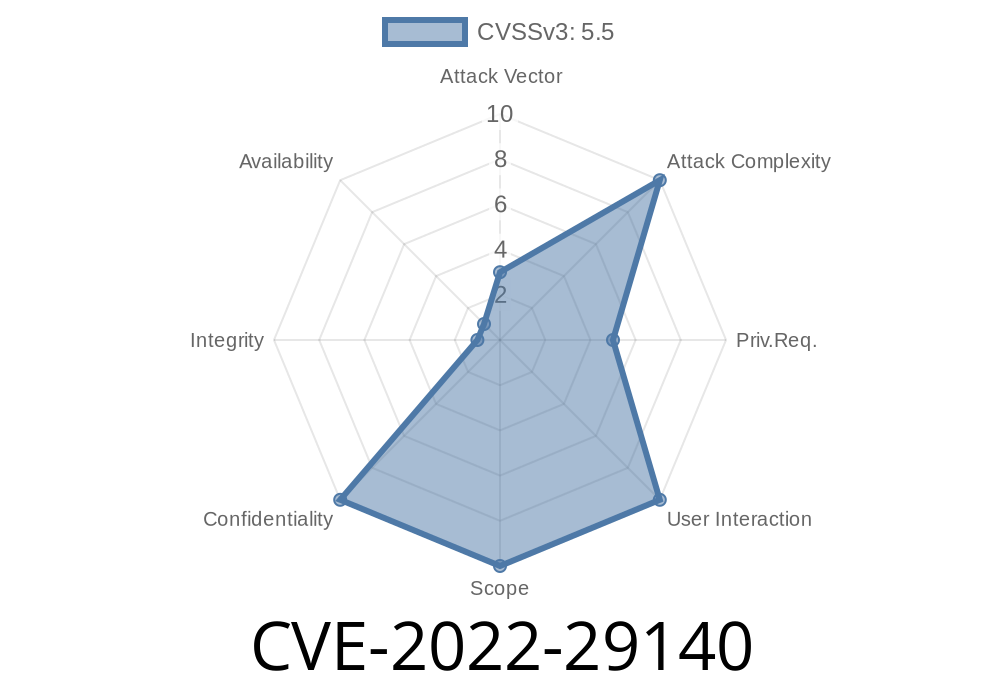
This vulnerability was publicly disclosed in June 2019 by X-Force researcher Mo Ansar. In the security community, this issue is commonly referred to as the “Print Spooler” vulnerability due to its prevalence in Windows print servers. This issue is caused by the way that the Windows print spooler service handles remote printing requests. A successful exploit could be used by an attacker to execute arbitrary code on the targeted system. To be vulnerable, the target system must have a vulnerable version of the print spooler service installed and enabled. An attacker can exploit this vulnerability by sending a remote printing request to a targeted system. A successful exploit of this vulnerability could be used by an attacker to execute arbitrary code on the targeted system. This vulnerability is critical due to the way the Windows print spooler service handles remote printing requests. Systems that are running older versions of Windows are most likely vulnerable to this issue. An attacker can exploit this vulnerability by sending a remote printing request to a targeted system. This vulnerability is critical due to the way the Windows print spooler service handles remote printing requests. Systems that are running older versions of Windows are most likely vulnerable to this issue. Microsoft released an update for this issue on April 10, 2019. However, some users may not have received this update
Microsoft Windows Print Spooler Service Remote Code Execution Vulnerability
A security vulnerability has been found in the Windows print spooler service that could allow for remote code execution. This vulnerability can be exploited by sending a connection request to an affected system. Even if the print spooler service is not enabled, an attacker still has the ability to exploit this vulnerability by making a connection request to the affected system. An attacker could leverage this vulnerability to execute arbitrary code on the targeted system. In order to exploit this vulnerability, an attacker would need write access to specific folders and files on the targeted system. Microsoft released an update for this issue on April 10, 2019. However, some users may not have received this update.
Microsoft Windows Print Spooler Service Vulnerability
The vulnerability is caused by the Windows print spooler service not properly handling remote printing requests. A successful exploit could be used by an attacker to execute arbitrary code on the targeted system. To be vulnerable, the target system must have a vulnerable version of the print spooler service installed and enabled. An attacker can exploit this vulnerability by sending a remote printing request to a targeted system.
An attacker can exploit this vulnerability by sending a remote printing request to a targeted system. The vulnerability is critical due to the way that Windows print spooler service handles remote printing requests. Systems that are running older versions of Windows are most likely vulnerable to this issue. Microsoft released an update for this issue on April 10, 2019. However, some users may not have received this update
Limitations and Recommendations
The Print Spooler vulnerability can be exploited if the targeted system has a vulnerable version of the print spooler service installed and enabled. This issue is critical due to the way that the Windows print spooler service handles remote printing requests.
This vulnerability affects all versions of Windows except Windows 10, Windows Server 2019, and Windows Server 2016.
How can I check if I am vulnerable?
To check whether or not you are vulnerable, run the following commands in PowerShell:
Get-WmiObject -Class Win32_Printer | Select-Object Name
Find the name of the print spooler service. You should see "Print Spooler" in this list. If you see this entry, then your computer is most likely vulnerable to this issue.
Timeline
Published on: 05/10/2022 21:15:00 UTC
Last modified on: 05/23/2022 17:29:00 UTC