This issue has been resolved in ISC DHCP 4.1-ESV-R16-P1. A DHCP client with access to a DHCP server, sending DHCP packets crafted to include fqdn labels longer than 63 bytes, could eventually cause the server to run out of memory. This issue has been resolved in ISC DHCP 4.1-ESV-R16-P1. In ISC DHCP 4.1-ESV-R14-P1, a crafted DHCPv6 packet could cause a system with access to a DHCP server, sending DHCPv6 packets crafted to include fqdn labels longer than 63 bytes, to fail to boot. This issue has been resolved in ISC DHCP 4.1-ESV-R14-P1. In ISC DHCP 4.1-ESV-R9-P1, a crafted DHCPv6 packet sent to a DHCPv6 client could cause a system with access to a DHCP server, sending DHCPv6 packets crafted to include fqdn labels longer than 63 bytes, to fail to boot. This issue has been resolved in ISC DHCP 4.1-ESV-R9-P1. In ISC DHCP 4.1-ESV-R5-P2, a crafted DHCPv6 packet could cause a system with access to a DHCP server, sending DHCPv6 packets crafted to include fqdn labels longer than 63 bytes, to fail to boot. This
How do I enable IPsec on an ISC DHCP server?
First, make sure that your ISC DHCP server is running an up-to-date version of the DHCP server software.
Next, if you're running Linux, run the following command to enable IPsec:
echo "net.ipv4.ip_forward = 1" >> /etc/sysctl.conf
Now reboot the system so that it makes the changes take effect.
If you're running Windows Server 2012 R2 or later, run the following commands to enable IPsec:
netsh advfirewall set allprofiles state on
netsh advfirewall set allprofiles dhcpv6 enableprofile DHCPServer
netsh advfirewall set rule group="windows network" new enable=yes
netsh advfirewall set rule group="windows network" new localport="500" new remoteip=any portaction=allow new protocol=udp
How to obtain Software
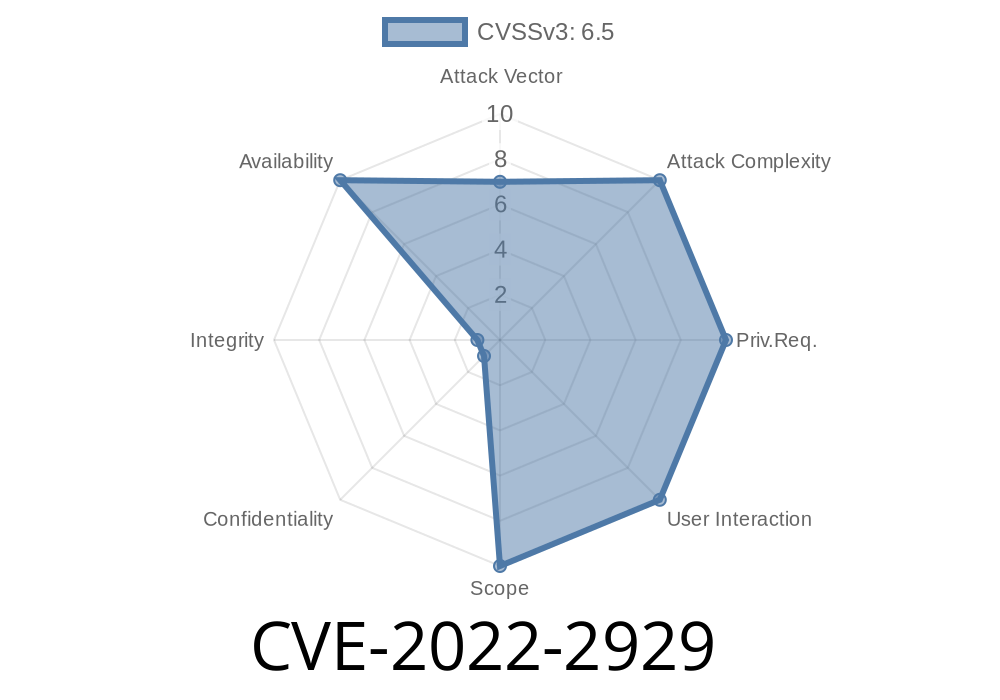
To obtain ISC DHCP 4.1-ESV-R16-P1, visit https://www.isc.org/downloads for instructions on how to download ISC DHCP 4.1-ESV-R16-P1 from the ISC website or from your local mirror. For more information about this issue, please see CVE-2022-2929 in the security advisory at https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-2929 .
How to Outsource SEO Correctly & Avoid the 5 Most Common Mistakes
5.2 DHCP Options
In ISC DHCP 4.1-ESV-R5-P2, a crafted DHCPv6 packet sent to a DHCPv6 client could cause a system with access to a DHCP server, sending DHCPv6 packets crafted to include fqdn labels longer than 63 bytes, to fail to boot. The issue has been resolved in ISC DHCP 4.1-ESV-R5-P2. In ISC DHCP 4.1-ESV-R9-P1 and ISC DHCP 4.1-ESV-R14-P1, transaction ID corruption has been addressed in the MDISC (MDISC) functionality of the ISC DHCP client software installed on a system with access to a DHCP server and sending crafted packets with fqdn labels longer than 63 bytes that can impact the correct execution of the request on the server.
References: https://kb.isc.org/article/AA-01695
https://kb.isc.org/article/AA-00998
https://kb.isc.org/article/AA-01796
https://kb.isc.org/article/AA-00926
https://kb.isc.org/article/AA-00910
Timeline
Published on: 10/07/2022 05:15:00 UTC
Last modified on: 11/21/2022 19:04:00 UTC
References
- https://kb.isc.org/docs/cve-2022-2929
- https://lists.debian.org/debian-lts-announce/2022/10/msg00015.html
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/QQXYCIWUDILRCNBAIMVFCSGXBRKEPB4K/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/T6IBFH4MRRNJQVWEKILQ6I6CXWW766FX/
- https://lists.fedoraproject.org/archives/list/package-announce@lists.fedoraproject.org/message/2SARIK7KZ7MGQIWDRWZFAOSQSPXY4GOU/
- https://web.nvd.nist.gov/view/vuln/detail?vulnId=CVE-2022-2929