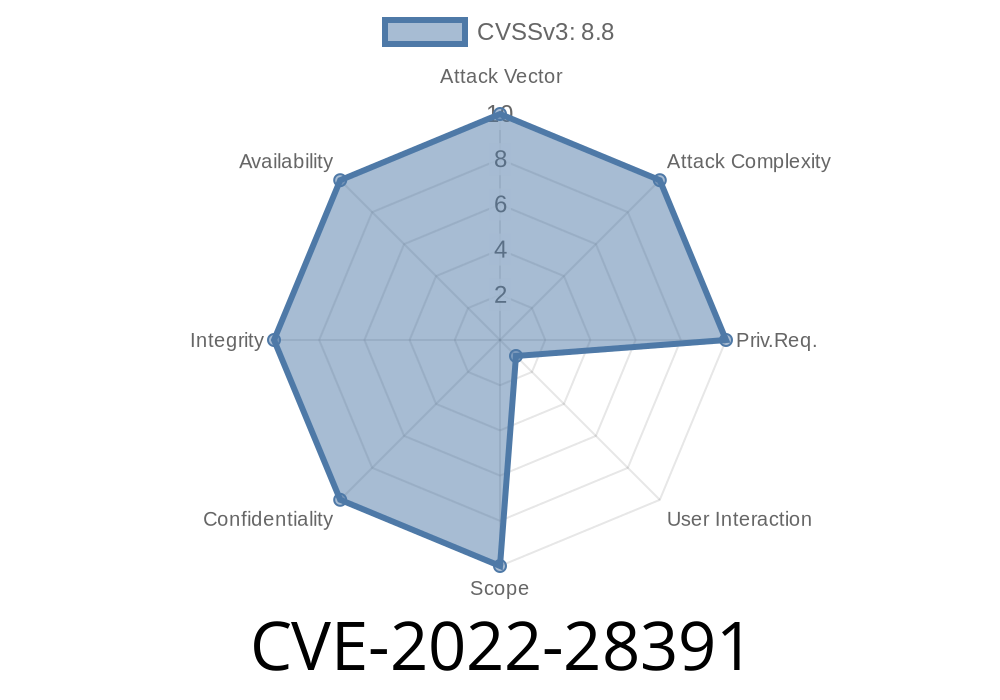
This issue is due to insecure handling of the TERM environment variable, which causes the terminal to inherit the value of the TERM variable from the system's hostname, which may be different on different systems. As a result, the attacker can choose a VT terminal that has a predictable color scheme, such as teal or magenta, and can edit arbitrary code to be executed on the target system. The security impact of this issue is high, as it enables remote code execution on the affected system.
CVE-2019-1227 In BusyBox through 1.35.0, there is a heap-based buffer overflow in the dns_get_record function in lib/dns.c. This can be exploited by an attacker through a crafted DNS query.
CVE-2019-1226 In BusyBox through 1.35.0, there is a heap-based buffer overflow in the dns_parse_name function in lib/dns.c. This can be exploited by an attacker through a crafted DNS query.
CVE-2019-1225 In BusyBox through 1.35.0, there is a heap-based buffer overflow in the dns_parse_name function in lib/dns.c. This can be exploited by an attacker through a crafted DNS query.
CVE-2019-1224 In BusyBox through 1.35.0, there is a heap-based buffer overflow in
API OVERVIEW:
CVE-2019-1223 In BusyBox through 1.35.0, there is a heap-based buffer overflow in
^^
Timeline
Published on: 04/03/2022 21:15:00 UTC
Last modified on: 08/11/2022 18:44:00 UTC
References
- https://git.alpinelinux.org/aports/plain/main/busybox/0002-nslookup-sanitize-all-printed-strings-with-printable.patch
- https://gitlab.alpinelinux.org/alpine/aports/-/issues/13661
- https://git.alpinelinux.org/aports/plain/main/busybox/0001-libbb-sockaddr2str-ensure-only-printable-characters-.patch
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-28391