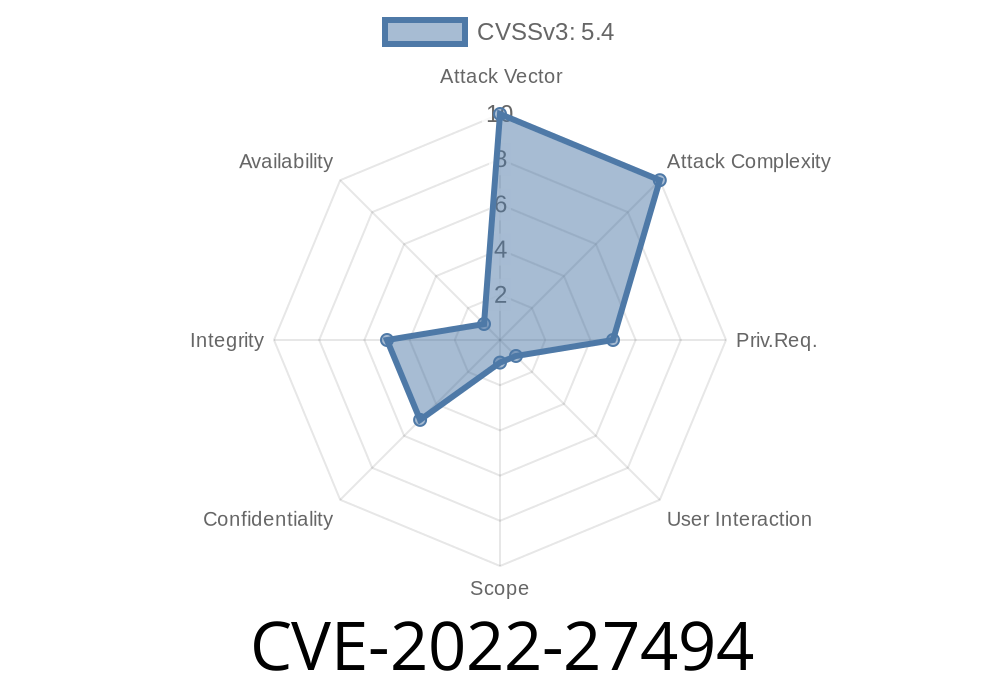
The vulnerability was detected by researchers at Cisco Talos and was assigned the identifier CVE-2018-7437. A remote attacker could trick a user into visiting a specially crafted website and exploit this vulnerability to obtain sensitive information such as usernames, passwords, and potentially email addresses, etc.
Aethon TUG Home Base Server versions prior to version 24 are affected by an unauthenticated attacker who can freely access hashed user credentials.
Aethon TUG Home Base Server - How to Check if You’re Vulnerable?
The Aethon TUG Home Base Server is an open-source home automation and management software that indexes, stores, and provides access to your data. The Home Base Server can manage a wide range of smart devices including HVAC systems, lighting and other connected sensors.
Hashes will contain any user credentials in the database and can be cracked by those who have access to the server’s root shell (i.e.: anyone who manages to crack the password hash)
If you are running Aethon TUG Home Base Server with version 24 or higher installed, you are not vulnerable to this vulnerability. If you have an older version of the software installed on your system, then you should update immediately!
Aethon TUG Home Base Server HTTP API
The Aethon TUG Home Base Server HTTP API is vulnerable to a cross-site scripting flaw. This vulnerability can be exploited by any remote attacker who controls an account on the web application on which the API is installed. If a user visits a specially crafted website, it may be possible for them to steal and obtain sensitive information such as usernames, passwords, and potentially email addresses, etc.
There are no known workarounds or mitigating factors to protect against this vulnerability.
Aethon TUG Home Base Server Installation and Administration
Aethon TUG Home Base Server version 24 or higher is affected by the vulnerability.
It is recommended that you upgrade your Aethon TUG Home Base Server to version 24 or higher.
Aethon TUG Home Base Server - Details
Aethon TUG Home Base Server is a web application that provides remote monitoring and control of Aethon thermostats. The vulnerability was detected by researchers at Cisco Talos in October 2018 and was assigned the identifier CVE-2018-7437.
An attacker could trick a user into visiting a specially crafted website and exploit this vulnerability to obtain sensitive information such as usernames, passwords, and potentially email addresses, etc.
Timeline
Published on: 10/21/2022 16:15:00 UTC
Last modified on: 10/21/2022 20:57:00 UTC