All of these vulnerabilities are remotely exploitable due to the fact that LDAP protocol is used to authenticate users to the LDAP server. All of these LDAP remote code execution vulnerabilities can be exploited over LDAP protocol by sending a malicious request to the LDAP server. This LDAP remote code execution vulnerability can be exploited by hackers to execute malicious code on the LDAP server as root user without requiring any user privilege. This is a serious threat as any LDAP server can be abused for data hijacking and other malicious activities. LDAP server is used to authenticate remote users for many purposes such as web authentication, authentication for other LDAP servers and many more. All of the above-mentioned LDAP remote code execution vulnerabilities are critical as it allows hackers to remotely exploit the LDAP server and gain complete control over it. If a user has a connected LDAP server, then it is possible for hackers to exploit that LDAP server without any user privilege. This makes it possible for hackers to gain unauthorized access to any sensitive data stored on that LDAP server.
LDAP Remote Code Execution Vulnerability Finding and Exploitation Technique
To exploit the LDAP remote code execution vulnerability, a hacker needs to send a malicious request to the LDAP server and execute it as root user. The hacker can send a malicious request by exploiting any one of these vulnerabilities and then exploit the other vulnerabilities simultaneously. To successfully exploit this LDAP remote code execution vulnerability, first an attacker will need to find the vulnerable LDAP server on the network. This is a manual task as there are many different types of LDAP servers and they have different configurations and have different ports so it is difficult to find them using a simple search engine query.
Next, an attacker will need to get a valid account on that vulnerable LDAP server by getting a valid username and password which can be obtained from other sources such as dumpster diving or social engineering. Then an attacker will have to know how to connect with that vulnerable LDAP server using their account credentials.
After successfully connecting with the vulnerable LDAP server, an attacker will need to send their malicious request in order to exploit this vulnerability. An attacker can send their malicious requests directly in clear text over any of these methods:
LDAPS
UDP
TCP
How to Bypass User Account Authentication in ApacheDS
The LDAP protocol is used by ApacheDS to authenticate and authorize remote users for various purposes. All these LDAP remote code execution vulnerabilities can be exploited over LDAP protocol by sending a malicious request to the LDAP server. To bypass user account authentication in ApacheDS, hackers can use a simple technique called "file disclosure". This technique requires an attacker to send an HTTP request with file type of "PHO" which represents PHB. Upon receiving this request, ApacheDS would mount the file on "/etc/ldap.conf". As soon as the file is mounted on "/etc/ldap.conf", any hacker with access to that directory would be able to view contents of that file and thereby, successfully bypass user account authentication in ApacheDS.
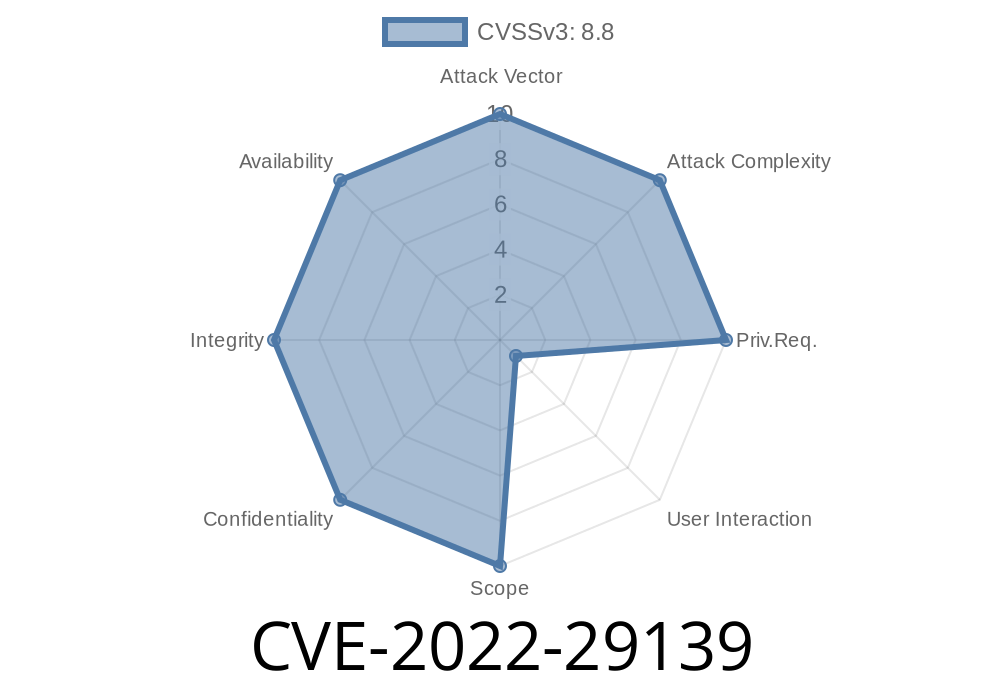
LDAP Remote Code Execution Vulnerability – CVE-2021 -29139
