When using the code>rel="localization"/code> link type, the a> tag does not close after the object has been destroyed, potentially allowing for a use-after-free. This could lead to a potential crash and possible remote code execution. Thunderbird and Firefox are not direct targets for this issue, but if an attacker can convince a user to install a malicious extension, then this issue could be leveraged to install code on the user’s machine.
An attacker could host a malicious extension on a third-party host and thus push an unsuspecting user to install the extension. During installation, the user accepts the “Do you want to install a href=“"> this extension?/a>” prompt and accepts the installation. This prompts the user to restart Thunderbird or Firefox. After restart, the use-after-free occurs and the attacker’s code is executed.
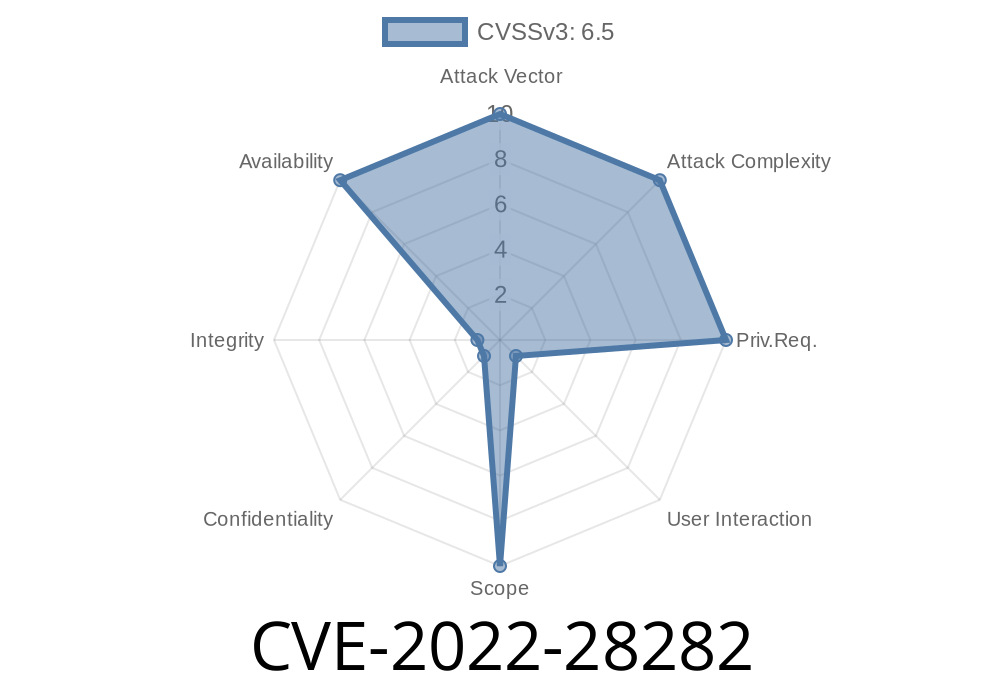
This issue affects Thunderbird 91.8, Firefox 99, and Firefox ESR 91.8. When using the code>rel="localization"/code> link type, the a> tag does not close after the object has been destroyed, potentially allowing for a use-after-free. This could lead to a potential crash and possible remote code execution. Thunderbird and Firefox are not direct targets for this issue, but if an attacker can convince a user to install a malicious extension, then this issue
Vulnerability Scenario
An attacker can convince a user to install a malicious extension. During installation, the user accepts the “Do you want to install a href=“"> this extension?/a>” prompt and accepts the installation. This prompts the user to restart Thunderbird or Firefox. After restart, the use-after-free occurs and the attacker’s code is executed.
Vulnerability Summary
This vulnerability is caused when a use-after-free occurs in the JavaScript engine. This could lead to a potential crash and possible remote code execution. Thunderbird and Firefox are not directly targets for this issue, but if an attacker can convince a user to install a malicious extension, then this issue could be leveraged to install code on the user’s machine.
Thunderbird and Firefox are not direct targets for this issue, but if an attacker can convince a user to install a malicious extension, then this issue could be leveraged to install code on the user’s machine
Timeline
Published on: 12/22/2022 20:15:00 UTC
Last modified on: 12/30/2022 20:54:00 UTC