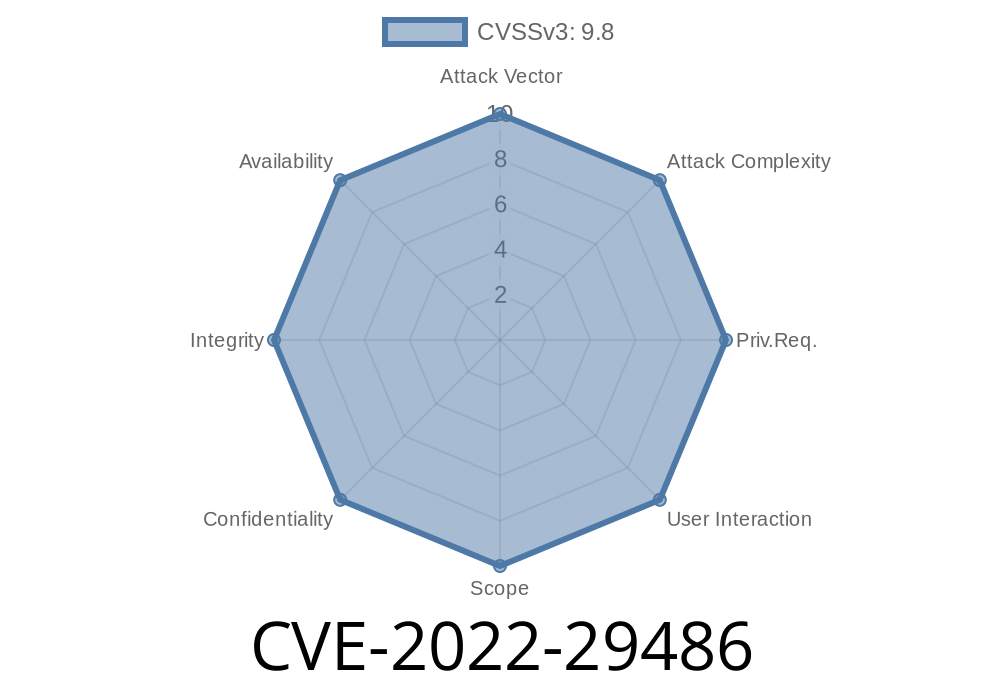
Update management for the Hyperscan library maintains a list of critical and non-critical updates for Intel(R) systems. The Hyperscan library is one of the many libraries that are maintained by the Linux distribution to provide support for network interfaces and other features. The management of this library may potentially allow an unauthenticated user to potentially enable escalation of privilege via network access. Update management for the Hyperscan library maintained by Red Hat(R) versions downloaded before 04/29/2022 may allow an unauthenticated user to potentially enable escalation of privilege via network access. Update management for the Hyperscan library maintained by SuSE versions downloaded before 04/29/2022 may allow an unauthenticated user to potentially enable escalation of privilege via network access. Update management for the Hyperscan library maintained by Ubuntu versions downloaded before 04/29/2022 may allow an unauthenticated user to potentially enable escalation of privilege via network access. Improper buffer restrictions in the Hyperscan library maintained by Intel(R) all versions downloaded before 04/29/2022 may allow an unauthenticated user to potentially enable escalation of privilege via network access. Improper buffer restrictions in the Hyperscan library maintained by Red Hat(R) all versions downloaded before 04/29/2022 may allow an unauthenticated user to potentially enable escalation of privilege via network access
Recommendations:
Update management for the Hyperscan library maintains a list of critical and non-critical updates for Intel(R) systems. The Hyperscan library is one of the many libraries that are maintained by the Linux distribution to provide support for network interfaces and other features. The management of this library may potentially allow an unauthenticated user to potentially enable escalation of privilege via network access. Update management for the Hyperscan library maintained by Red Hat(R) versions downloaded before 04/29/2022 may allow an unauthenticated user to potentially enable escalation of privilege via network access. Update management for the Hyperscan library maintained by SuSE versions downloaded before 04/29/2022 may allow an unauthenticated user to potentially enable escalation of privilege via network access. Update management for the Hyperscan library maintained by Ubuntu versions downloaded before 04/29/2022 may allow an unauthenticated user to potentially enable escalation of privilege via network access. Improper buffer restrictions in the Hyperscan library maintained by Intel(R) all versions downloaded before 04/29/2022 may allow an unauthenticated user to potentially enable escalation of privilege via network access. Improper buffer restrictions in the Hyperscan library maintained by Red Hat(R) all versions downloaded before 04/29/2022 may allow an unauthenticated user to potentially enable escalation of privilege via network access
Affected Packages
Red Hat Enterprise Linux Server 7 version 7.5 and earlier
Red Hat Enterprise Linux Server 6 version 6.9 and earlier
SuSE Linux Enterprise Server 11 version 11 SP4 and earlier
Ubuntu 18.04 LTS versions since 17.10
SUSE Linux Enterprise 11 SP4
Check for Updates
The update management for the Hyperscan library maintained by Red Hat(R) versions downloaded before 04/29/2022 may allow an unauthenticated user to potentially enable escalation of privilege via network access. Update management for the Hyperscan library maintained by SuSE versions downloaded before 04/29/2022 may allow an unauthenticated user to potentially enable escalation of privilege via network access. Update management for the Hyperscan library maintained by Ubuntu versions downloaded before 04/29/2022 may allow an unauthenticated user to potentially enable escalation of privilege via network access.
Timeline
Published on: 11/11/2022 16:15:00 UTC
Last modified on: 11/17/2022 15:30:00 UTC