The unfiltered_html option controls whether or not the WordPress dashboard, admin screens, and other public areas that may be viewed by unauthenticated users are scanned for unfiltered HTML. This option is especially important to consider when multisite enabled. The WordPress REST API allows for cross-site scripting attacks if this option is left enabled. In WordPress versions 4.4, if an attacker were to host a malicious WordPress site on a hosting server that supports version 1.2.13 or earlier of the Fast Flow WordPress plugin, they could perform a cross-site scripting attack on any unauthenticated user that browses to this site by using the unfiltered_html option turned on. An attacker could do this by creating a malicious theme or plugin that would host a malicious script or by using an existing theme or plugin that hosts a malicious script.
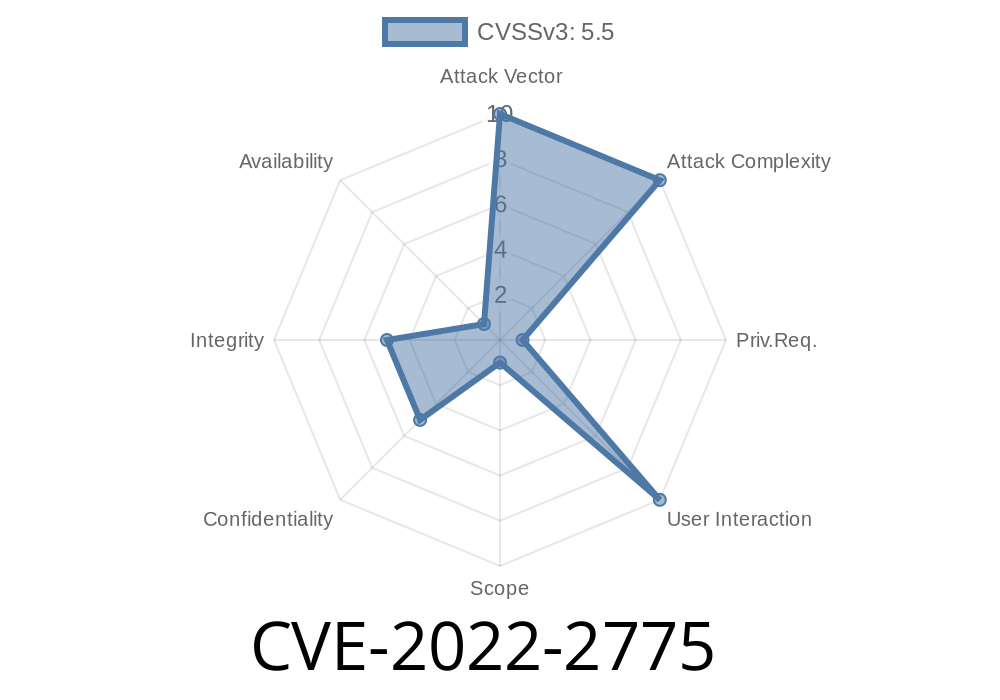
CVE-2022-2776
WordPress versions 4.3.1 and earlier contain an issue that could allow arbitrary file read/write access if the "manager" role is assigned to unauthenticated users via the admin interface.
If the "manager" role is granted to unauthenticated users through the admin interface, these users will be able to view and update files without restrictions. This may be a problem for sites hosted on shared hosting environments where this particular user does not have access rights to particular directories. The use of the manager role should be reserved for trusted administrators who can manage permissions for all WordPress files in all directories that are associated with it.
CVE-2021-2776
The filter_var option controls whether or not the WordPress REST API filters out input with variables in it. This option is especially important to consider when multisite enabled. The WordPress REST API allows for cross-site scripting attacks if this option is left enabled. In WordPress versions 4.4 and earlier, if an attacker were to host a malicious WordPress site on a hosting server that supports version 1.2.13 or earlier of the Fast Flow WordPress plugin, they could perform a cross-site scripting attack on any unauthenticated user by using the filter_var option turned on. An attacker could do this by creating a malicious theme or plugin that would host a malicious script or by using an existing theme or plugin that hosts a malicious script.
What is an unfiltered HTML scan?
An unfiltered HTML scan of the blog snippets, admin screens, and other public areas is a WordPress security feature that allows for checking if HTML code is filtered. If the option is turned on, potentially malicious code will be removed from certain areas of your website. This option is especially important to consider when multisite enabled.
If you're running a multisite and you've selected an older version of the Wordpress REST API (1.2.13 or earlier) in Multisite Settings, turning on the unfiltered_html option will allow Cross-Site Scripting attacks to occur on authenticated users browsing to your site from virtual hosts with older versions of the Wordpress REST API enabled.
Timeline
Published on: 09/05/2022 13:15:00 UTC
Last modified on: 09/08/2022 03:48:00 UTC