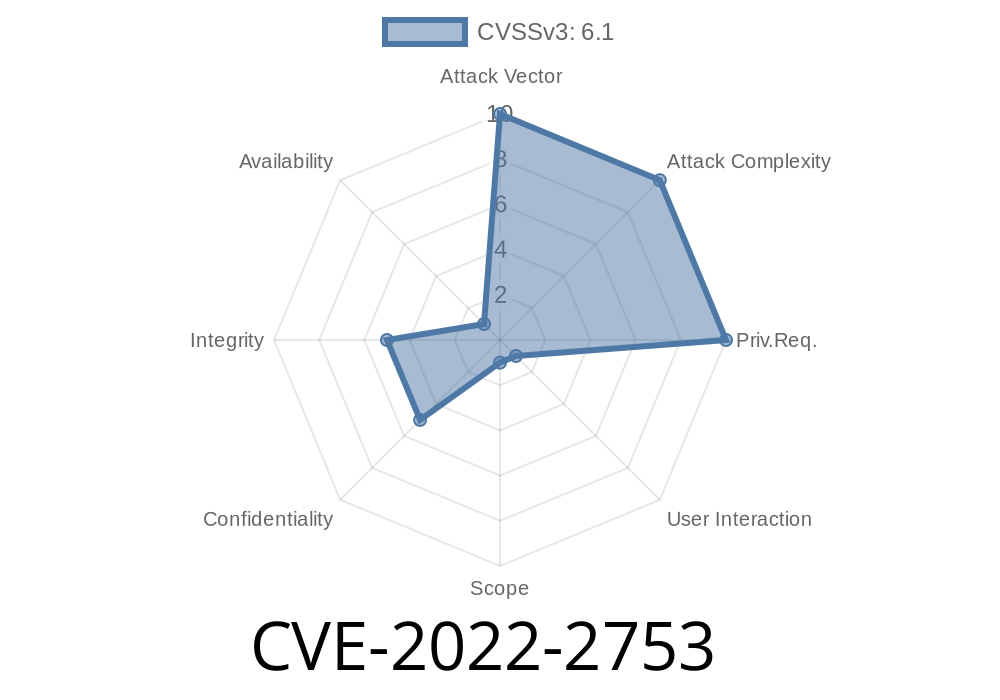
by a client. An attacker can leverage a XSS flaw to execute arbitrary code in the web application. This plugin version is 3.2.0 and above. If you have installed version 3.2.0 or above of this plugin, it’s recommended to update it as soon as possible. By installing this plugin you accept risk of attackers injecting malicious code via XSS flaws. This plugin does not restrict user input length, does not validate user input, and uses an unsafe method to sanitise user input. In short, it is recommended to avoid this plugin version.
Description
A vulnerability in a third-party plugin has been discovered. So, if you are using this plugin, please update it as soon as possible.
How do I know if my website is vulnerable?
If you see this message in your browser's address bar, then it is likely that your website is vulnerable to this vulnerability. If you need help identifying what plugin version you have installed, please contact our support team.
Versions Affected 3.1.6
3.2.0
What is XSS?
Cross-site scripting (XSS) is an attack that allows a malicious user to inject client-side scripts into a web application. XSS flaws can be found in areas such as Web forms and HTML attributes. The vulnerability occurs when output from one part of a website is used where it wasn’t intended, for example, using the input box in a form for an email address.
Timeline
Published on: 09/19/2022 14:15:00 UTC
Last modified on: 09/21/2022 06:27:00 UTC