These issues were fixed in OpenSSL 1.0.2i. As a result of the fix, Debian has removed support for OpenSSL in squeeze. (Debian 7.0 was the last version supported). Debian recommends that users of OpenSSL 1.0.2 or 1.0.1 installations upgrade to a new version as soon as possible. Users of Debian 7.0 or earlier may want to consider manually uninstalling OpenSSL packages before upgrading to Debian 8.1. (For instructions, see: https://www.debian.org/unstable/news)
CVE-2022-29127: A TLS renegotiation attack was discovered that could be exploited during a SSL/TLS handshake. If a client connected to an attacker's server supports renegotiation and the renegotiation request is accepted by the server, then the client and server can end up negotiating new protocols that are not supported by either side. This could allow an attacker to inject arbitrary content into the client request, allowing them to inject arbitrary code into the server response. This could lead to a loss of integrity of the server response if the server is using encryption. Debian points to the OpenSSL 1.0.2i announcement for more information about this issue.
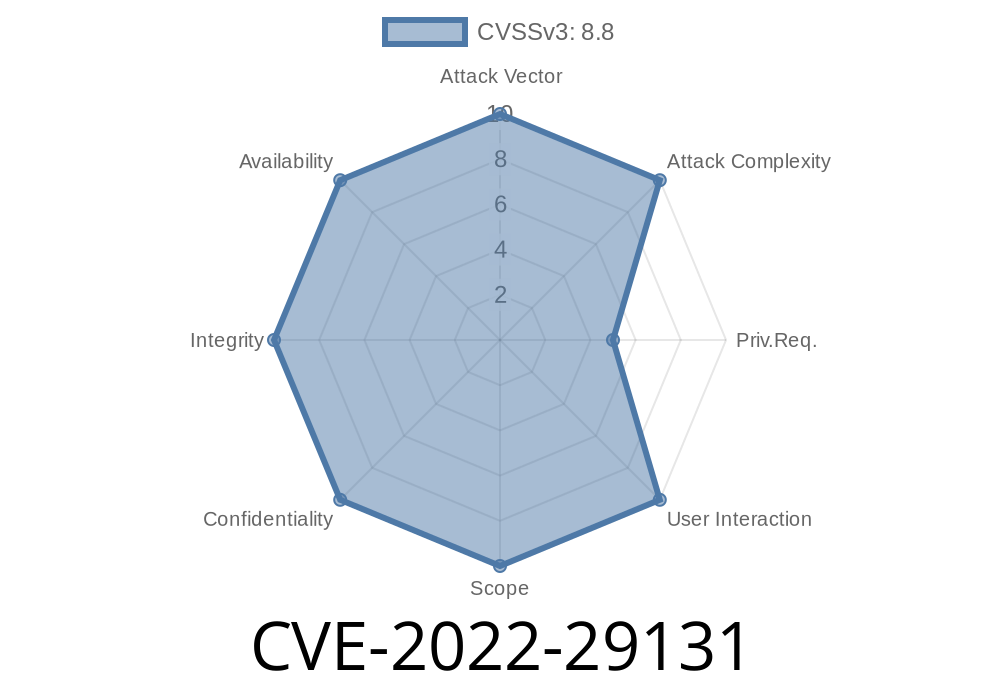
CVE-2022-29131: A denial of service flaw was discovered in the way OpenSSL parsed TMI messages. A remote attacker could use this flaw to crash a TLS/SSL client using OpenSSL by sending
The Debian Installer: an update is available!
The Debian Installer: an update is available!
Please note that this release does not represent a new version of Debian and is not supported with any further updates.
Debian 8.1 was released on the 3rd of December, 2016. As a result, Debian 7.0 has reached its end-of-life and will no longer be supported with security updates as of the 2nd of January, 2017.
References:
Debian: https://www.debian.org/security/2017/dsa-3742
OpenSSL: https://www.openssl.org/news/secadv_20170331.txt
OpenSSL 1.0.2i: https://www.openssl.org/news/v1_0_2i
Timeline
Published on: 05/10/2022 21:15:00 UTC
Last modified on: 05/23/2022 17:29:00 UTC