When executing a remote query, the server, by default, listens for connections on all local endpoints, and if an attacker, on the same subnet, is able to connect to the server, an attacker may run arbitrary code on the server. In version 18.12.05 and earlier, an attacker may exploit this behavior, by connecting to the server on port 1099, to run arbitrary code on the server. Upgrade to at least 18.12.06 or apply patches at https://issues.apache.org/jira/browse/OFBIZ-12646. When executing a remote query, the server, by default, listens for connections on all local endpoints, and if an attacker, on the same subnet, is able to connect to the server, an attacker may run arbitrary code on the server. In version 18.12.05 and earlier, an attacker may exploit this behavior, by connecting to the server on port 1099, to run arbitrary code on the server. Upgrade to at least 18.12.06 or apply patches at https://issues.apache.org/jira/browse/OFBIZ-12646. When executing a remote query, the server, by default, listens for connections on all local endpoints, and if an attacker, on the same subnet, is able to connect to the server, an attacker may run arbitrary code on the server. In version 18.12.05 and earlier, an attacker
Vulnerability: Untrusted Java Applet Remote Code Execution
An attacker may exploit this vulnerability, by connecting to the server on port 1099, to run arbitrary code on the server. Upgrade to at least 18.12.06 or apply patches at https://issues.apache.org/jira/browse/OFBIZ-12646
When executing a remote query, the server, by default, listens for connections on all local endpoints, and if an attacker, on the same subnet, is able to connect to the server, an attacker may run arbitrary code on the server. In version 18.12.05 and earlier, an attacker may exploit this behavior, by connecting to the server on port 1099, to run arbitrary code on the server. Upgrade to at least 18.12.06 or apply patches at https://issues.apache.org/jira/browse/OFBIZ-12646
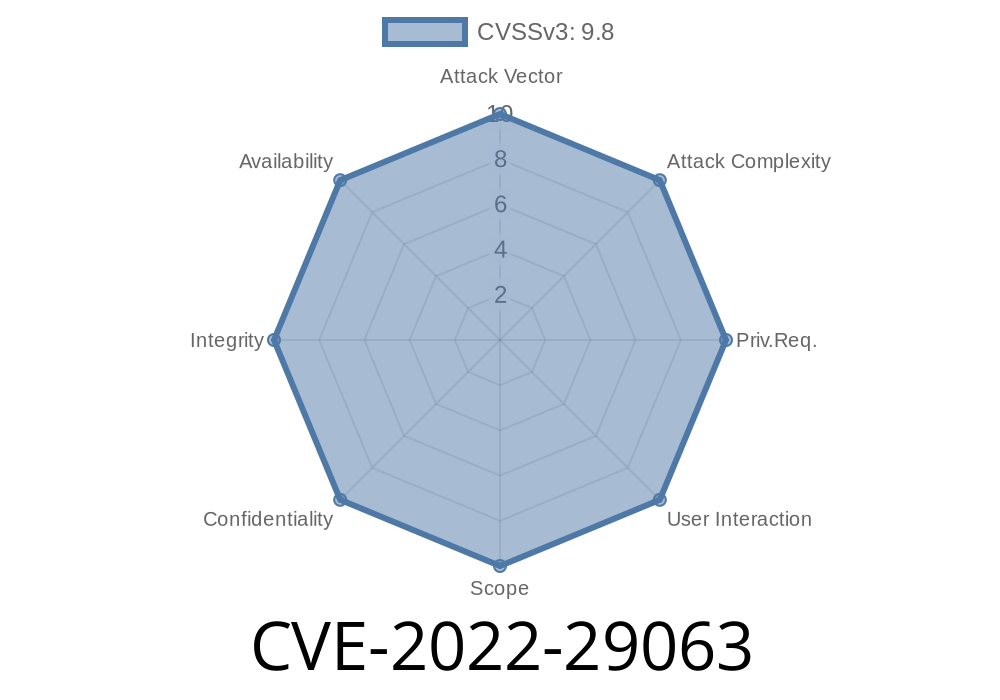
References CVE-2022-29063
https://issues.apache.org/jira/browse/OFBIZ-12646
Solution: Apply patches or upgrade to version 18.12.06
The Apache Foundation has released patches for the Apache OFBiz software, which can be downloaded from their site:
https://issues.apache.org/jira/browse/OFBIZ-12646
Timeline
Published on: 09/02/2022 07:15:00 UTC
Last modified on: 09/08/2022 12:17:00 UTC