The vulnerability is exposed when the videoAddNew module is called on an HTTP request, allowing an attacker to inject malicious code into pages where the videoAddNew function is called.
Specially-crafted HTTP requests can be used to exploit this vulnerability. You can prevent exploitation of this vulnerability by checking the received data against a whitelist of known data types. Additionally, review the request parameters to make sure they are not being sent to an end point where they could be used to exploit this vulnerability. This vulnerability is being actively researched and is not yet known to be publicly exploited. There are no workarounds at this time to mitigate this vulnerability.
When reviewing the source code of the vulnerable module, you can identify the code that is being called through the HTTP request. You can then adjust the code to check for the received data before allowing it to be executed. For example, you can use the if (isset($data)) { } construct to verify that the data is not malicious before allowing it to be executed.
4.2
.6: The vulnerability
The vulnerability is exposed when the videoAddNew module is called on an HTTP request, allowing an attacker to inject malicious code into pages where the videoAddNew function is called.
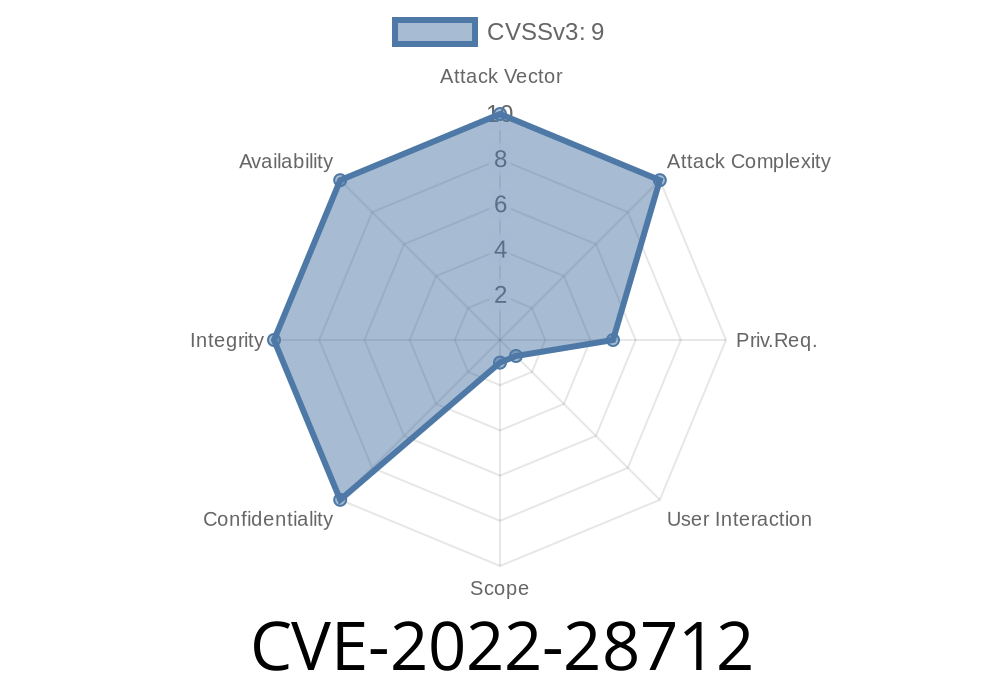
Reference: CVE-2022-28712
3.2.5 - CVE-2023-28713
The vulnerability is exposed when the videoAddNew module is called on an HTTP request, allowing an attacker to inject malicious code into pages where the videoAddNew function is called.
Specially-crafted HTTP requests can be used to exploit this vulnerability. You can prevent exploitation of this vulnerability by checking the received data against a whitelist of known data types. Additionally, review the request parameters to make sure they are not being sent to an end point where they could be used to exploit this vulnerability. This vulnerability is being actively researched and is not yet known to be publicly exploited. There are no workarounds at this time to mitigate this vulnerability.
When reviewing the source code of the vulnerable module, you can identify the code that is being called through the HTTP request. You can then adjust the code to check for the received data before allowing it to be executed. For example, you can use the if (isset($data)) { } construct to verify that the data is not malicious before allowing it to be executed.
Timeline
Published on: 08/22/2022 19:15:00 UTC
Last modified on: 08/26/2022 13:49:00 UTC