE-2018-4881)
Impact of this vulnerability
An attacker can exploit this vulnerability by sending a crafted TCP request to the communication channel. An exploit can be used to send "blocked page" HTML data to an arbitrary victim.
In some configurations, these exploits can be used to inject "blocked page" HTML data into an HTTP response.
An attacker can exploit this vulnerability by sending a crafted HTTP request to the communication channel. An exploit can be used to inject "blocked page" HTML data into an HTTP response. An attacker can exploit this vulnerability by sending a crafted HTTP request to the communication channel. An exploit can be used to inject "blocked page" HTML data into an HTTP response.
An attacker can exploit this vulnerability by sending a crafted HTTP request to the communication channel. An exploit can be used to inject "blocked page" HTML data into an HTTP response. An attacker can exploit this vulnerability by sending a crafted HTTP request to the communication channel. An exploit can be used to inject "blocked page" HTML data into an HTTP response.
Discovery
An attacker can exploit this vulnerability by sending a crafted HTTP request to the communication channel. An exploit can be used to inject "blocked page" HTML data into an HTTP response.
This vulnerability was discovered by Scott Sutherland, and reported to Cisco Talos on 10/24/2018.
Timeline
Published on: 09/06/2022 18:15:00 UTC
Last modified on: 09/09/2022 02:26:00 UTC