Meeting Connector is an extensible content management platform that enables meeting organizers to create, edit, and share documents and presentations. It is widely used in enterprises, government agencies, non-profit organizations, education, and healthcare. On March 13, 2019, Zoom released version 4.8.20220815.130 of MMR, which is the latest version at the time of publishing. There are two ways to install MMR in your organization. You can either download it from a URL directly from the Zoom website, or you could install it using a distribution package. If you used an installation package, you should immediately upgrade to the latest version. A recently discovered vulnerability in the on-premise version of MMR could be exploited by a malicious actor to obtain the audio and video feed of a meeting they were not authorized to join.
What is MMR?
The Meeting Manager Runtime (MMR) is a web portal that enables meeting organizers to create, edit, and share documents and presentations. Zoom released the first version of MMR in May 2009, which was an on-premise software. Today, MMR can be deployed across a range of platforms including Zoom, Office 365, Google Apps for Work and G Suite and hosted on Amazon Web Services or Microsoft Azure.
Vulnerability description
There is a vulnerability in the on-premise version of MMR. The vulnerability could be exploited by a malicious actor to obtain the audio and video feed of a meeting they were not authorized to join.
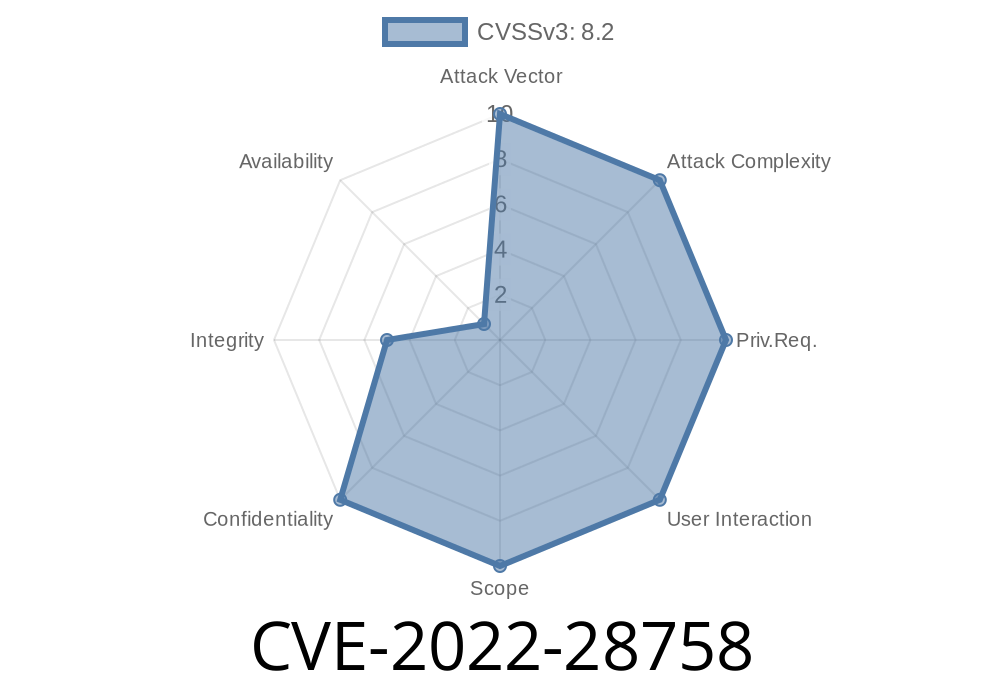
CVE-2022-28758
Estimating Exposure
The vulnerability could be exploited by a malicious actor to obtain the audio and video feed of a meeting they were not authorized to join. This includes meetings hosted with the on-premise version of MMR that are not currently being hosted or meetings hosted with the ZOOM Conferences service.
Timeline
Published on: 09/16/2022 22:15:00 UTC
Last modified on: 09/21/2022 16:31:00 UTC