The Remote Access Connection Manager service and the Remote Access Connection 2.0 service on Windows 7, Windows 2008 R2, Windows 2012, Windows 8, Windows 10, and Windows Server 2008 R2 and later operating systems are susceptible to a remote code execution vulnerability that could allow an attacker to take control of an affected system.
Attackers could exploit this vulnerability by persuading an authorized user to enable Remote Access on the system. An attacker could then install programs or start services with the elevated privileges to malicious code. System administrators who are privileged users could also be tricked into enabling Remote Access on their systems. Exploits that run with elevated privileges on an affected system could be used to launch attacks against other systems. An attacker could potentially exploit this vulnerability to take control of an affected system and then use that system to launch attacks against other systems. Windows 10 and Windows Server 2016 are not vulnerable to this issue. In Windows 10 and Windows Server 2016, the Remote Access Connection Manager service is not installed by default. To check if this service is installed, open a command prompt and run the following command:
In Windows 10 and Windows Server 2016, the Remote Access Connection 2.0 service is not installed by default. To check if this service is installed, open a command prompt and run the following command:
Vulnerability details
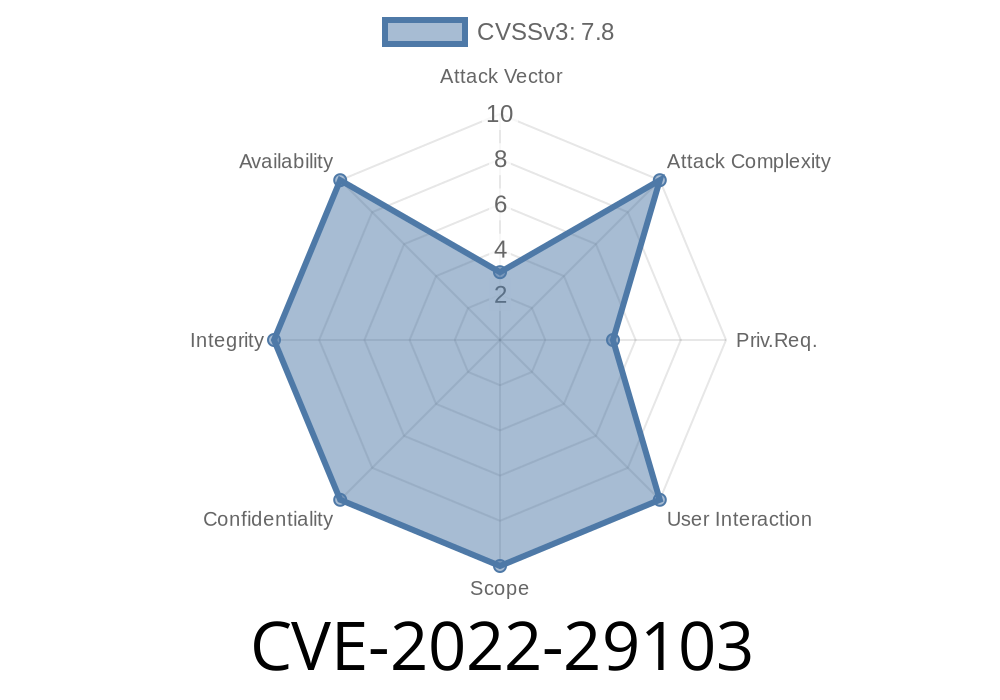
Vulnerability: Remote Access Connection Manager service and the Remote Access Connection 2.0 service on Windows 7, Windows 2008 R2, Windows 2012, Windows 8, Windows 10, and Windows Server 2008 R2 and later operating systems are susceptible to a remote code execution vulnerability.
Description: Attackers could exploit this vulnerability by persuading an authorized user to enable Remote Access on the system. An attacker could then install programs or start services with the elevated privileges to malicious code. System administrators who are privileged users could also be tricked into enabling Remote Access on their systems. Exploits that run with elevated privileges on an affected system could be used to launch attacks against other systems. An attacker could potentially exploit this vulnerability to take control of an affected system and then use that system to launch attacks against other systems.
Impact: System administrators who are privileged users could also be tricked into enabling Remote Access on their systems. Exploits that run with elevated privileges on an affected system could be used to launch attacks against other systems. An attacker could potentially exploit this vulnerability to take control of an affected system and then use that system to launch attacks against other systems.
Affected Systems: This issue affects all operating systems listed above except for Windows 10 and Windows Server 2016 versions of these services which are not vulnerable due to default settings for the services in those operating systems
Mitigation: Microsoft has released a security update for CVE-2022-29103 which addresses this issue in supported versions of Microsoft
Windows 8 and Windows Server 2012
R2 are vulnerable
Windows 8 and Windows Server 2012 R2 are vulnerable to this Remote Access Connection manager vulnerability. Both operating systems have the Remote Access Connection Manager service installed by default, which is susceptible to this exploit.
In order to check if your system is vulnerable, open a command prompt and run the following command:
In Windows 8 and Windows Server 2012 R2, the Remote Access Connection 2.0 service is not installed by default. To check if this service is installed, open a command prompt and run the following command:
The Remote Access Connection Manager service on Windows 7, Windows 2008 R2, Windows 2012, Windows 8, Windows 10 and Windows Server 2008 R2 versions of the operating system are susceptible to a remote code execution vulnerability that could allow an attacker to take control of an affected system. These vulnerabilities affect both the client-side and server side of the connection service. As such, a malicious user may be able to take control of an affected system from within or outside of it. If a user with administrative privileges has enabled remote access for their PC then hackers can exploit these vulnerabilities without even having physical access to that PC. Here are some ways that hackers can exploit these vulnerabilities:
1) Exploiting via User Privileges - An attacker who has admin rights on their own machine may be able to exploit these vulnerabilities without even having physical access to another computer. They could persuade an authorized user or someone with administrative privileges to enable remote access on their computer
Affected Software:
Windows 7, Windows 2008 R2, Windows 2012, Windows 8, Windows 10 and Windows Server 2008 R2 and later systems
Be sure to follow the instructions in the article to avoid becoming a victim of this vulnerability.
Timeline
Published on: 05/10/2022 21:15:00 UTC
Last modified on: 05/20/2022 17:59:00 UTC