This resulted in connections that might have been explicitly closed
because of changes in configuration being kept in the connection pool.
Impact: A malicious or misinformed server application could
utilize this flaw to launch a series of denial-of-service (DoS)
attacks on a libcurl-using server.
Now updated to version 7.56.3, libcurl has been patched to
avoid connection reuse by erasing connections that match an
unexpected server configuration.
Exploitability: This problem affects TLS and SSH connections and thus
affects only servers that provide these services. Servers using these
protocols are extremely rare.
Red Hat recommends updating your libcurl packages as soon as
possible. To update libcurl, run the following command on the Red
Hat Enterprise Linux system where you run libcurl:
Red Hat recommends updating your libcurl packages as soon as possible. To update libcurl, run the following command on the Red Hat Enterprise Linux system where you run libcurl:
Red Hat recommends updating your libcurl packages as soon as possible. To update libcurl, run the following command on the Red Hat Enterprise Linux system where you run libcurl:
Red Hat recommends updating your libcurl packages as soon as possible. To update libcurl, run the following command on the Red Hat Enterprise Linux system where
Overview: libcurl URL Resolver Denial of Service Vulnerability
The curl package provides a library called libcurl that can be used to perform many types of network transfer tasks. A denial-of-service (DoS) vulnerability was found in the libcurl URL resolver due to its use of incorrectly closed connections after configuration changes. This resulted in connections that might have been explicitly closed because of changes in configuration being kept in the connection pool.
Exploitability: This problem affects TLS and SSH connections and thus affects only servers that provide these services. Servers using these protocols are extremely rare.
Red Hat recommends updating your libcurl packages as soon as possible. To update libcurl, run the following command on the Red Hat Enterprise Linux system where you run libcurl:
TL;DR: libcurl updated to version 7.56.3 and TLS protocol versions
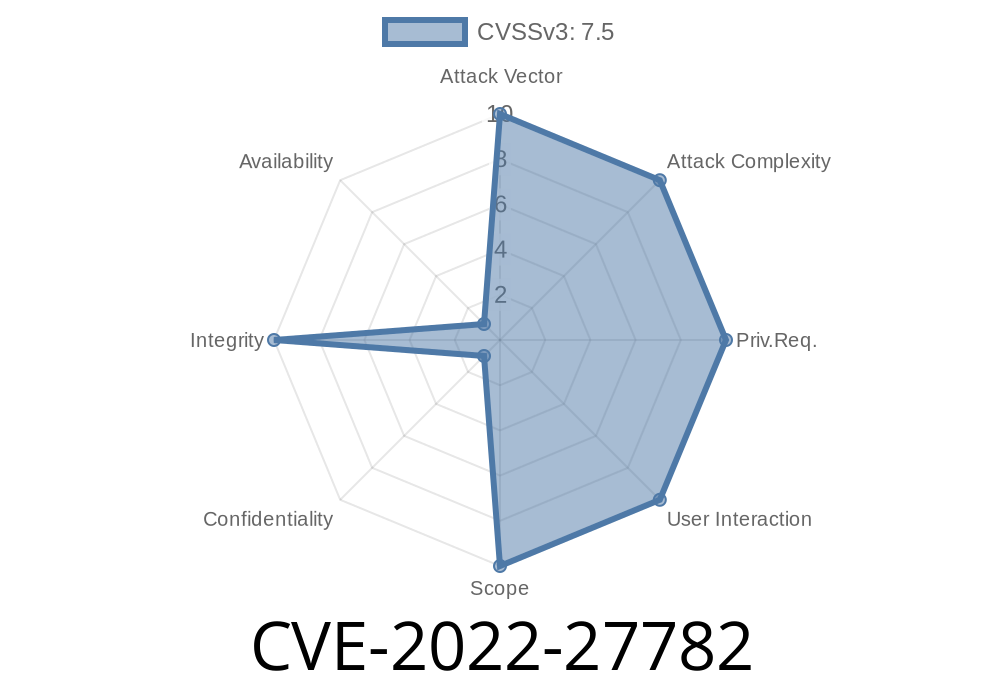
The flaw, CVE-2022-27782, was discovered by security researcher
Merijn Bellekom. The vulnerability could have been used by a malicious
or misinformed server application to launch a series of denial-of-service
(DoS) attacks on a libcurl-using server. This flaw is known as
connection reuse because the code can re-use connections that it
might have explicitly closed due to configuration changes in order to keep in the connection pool. These connections might be reused while they are still valid, which makes them more likely to be successfully exploited. Additionally, the vulnerability causes an endless loop in libcurl's TLS client when the server sends an unexpected TLS key exchange message and then closes the connection without sending back any data.
Overview of libcurl vulnerability
Red Hat recommends updating your libcurl packages as soon as possible. To update libcurl, run the following command on the Red Hat Enterprise Linux system where you run libcurl:
rpm --import https://www.redhat.com/security/data/cve/CVE-2022-27782.asc
rpm -ivh curl-7.56.3-1.el6_7.src.rpm
Concerns with TLS and SSH connections
The first concern is that the flaw could be exploited by a malicious server application. The second concern is that this problem affects only servers that provide TLS and SSH connections, and these protocols are extremely rare. As a result, this vulnerability affects only servers that provide these services.
Timeline
Published on: 06/02/2022 14:15:00 UTC
Last modified on: 08/29/2022 01:15:00 UTC