The latest released version 3.2.56 of the Zephyr Project Manager WordPress plugin is released with the fix to this issue.
Unauthenticated users can now also create issues on projects by uploading files and images, which could allow them to perform Remote Code Execution attacks via uploading a malicious file.
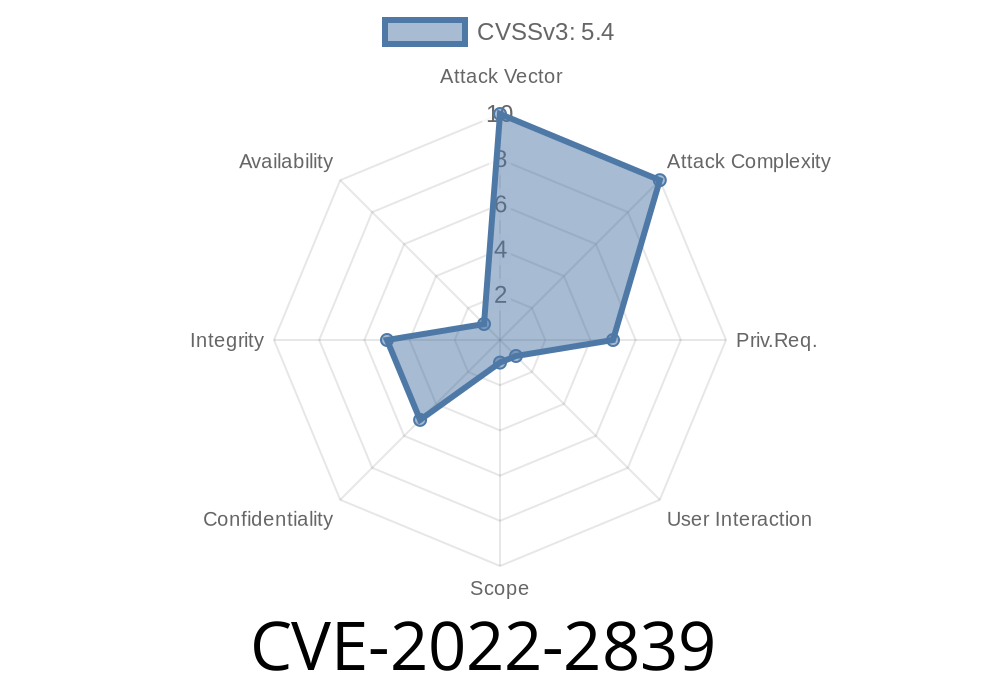
An issue with the authorization of the ‘Add issue’ action in the Zephyr Project Manager WordPress plugin before 3.2.55 allows unauthenticated users to add issues without any authorisation as well as SQL injection. An attacker could inject SQL code into the issue creation form via an unauthenticated user, allowing them to execute arbitrary SQL commands and download and upload any file.
Next Steps
WordPress plugin developers are encouraged to perform regular security audits of their plugins to identify potential issues like these and correct them as soon as possible. An example of such audit is the Google Search Bar or the plugin repository security team at GitHub.
Summary
The latest released version 3.2.56 of the Zephyr Project Manager WordPress plugin is a security update that fixes a vulnerability that could allow an attacker to perform Remote Code Execution attacks via uploading a malicious file.
Timeline
Published on: 10/03/2022 14:15:00 UTC
Last modified on: 10/04/2022 20:34:00 UTC