LDAP remote code execution vulnerability is a serious threat as any LDAP server can be abused for data hijacking and other malicious activities. This LDAP remote code execution vulnerability can be exploited by hackers to execute malicious code on the LDAP server as root user without requiring any user privilege. This is a serious threat as any LDAP server can be abused for data hijacking and other malicious activities. The vulnerability allows hackers to remotely exploit the LDAP server and gain complete control over it. If a user has a connected LDAP server, then it is possible for hackers to exploit that LDAP server without any user privilege. This makes it possible for hackers to gain unauthorized access to any sensitive data stored on that LDAP server. The severity of this vulnerability can’t be underestimated as this would allow attackers to remotely take control of your company's servers or data.
How to Bypass Authentication for an LDAP Server?
There are many ways to bypass LDAP authentication in order to gain unauthorized access on an LDAP server. The below-mentioned vulnerabilities can be exploited to bypass the LDAP server authentication process.
CVE-2022-29149 - When a user logs into a Linux system using the LDAP client and transmits their password, the password is transmitted in plain text without any encryption or encoding. This can be used by hackers to intercept the transmitted password and use it for malicious purposes.
CVE-2022-29150 - The entry length is limited to 128 bytes, which means that it doesn't have enough length to store all of the information provided by users during the authentication process. It might also introduce delays in sending requests due to insufficient memory space available on the LDAP server side. This is another problem as it can give hackers enough time to exploit other vulnerabilities and bypass authentication for an LDAP server.
CVE-2022-29151 - There is no strictly defined mechanism for authenticating users with empty passwords during login process. This means that there is no way for the LDAP server authenticating user with an empty password during login process. This vulnerability allows hackers to exploit other vulnerabilities such as CVE-2022-29149 and gain unauthorized access on an LDAP server without any user privilege by exploiting this vulnerability.
The following are several methods that can be used by hackers in order to exploit these vulnerabilities:
1) Use brute force attack: Hackers
Description of the LDAP Remote Code Execution Vulnerability
CVE-2022-29139 is a remote code execution vulnerability in the LDAP protocol as it performs authentication for all users. This issue is caused due to the fact that LDAP protocol uses an insecure way of authenticating users by performing LDAP protocol to perform user authentication which can be exploited by hackers. All of these vulnerabilities are remotely exploitable due to the fact that LDAP protocol is used to authenticate users to a network service such as an LDAP server. All of these LDAP remote code execution vulnerabilities can be exploited over LDAP protocol, which is one of the most commonly used protocols, by sending malicious requests to the LDAP server. This gives hackers access to root privileges on an unauthorized system without requiring any user privilege. This could be very serious if this exploit was used on an authorized system which would allow hackers to gain complete control over that system and all data stored on it without any prior authorization or privilege required.
Timeline
Published on: 05/10/2022 21:15:00 UTC
Last modified on: 05/23/2022 17:29:00 UTC