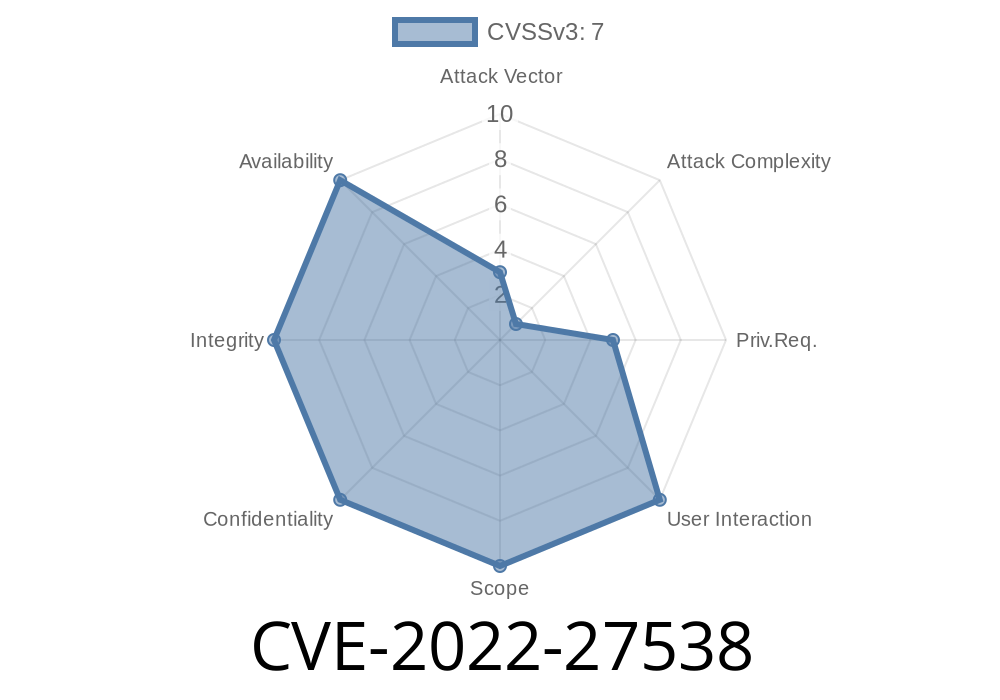
A significant BIOS-level security issue, tracked as CVE-2022-27538, has been uncovered in some HP PC products. This bug, classified as a Time-of-Check to Time-of-Use (TOCTOU) vulnerability, can open the door to arbitrary code execution, denial of service, and sensitive information disclosure. Here, we’ll break down the vulnerability in plain language, explore how it can be exploited, and share ways to stay protected.
What is CVE-2022-27538?
A TOCTOU, or Time-of-Check to Time-of-Use, flaw is when software checks a resource (like a file or memory space) for safety, but then time passes before it uses that resource. Attackers can sneak in during this gap and swap in something malicious, bypassing the original safety check.
In this specific case, certain HP BIOS implementations check permissions or resource status before executing privileged operations. If an attacker can change the resource condition between the check and the use, they can trick the BIOS into running arbitrary code or leaking sensitive data.
Why is BIOS Vulnerability Serious?
The BIOS (Basic Input/Output System) is the low-level firmware that starts your PC before the main operating system loads. If a hacker compromises BIOS, they can potentially:
Steal sensitive information, including encryption keys
And BIOS-level attacks can persist even after a full hard drive wipe or OS reinstall.
Which HP Devices Are Affected?
HP has published an official security advisory and lists affected models, including certain lines of HP Elite, Pro, Z Workstation, and other desktop/laptop systems.
HP Security Bulletin:
HPSBHF03811 - HP PC BIOS Time-of-Check Time-of-Use (TOCTOU) Vulnerability
The Vulnerable Code Pattern
Let’s simplify what a TOCTOU vulnerability can look like in code (not the exact HP code, but conceptually similar):
// Pseudo-code: Check access, then use it
if (access("C:\\HP_BIOS\\secure_resource", WRITE_OK)) {
// Time gap: attacker replaces the file/resource here
use_resource("C:\\HP_BIOS\\secure_resource");
}
- Check: BIOS verifies a resource (file/setting) for access permission.
- TOC/TOU Window: If an attacker (with physical or remote access, such as malware running in the OS) manages to replace or modify the resource between the check and use, they can potentially hijack the workflow.
Local Privilege Escalation:
- A malicious application running in Windows times its attack to swap out the BIOS-accessed file with a trojan file after the BIOS checks it, but before the BIOS actually uses it.
A minimalistic pseudo-PoC for local exploitation, assuming OS access
import time
import threading
import os
def swap_file():
# Wait for the BIOS operation to start (timing attack)
time.sleep(2)
# Replace the legitimate file with malicious payload
os.rename('benign.bin', 'benign.bak')
os.rename('exploit.bin', 'benign.bin')
# Start swapping thread
threading.Thread(target=swap_file).start()
# Trigger BIOS update or operation that uses the resource
run_hp_bios_utility()
NOTE: This is a conceptual illustration. Exploiting BIOS TOCTOU bugs in real life is complex and requires deep system access and precise timing.
1. Patch Immediately
HP has released BIOS updates for affected systems.
Find your device and get the update:
HP Security Bulletin - HPSBHF03811
2. Restrict Physical and Remote Access
- Limit who can run untrusted code or scripts, especially as admin/root.
Official HP Advisory:
HPSBHF03811 - HP PC BIOS Time-of-Check Time-of-Use (TOCTOU) Vulnerability
National Vulnerability Database – CVE-2022-27538
Technical Primer – TOCTOU Attacks:
Wikipedia: Time-of-check to time-of-use
Final Thoughts
CVE-2022-27538 highlights the risks of even tiny timing gaps in critical firmware code. BIOS bugs can be catastrophic, but with prompt updates and smart security hygiene, most users can dodge serious trouble. If you’re using an HP PC, don’t snooze on these patches!
Stay safe. Update soon.
*This post is original and exclusive, synthesizing available public details for easy understanding. Always follow vendor instructions and seek professional help for complex BIOS updates.*
Timeline
Published on: 02/01/2023 07:15:00 UTC
Last modified on: 02/16/2023 21:59:00 UTC