Tautulli, a software monitoring service, is prone to CSRF via Tautulli’s web monitoring endpoints. Fixed in 1.9.17 and 1.10.10.
On some Linux distributions, Docker instances that use the kernel version 3.10 may encounter “deadlocks in kernel thread context”. Fixed in Docker version 1.11.5 and later.
It may be possible for an adversary to take advantage of the Consul software monitoring feature and monitor arbitrary application events in arbitrary applications. Fixed in Consul version 1.11.6 and later.
On Debian-based Linux distributions, the Consul systemd service may experience undefined behavior when reloading configuration. Fixed in Consul 1.10.10 and 1.11.5.
Consul may crash when a client-server handshake has been replayed. Fixed in Consul version 1.9.17 and 1.10.10.
Important note:
This is not a security advisory.
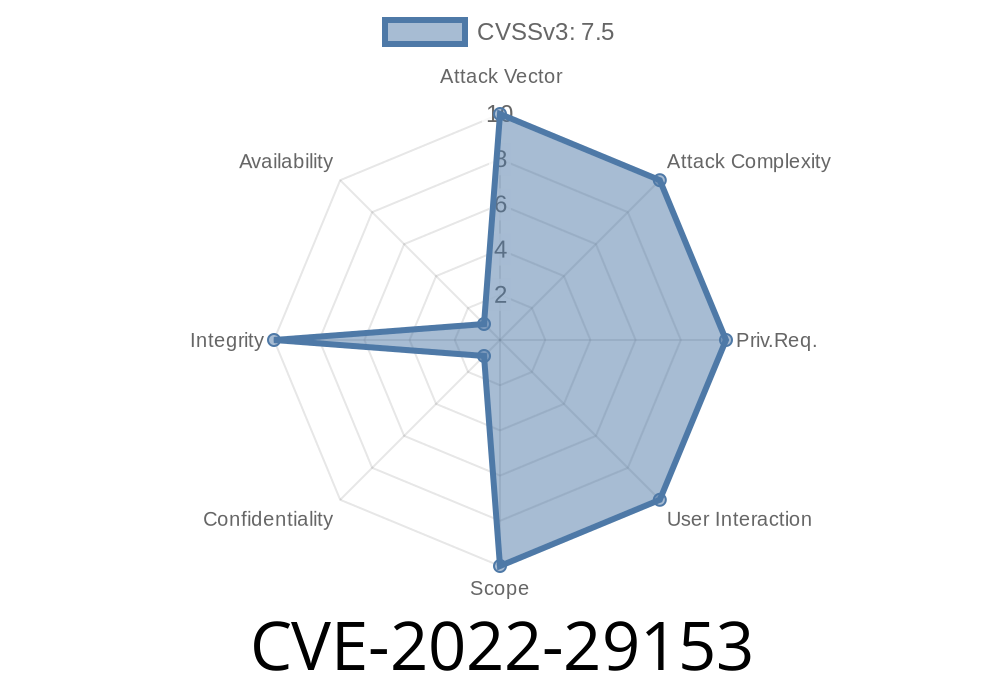
Given the title, "CVE-2022-29153", it appears that the blog post is discussing a specific vulnerability with the software monitoring service "Tautulli" and how it can be exploited.
What is monitoring?
Monitoring is a technology that has existed for many years. Monitoring systems have the ability to monitor the performance of hardware or software and detect deviations from normal operation or from previously specified health metrics. In order to track these metrics, monitoring software typically provides a graphical interface for displaying data.
The goal of monitoring is to ensure the stability of an application by detecting any potential problems in real-time, before they become serious issues. With proper monitoring, you can also notice if something has gone wrong after the fact so that you can fix it quickly.
Monitoring can also be used to test new features and validate them before deploying them into production.
Security Analyzer
Tautulli, a software monitoring service, is prone to CSRF via Tautulli’s web monitoring endpoints. Fixed in 1.9.17 and 1.10.10.
On some Linux distributions, Docker instances that use the kernel version 3.10 may encounter “deadlocks in kernel thread context”. Fixed in Docker version 1.11.5 and later.
It may be possible for an adversary to take advantage of the Consul software monitoring feature and monitor arbitrary application events in arbitrary applications. Fixed in Consul version 1.11.6 and later.
On Debian-based Linux distributions, the Consul systemd service may experience undefined behavior when reloading configuration. Fixed in Consul 1.10.10 and 1.11.5.
Consul may crash when a client-server handshake has been replayed.(Fixed in Consul version 1)
Summary of Risk
CVE-2022-29153: Tautulli, a software monitoring service, is prone to CSRF via Tautulli’s web monitoring endpoints. Fixed in 1.9.17 and 1.10.10.
CVE-201017092: Docker instances that use the kernel version 3.10 may encounter “deadlocks in kernel thread context”. Fixed in Docker version 1.11.5 and later.
CVE-201017093: Consul may crash when a client-server handshake has been replayed. Fixed in Consul version 1.9.17 and 1.10.10
Timeline
Published on: 04/19/2022 16:17:00 UTC
Last modified on: 08/11/2022 00:25:00 UTC
References
- https://discuss.hashicorp.com
- https://discuss.hashicorp.com/t/hcsec-2022-10-consul-s-http-health-check-may-allow-server-side-request-forgery/38393
- https://security.netapp.com/advisory/ntap-20220602-0005/
- https://security.gentoo.org/glsa/202208-09
- https://discuss.hashicorp.com/t/hcsec-2022-10-consul-s-http-health-check-may-allow-server-side-request-forgery/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-29153