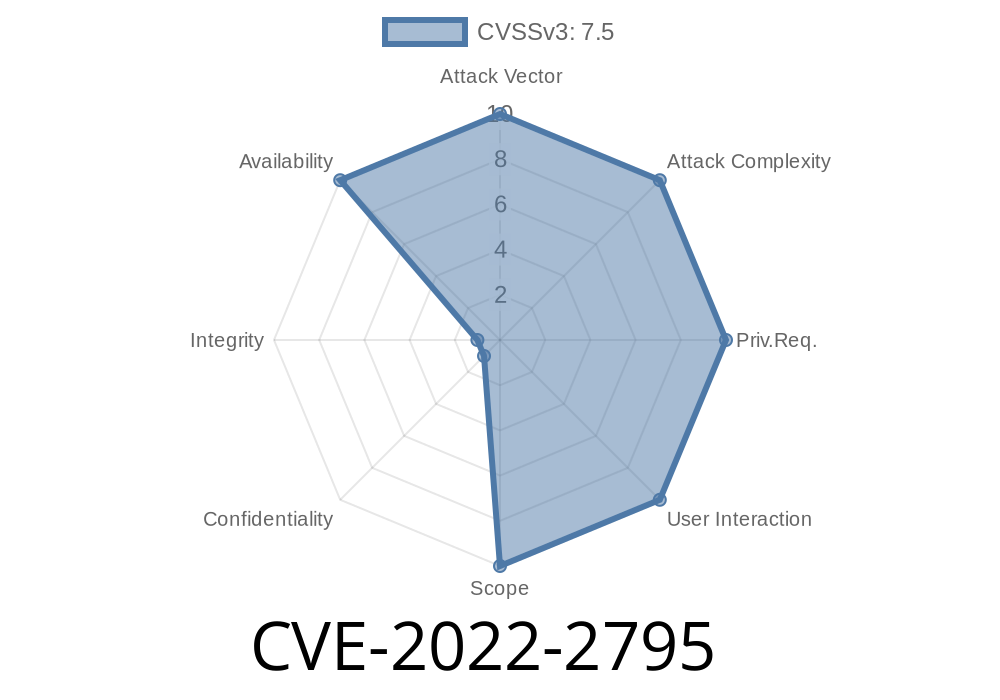
As a result, attackers can leverage this vulnerability to conduct a wide range of attacks against the target system, including command injections, redirection of traffic to malicious hosts, and the theft of sensitive data. In order to exploit this vulnerability an attacker must first be able to send queries to a targeted DNS resolver via HTTP or other protocol. Once a system has been identified as vulnerable to DNS amplification, an attacker can send malicious queries to that system via a wide variety of vectors, including malicious emails, forged web requests, or malicious programs communicating with the DNS server.
How DNS Amplification Works in Practice
DNS Amplification is a type of DDoS attack that uses the Domain Name System (DNS) to generate traffic volume that overwhelms the target system. By exploiting the DNS resolver, attackers can send a wide range of queries to the target server, including those that make it easier for them to launch additional attacks.
The exploitation of this vulnerability requires two components: an initial query sent by an attacker and a list of nameservers which will respond with amplified responses. The exploit may also require specific timing or other conditions in order to execute properly.
Vulnerability Characteristics
The vulnerability is classified as critical because it can be exploited remotely. The vulnerability is also categorized as a private-by-default attack because it requires an attacker to have knowledge of the target system’s IP address in order to exploit it. Furthermore, the vulnerability is a command injection vulnerability because the operating system of the affected system will execute commands sent by the attacker in response to DNS queries. Finally, this vulnerability can be used to conduct a wide range of attacks against the target system.
DNS Amplification and Its Effects
DNS amplification is a technique that can be used to amplify the impact of DNS traffic. This is accomplished by sending a DNS query to a target system and then capturing the response and returning the response to the querier. The difference in size between the original query and its resulting response can be as large as 20x.
So, what are some of the impacts of DNS amplification? Well, first and foremost, this vulnerability can be used to leverage other vulnerabilities on the target system. Attackers may use this vulnerability as an entry point for further exploitation. For example, if an attacker were able to exploit this vulnerability for command injection attacks, they could then leverage other vulnerabilities on the targeted system to gain more control over it. Additionally, attackers may leverage this vulnerability for redirection attacks for which there would be no noticeable indicator when using traditional methods of detection due to how subtle these attacks are. In some cases, attackers have exploited DNS amplification vulnerabilities in order to steal sensitive data from administrators while they're logged into their systems. For example, an attacker may send malicious queries with a high TTL value or with forged responses that are amplified so that administrators see them earlier than expected. Additionally, an attacker may send malicious requests with exact timing in order to capture credentials or other sensitive information when it's being sent back from a service like SMTP or HTTP POST requests.
Coverage of CVE-2022-2795
The DNS redirection vulnerability is being discussed by security researchers and organizations as an important issue. Organizations should be aware that this attack vector has been used in the wild to target infrastructure providers, government organizations and more. The National Institute of Standards and Technology (NIST) issued a warning about this vulnerability on its website in April 2014 and recommended mitigation techniques for those systems that have not been patched at the time of publication. NIST also announced it would not issue any more updates for this advisory.
DNS amplification vulnerabilities are one of the most dangerous vulnerabilities found in recent years, because they can be leveraged by attackers to conduct a wide range of attacks against victims. To exploit this vulnerability an attacker must first be able to send queries to a targeted DNS resolver via HTTP or other protocol. Once an attacker identifies vulnerable DNS resolvers, they can send malicious queries to those systems via a wide variety of vectors, including malicious emails, forged web requests, or malicious programs communicating with the DNS server.
DNS Amplification and its Mitigation
To mitigate this vulnerability, it is recommended that you disable the vulnerable DNS resolver on all systems and replace it with a non-vulnerable resolver. This mitigation can be achieved in several ways:
1) Use DNSSEC to authenticate the query and prevent amplification
2) Restrict access to the vulnerable system via firewall rules
3) Restrict access to the vulnerable system via network segmentation
Timeline
Published on: 09/21/2022 11:15:00 UTC
Last modified on: 09/25/2022 02:15:00 UTC
References
- https://kb.isc.org/docs/cve-2022-2795
- http://www.openwall.com/lists/oss-security/2022/09/21/3
- https://www.debian.org/security/2022/dsa-5235
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/CV4GQWBPF7Y52J2FA24U6UMHQAOXZEF7/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-2795