The target user must have installed the Zoom client on their system and logged in to the system as a user with an elevated privileges. The local attacker must convince the user to open a maliciously crafted website or click on a malicious link sent by email. Zoom for Windows is already blocked from accessing certain sensitive websites by default. Therefore, it is more likely for this to occur in public places such as conference rooms.
An attacker could also assign the meeting or conference room to another user and convince them to log in as a user with elevated privileges. In this scenario, the attacker is the user that should be subject to the DLL injection vulnerability. An attacker could also send a link to the user through email or a message board and trick the user into opening the link. In both scenarios, the meeting room or conference room is the target. An attacker could also assign the meeting or conference room to another user and convince them to log in as a user with elevated privileges. In this scenario, the attacker is the user that should be subject to the DLL injection vulnerability. An attacker could also send a link to the user through email or a message board and trick the user into opening the link. In both scenarios, the meeting room or conference room is the target.
Affected SoftwareZoom for Windows a target="_blank" href="http://www.chanakya.com/downloads/zoom_win
_10_0.1.1-3659.EXE">Zoom for Windows 8.0/8.1/10
Mitigation
The DLL injection vulnerability can be mitigated by restricting the privileges of a user that logs into a meeting room or conference room. If Zoom for Windows is installed on a system and is logged in with elevated privileges, Zoom for Windows must also be configured to have restricted privileges.
Zoom for Windows already has default settings to block access to certain sensitive websites such as banking websites and social media websites. This can be easily modified by the administrator who installs Zoom for Windows on the system and limits their access accordingly.
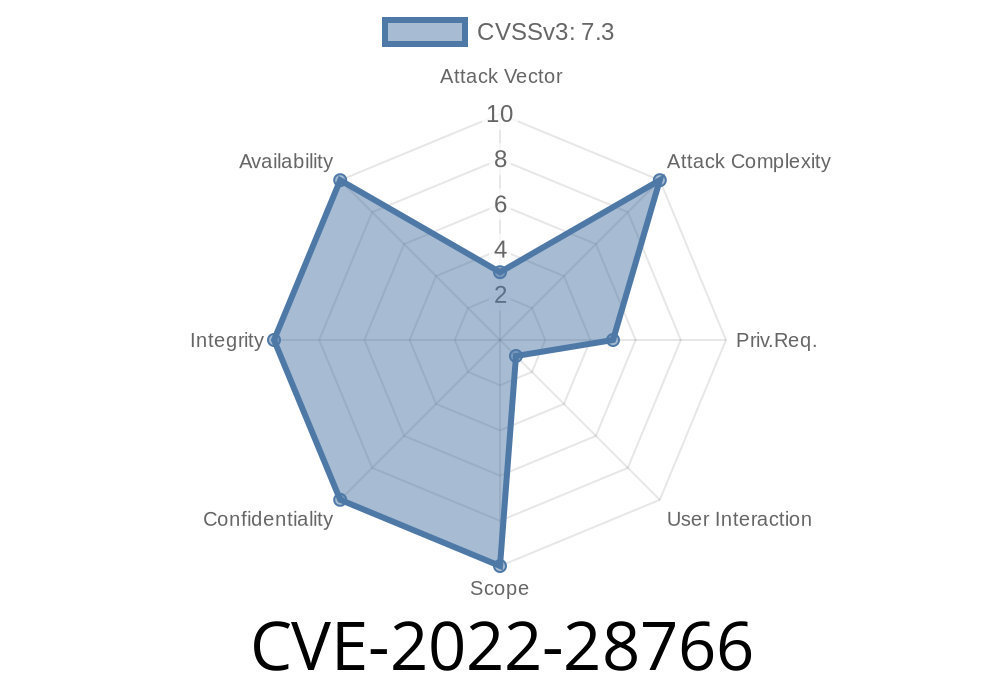
ID: 2023-28766
Zoom for Windows: Zoom is a video conferencing software.
This vulnerability affects Zoom for Windows and requires a user to have installed the software on their system with elevated privileges, then convincing them to open a maliciously crafted website or click on a malicious link sent by email.
An attacker could also assign the meeting or conference room to another user and convince them to log in as a user with elevated privileges. In this scenario, the attacker is the user that should be subject to the DLL injection vulnerability. An attacker could also send a link to the user through email or a message board and trick the user into opening the link. In both scenarios, the meeting room or conference room is the target.
CVE-2023-28767
The target user must have installed the Zoom client on their system and logged in to the system as a user with an elevated privileges. An attacker must convince the user to open a maliciously crafted website or click on a malicious link sent by email.
Timeline
Published on: 11/17/2022 23:15:00 UTC
Last modified on: 11/22/2022 16:14:00 UTC