The attacker may also have the capability to reset the password and login to the device via Telnet/SSH, escalate privileges, or install a new operating system with root access.
An attacker may be able to obtain ssh or telnet access to a device via a man-in-the-middle attack, or via ssh brute-forcing of the password.
Impact of MitM: An attacker may be able to obtain administrative access to the device, install a new operating system with root access, or reset the administrator password.
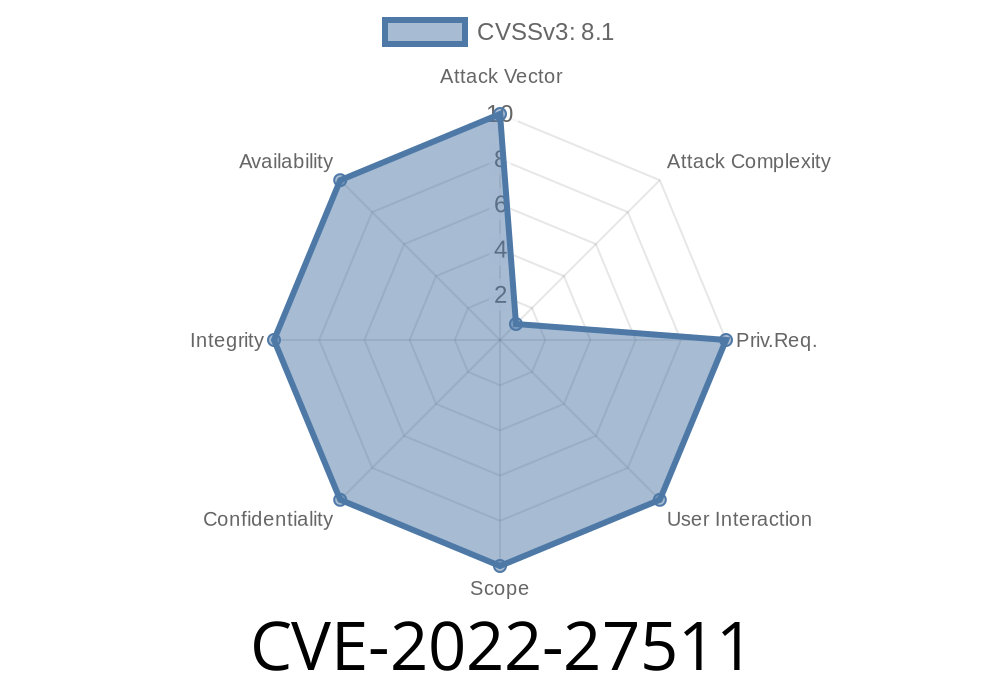
CVE-IDs: CVE-2017-9524, CVE-2017-9525, CVE-2017-9526, CVE-2017-9527, CVE-2017-9528, CVE-2017-9529, CVE-2017-9530, CVE-2017-9531, CVE-2017-9532, CVE-2017-9533, CVE-2017-9534, CVE-2017-9535, CVE-2017-9536, CVE-2017-9537, CVE-2017-9538, CVE-2017-9539, CVE-2017-9540, CVE-2017-9541, CVE-2017-9542, CVE-2017-9543, CVE-2017-9544, CVE-2017-9545, CVE-2017-9546, CVE-2017-9547, CVE-2017-9548, CVE-2017-9549, CVE-
Potential Improvements
One security improvement is to implement SSH authentication, ensuring that only the person who has been authorized gains access.
Another potential improvement is to use key authentication, where a user must provide their password but also a key in order to gain access.
Mitigation Strategies
Mitigating the impact of a MitM attack is a difficult situation. The following methods can be used:
- Restrict Telnet or SSH access to first-level administrators or root users only.
- Use strong passwords and ensure that they are hard to crack.
- Enable MAC filtering on the device's firewall.
Authentication Fails: Implications for Build Security
Authentication fails on a system with no known vulnerability:
Impact of Authentication Fails:
- You may have to provide the same credentials again, which will cause confusion.
Timeline
Published on: 06/16/2022 19:15:00 UTC
Last modified on: 06/16/2022 21:57:00 UTC