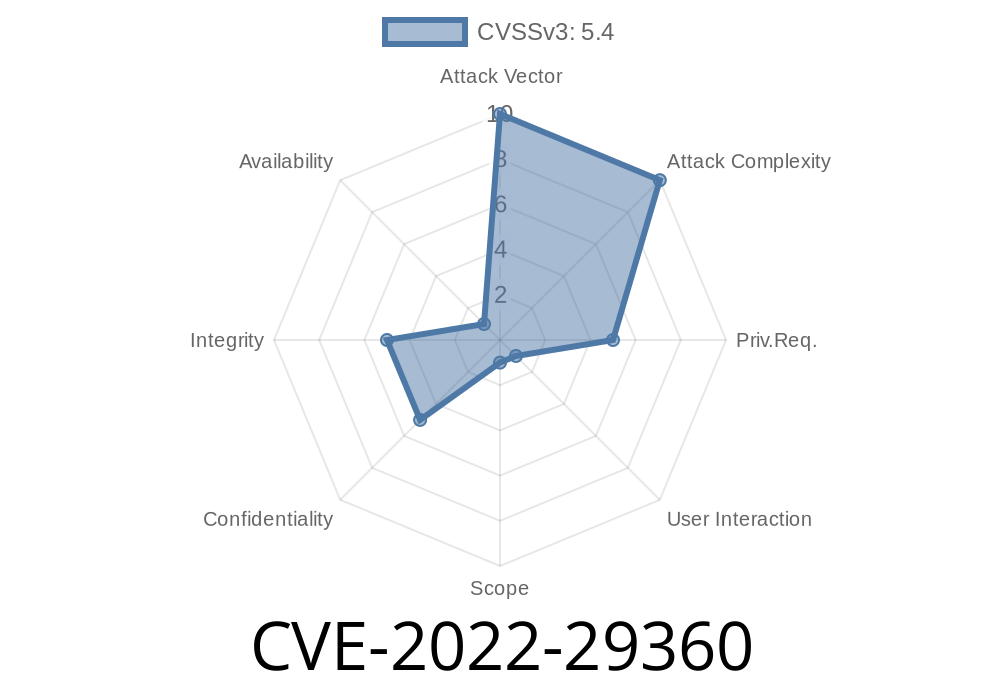
An attacker can access the system via an email message that sends a crafted “From” field on a system that has a vulnerable version of RainLoop installed. XSS occurs in the “notifications” section of the “Settings” page. The severity of XSS depends on the value of the “From” email field when the user is notified of a campaign by RainLoop. If an attacker can access the “Settings” page and send a crafted “From” email address, then the user’s session is vulnerable to an XSS attack. An attacker can send a crafted email message from a reliable external email address to trigger an XSS. An attacker can also craft an email message from an unreliable external email address and send it to trigger XSS.
Vulnerability overview
An XSS vulnerability allows an attacker to inject malicious scripts into the user's session. When the user visits a website that is vulnerable to XSS, an attacker can send specially crafted email messages from reliable and unreliable external email addresses in order to trigger an XSS attack. This attack is known as cross-site scripting (XSS).
Vulnerable Servers
An attacker can exploit an XSS vulnerability over email to send a crafted "From" field that sends the user's session data to an attacker.
Vulnerability Discovery
CVE-2022-29360 was discovered by a team of researchers looking for vulnerabilities in RainLoop. The discovery is the result of a series of scans that were performed on various sites to determine if they were vulnerable to XSS attacks. One of the websites that was scanned was www.rainloop.com, which had an XSS vulnerability in its “notifications” section in the “Settings” page.
Timeline
Published on: 07/28/2022 21:15:00 UTC
Last modified on: 08/04/2022 16:03:00 UTC