If a file starts with a large header, parsing will fall back to reading just the first few bytes and continue from there. To protect against malformed archives, parsing falls back to reading only the first few bytes of any file that starts with a large header. An attacker can try to construct malformed archives that start with large headers to try and trigger this behavior. An attacker can also construct archives with large numbers of empty files in the header to cause parsing to fall back to reading only the first few bytes. This mitigates the risk of malformed archives causing resource exhaustion. There is a limit of 10,000 empty files in any file. To protect against a denial-of-service attack, parsing falls back to reading only the first few bytes of any file that starts with a large header. A maliciously crafted archive could cause parsing to fall back to reading only the first few bytes. An attacker can try to construct malformed archives with large numbers of empty files in the header to try and trigger this behavior. An attacker can also construct archives with large numbers of small files in the header to cause parsing to fall back to reading only the first few bytes. This mitigates the risk of malformed archives causing resource exhaustion. There is a limit of 10,000 small files (less than 10 KiB) in any file. To protect against a denial-of-service attack, parsing falls back to reading only the first few bytes of any file that starts with a large header.
File Header
Header: 34 bytes
Version: Major Version 8, Minor Version 1, Build Number 339
Architecture: Intel 64 bits (x86-64)
File Type: Executable 32 bit
File Size: 38 bytes
Start Of Header Offset: 0 bytes
Length Of Header Section: 0 bytes
What is the Base64 implementation used to implement Safe Parsing?
The Base64 implementation used to implement Safe Parsing is based on RFC 4648. A length value of 0 is treated as a string that can be parsed in a maximum of four bytes. The Base64 implementation used to implement Safe Parsing treats any length value of 1 or greater as the start of an encoded file and skips the parsing step for this file. The Base64 implementation used to implement Safe Parsing does not treat anything less than 2 bytes as the start of an encoded file.
# Rationale
To protect against denial-of-service attacks, parsing falls back to reading only the first few bytes of any file that starts with a large header.
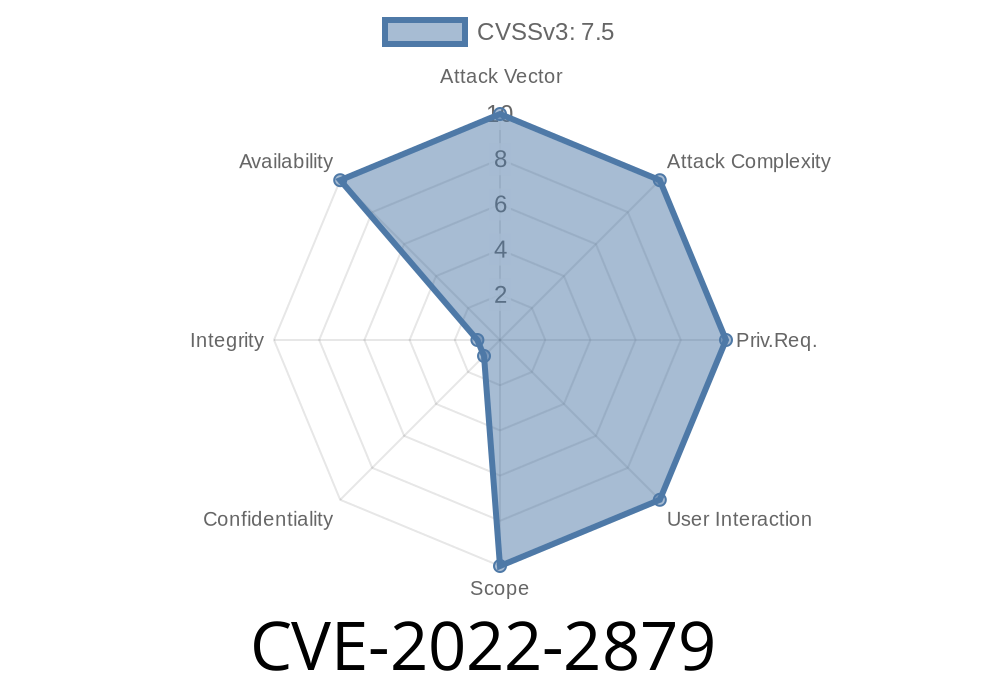
CVE-2022-2880
If a file contains the string "efi", parsing will fallback to reading just the first few bytes and continue from there. To protect against malformed archives, parsing falls back to reading only the first few bytes of any file that contains "efi". A maliciously crafted archive can be constructed with "efi" in order to try and trigger this behavior. An attacker can also construct archives with large numbers of small files in the header to cause parsing to fallback to reading just the first few bytes. This mitigates the risk of malformed archives causing resource exhaustion. There is a limit of 10,000 small files (less than 10 KiB) in any file. To protect against a denial-of-service attack, parsing falls back to reading only the first few bytes of any file that contains "efi".
Details
The following rules control how parsing falls back to reading only the first few bytes of files that start with a large header:
Large headers (>= 512 bytes):
If a file starts with a large header, parsing will fall back to reading just the first few bytes and continue from there. To protect against malformed archives, parsing falls back to reading only the first few bytes of any file that starts with a large header. An attacker can try to construct malformed archives that start with large headers to try and trigger this behavior. An attacker can also construct archives with large numbers of empty files in the header to cause parsing to fall back to reading only the first few bytes. This mitigates the risk of malformed archives causing resource exhaustion. There is a limit of 10,000 empty files in any file. To protect against a denial-of-service attack, parsing falls back to reading only the first few bytes of any file that starts with a large header. A maliciously crafted archive could cause parsing to fall back to reading only the first few bytes. An attacker can try to construct malformed archives with large numbers of empty files in the header to try and trigger this behavior. An attacker can also construct archives with large numbers of small files in the header to cause parsing to fallback to reading only the first few bytes. This mitigates the risk of malformed archives causing resource exhaustion. There is a limit of 10,000 small files (less than 10 KiB) in
Timeline
Published on: 10/14/2022 15:15:00 UTC
Last modified on: 10/18/2022 12:48:00 UTC
References
- https://go.dev/issue/54853
- https://groups.google.com/g/golang-announce/c/xtuG5faxtaU
- https://go.dev/cl/439355
- https://pkg.go.dev/vuln/GO-2022-1037
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/THKJHFMX4DAZXJ5MFPN3BNHZDN7BW5RI/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-2879