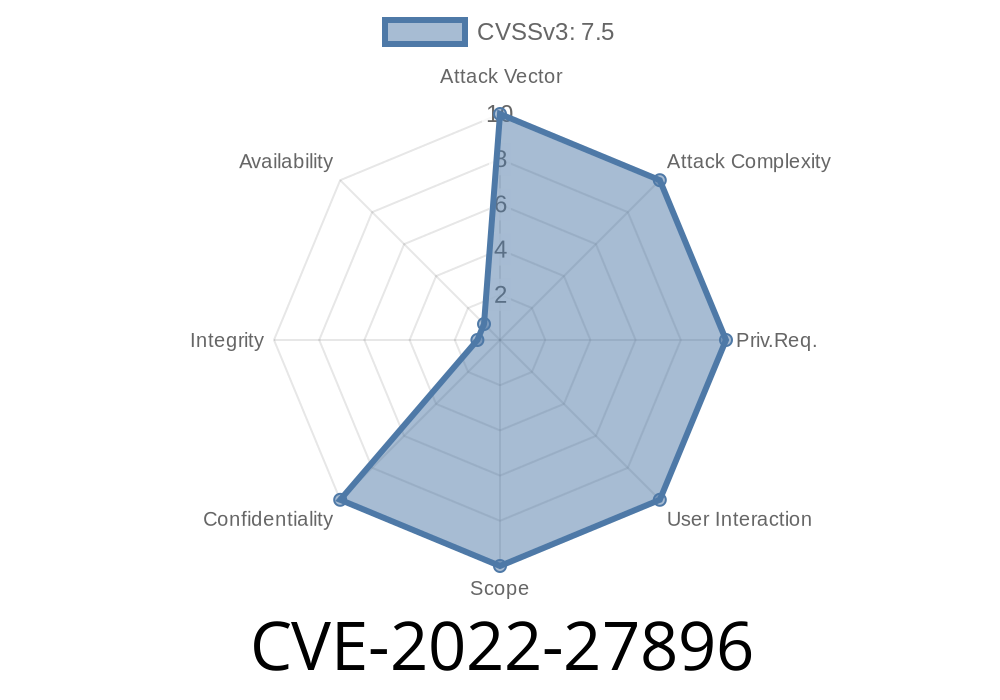
Summary:
CVE-2022-27896 points to a serious vulnerability that exposed sensitive authentication tokens in the log files of Palantir Foundry Code-Workbooks. This shortcoming potentially gave threat actors access to user sessions by leaking tokens in logs, thus endangering the security posture of data analytics environments using this product. Below, we break down the details behind this vulnerability, show example code paths, and provide guidance on mitigation. This explanation is customized for technical readers, security analysts, and Foundry admins.
What Is CVE-2022-27896?
CVE-2022-27896 is an "Information Exposure Through Log Files" flaw in Palantir Foundry Code-Workbooks.
Between versions 4.144 and 4.460. (inclusive), a backend service endpoint that executes Python code for Code-Workbooks was logging user code, and crucially, including the Foundry authentication token in the service logs. These tokens are essentially a user's passkey in the platform, meaning anyone with log access could potentially hijack sessions or gain unauthorized access to sensitive data.
Privileged users could have their tokens captured just by running valid code.
- Anyone with log file access (admins, developers, attackers post-breach) can extract and abuse actual user tokens.
- This is an example of how insecure logging can become a lateral movement vector within corporate environments.
How Did The Vulnerability Occur?
For debugging and auditing, Foundry Code-Workbooks' backend service logged the input Python code and associated metadata with every code execution call. Inadvertently, these logs included the full Authorization Bearer Token that represents the user's session.
Example Snippet (Not actual source, but representative)
# (Simplified example from a Python Flask-like pseudocode)
import logging
from flask import request
def execute_code():
code = request.json.get('code')
token = request.headers.get('Authorization') # Example: 'Bearer eyJ...'
# Insecure logging of both code and token!
logging.info(f"Code execution request: code={code}, auth={token}")
# ... execute 'code' with proper authentication
return {"status": "success"}
`bash
curl -H "Authorization: Bearer eyJe..." https://foundry.company.com/api/some_endpoint
Exploit Details
An attacker does not need client-side access; just access to the logs in the backend or wherever logs are sent (e.g., SIEMs, log aggregators, backups).
Note: The actual vulnerability is not a code injection bug, but an information disclosure caused by careless logging.
In this version, logging of authentication tokens is removed from the backend log records.
Changelog Reference:
Palantir Security Advisory (official link—use your org’s access or contact Palantir support).
Github Reference:
If your org has code or image-level access:
- CVE-2022-27896 at NIST NVD
- Palantir-Foundry release notes
Review log file retention policies & sweep old logs for tokens. Rotate API/Foundry tokens immediately if exposure is suspected.
Official CVE Details
- CVE: CVE-2022-27896
References
- NIST NVD Entry for CVE-2022-27896
- Palantir Security Updates
- OWASP - Logging Sensitive Information
In summary:
CVE-2022-27896 is a critical example of why you should never log credentials, secrets, or session tokens—even for debugging. If you administer Palantir Foundry, upgrade to at least v4.461., review all historic logs for leakage, and rotate any tokens exposed. Logging is a security boundary—treat it with the same caution you would your most sensitive data.
Timeline
Published on: 11/14/2022 21:15:00 UTC
Last modified on: 11/17/2022 22:09:00 UTC