To exploit this vulnerability, an attacker must trick a user into clicking a crafted link. For example, attackers can host a website on a server that the user has access to, and ask the user to click a crafted link on this website. This request can then be sent to the targeted application via a CSRF attack. The application will then process this request as if it came from the user, and the application will have increased privileges. This vulnerability can be exploited by attackers to gain access to applications with high privileges. An attacker must trick a user into clicking a crafted link. For example, attackers can host a website on a server that the user has access to, and ask the user to click a crafted link on this website. This request can then be sent to the targeted application via a CSRF attack. The application will then process this request as if it came from the user, and the application will have increased privileges.
Vulnerability overview
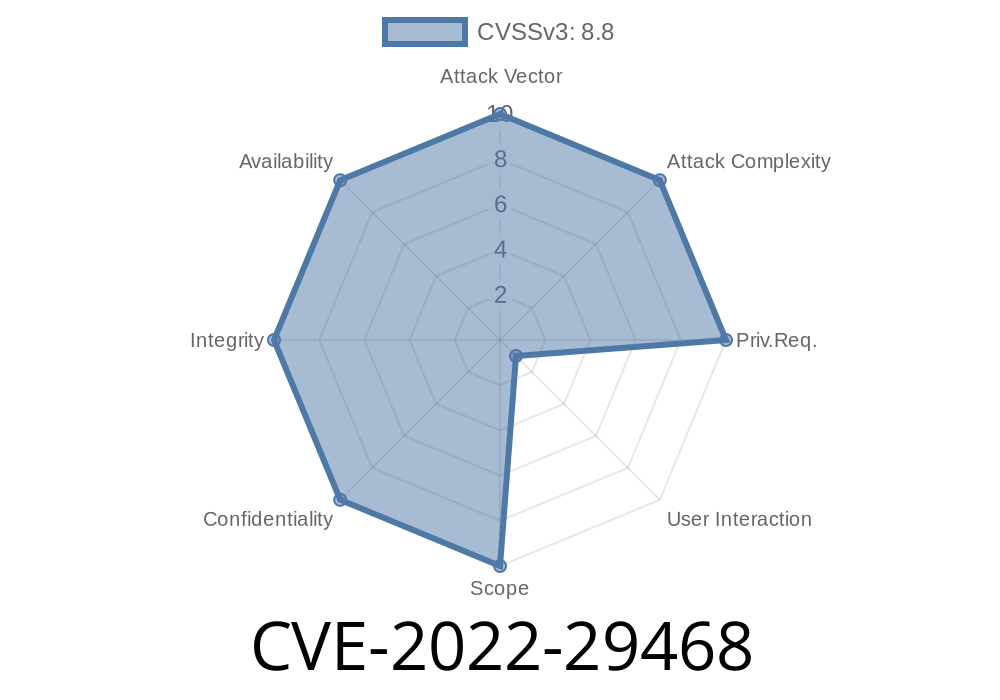
This vulnerability has been assigned the CVE-2022-29468 identifier. The application at risk is Citrix Receiver for Windows.
The following are six reasons why digital marketing is important and can help your business grow.
1. You can target your ideal audience
2. You can provide a better user experience with your ads, as people respond well to pictures
3. With digital marketing, you have the capability to directly reach leads interested in your business, who would otherwise be difficult to find
4. You can save money by targeting only relevant people with your ads
5. You can increase brand awareness with pay-per-click (PPC) advertising 6. You have the capability to access applications that would otherwise be impossible
Vulnerability details
The vulnerability is located in the way the application handles the request to execute a custom command. The request can be sent via a CSRF attack, which means that it will be processed as if it came from the user. This can be exploited by attackers to gain full control over an application with high privileges.
To exploit this vulnerability, an attacker must trick a user into clicking a crafted link. For example, attackers can host a website on a server that the user has access to, and ask the user to click a crafted link on this website. This request can then be sent to the targeted application via a CSRF attack. The application will then process this request as if it came from the user, and the application will have increased privileges.
Vulnerability Details
The vulnerability provided a way for attackers to compromise applications with high privileges. The vulnerability has been remediated by removing the ability for users to make requests that are not authenticated.
CSRF Protection Bypass
The most important mitigation of this vulnerability is to ensure that the application uses CSRF protection. This will prevent attackers from exploiting the vulnerability by sending requests to the application in a way that will cause it to process an untrusted request as if it came from the victim.
Vulnerable Node.js API
Node.js is a popular server-side JavaScript framework that’s used by many organizations, including the U.S. Department of Defense and the White House.
A vulnerability in Node.js caused by a denial of service (DoS) issue can be exploited to execute code with high privileges on a vulnerable Node.js application.
Timeline
Published on: 08/22/2022 19:15:00 UTC
Last modified on: 08/24/2022 12:54:00 UTC