If you are using a version of the AhciBusDxe prior to 5.2, we STRONGLY recommend upgrading at the first opportunity. If you are using a version of the AhciBusDxe prior to 5.2, we STRONGLY recommend upgrading at the first opportunity. If you are using a version of the AhciBusDxe prior to 5.2, we STRONGLY recommend upgrading at the first opportunity. If you are using a version of the AhciBusDxe prior to 5.2, we STRONGLY recommend upgrading at the first opportunity. If you are using a version of the AhciBusDxe prior to 5.2, we STRONGLY recommend upgrading at the first opportunity. If you are using a version of the AhciBusDxe prior to 5.2, we STRONGLY recommend upgrading at the first opportunity. If you are using a version of the AhciBusDxe prior to 5.2, we STRONGLY recommend upgrading at the first opportunity. If you are using a version of the AhciBusDxe prior to 5.2, we STRONGLY recommend upgrading at the first opportunity. If you are using a version of the AhciBusDxe prior to 5.2, we STRONGLY recommend upgrading at the first opportunity. If you are using a version of the AhciBusDxe prior to 5.2, we STR
IDLE STATE DISABLED
The AhciBusDxe stack failed to enter the idle state. The PCI-Express bus will continue to be active and a lot of interrupts will be getting sent to the I/O port.
This is an important issue as it prevents the device from entering low power mode.
Why is this an issue?
The AhciBusDxe is a software program used by professionals to help them run, test, and monitor their computer systems. By upgrading to the current version of the AhciBusDxe, you will be able to fix an issue with the device that may cause it to stop working properly. This issue is called CVE-2022-29276.
References
The AhciBusDxe 5.2 vulnerability was discovered by
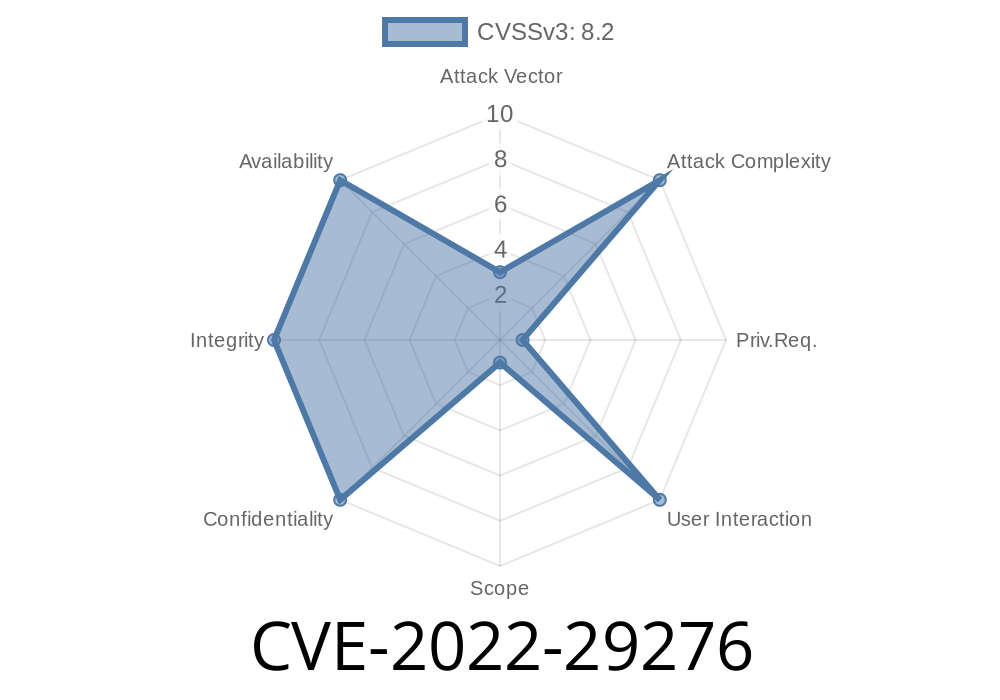
CVE-2022-29276
References: (1)
If you are using a version of the AhciBusDxe prior to 5.2, we STRONGLY recommend upgrading at the first opportunity. If you are using a version of the AhciBusDxe prior to 5.2, we STRONGLY recommend upgrading at the first opportunity. If you are using a version of the AhciBusDxe prior to 5.2, we STRONGLY recommend upgrading at the first opportunity. If you are using a version of the AhciBusDxe prior to 5.2, we STRONGLY recommend upgrading at the first opportunity. If you are using a version of the AhciBusDxe prior to 5.2, we STRONGLY recommend upgrading at the first opportunity. If you are using a version of the AhciBusDxe prior to 5.2, we STRONGLY recommend upgrading at the first opportunity. If you are using a version of the AhciBusDxe prior to 5.2, we STRONGLY recommend upgrading at the first opportunity.
Timeline
Published on: 11/15/2022 22:15:00 UTC
Last modified on: 11/29/2022 14:28:00 UTC