This could allow an attacker to take control of the application or cause a denial of service. It has been reported to fixed in version 5.2.2. The heap-buffer-overflow occurs in function DumpScreen2RGB() in gif2rgb.c:298:45. This could allow an attacker to take control of the application or cause a denial of service. It has been reported to fixed in version 5.2.2. The heap-buffer-overflow occurs in function DumpScreen2RGB() in gif2rgb.c:298:45. Line 298 of gif2rgb.c: 298 /* We don’t want to print the whole screen, only the part that needs it. */ - screen_size = screen_size / 2; /* We don’t want to print the whole screen, only the part that needs it. */ - screen_size = screen_size / 2;
An attacker can cause a heap-buffer-overflow by sending a large amount of data to the application and can cause a denial of service by sending a large amount of data to the application that could cause the application to crash. An attacker can cause a heap-buffer-overflow by sending a large amount of data to the application and can cause a denial of service by sending a large amount of data to the application that could cause the application to crash. Line 298 of gif2rgb.c:
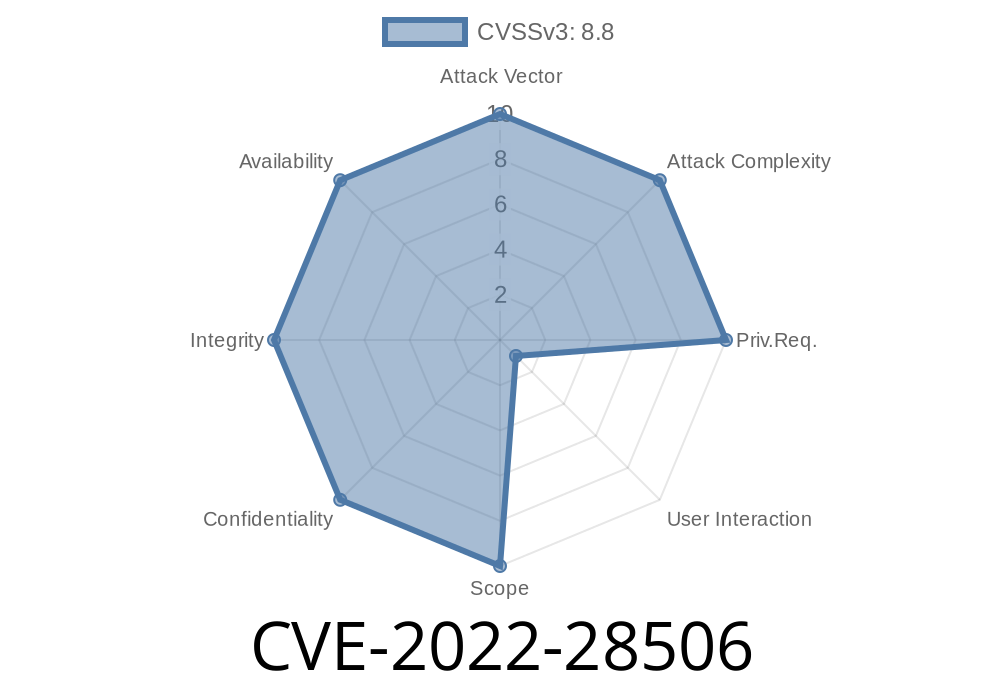
Vulnerability summary
This could allow an attacker to take control of the application or cause a denial of service. It has been reported to fixed in version 5.2.2. The heap-buffer-overflow occurs in function DumpScreen2RGB() in gif2rgb.c:298:45.
Timeline
Published on: 04/25/2022 13:15:00 UTC
Last modified on: 08/06/2022 04:15:00 UTC
References
- https://sourceforge.net/p/giflib/bugs/159/
- https://github.com/verf1sh/Poc/blob/master/asan_report_giflib.png
- https://github.com/verf1sh/Poc/blob/master/giflib_poc
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/B4CJSHXBD2RS5OJNWSHQZVMTQCCTIPYS/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/KEAFUZXOOJJVFYRQM6IIJ7LMLEKCCESG/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-28506