The issue was discovered during internal penetration testing. Vulnerable versions are Mitsubishi Electric GX Works3 versions 1.015R and later. An attacker can exploit the issue by sending a crafted email message to an employee. MELSEC safety CPU modules could be accessed by the attacker. Mitmsec Electric GX Works3 versions 1.015R and later are vulnerable. An attacker can exploit the issue by sending a crafted email message to an employee. MELSEC safety CPU modules could be accessed by the attacker. Mitmsec Electric GX Works3 versions 1.015R and later are vulnerable. An attacker can exploit the issue by sending a crafted email message to an employee. MELSEC safety CPU modules could be accessed by the attacker. Mitmsec Electric GX Works3 versions 1.015R and later are vulnerable. An attacker can exploit the issue by sending a crafted email message to an employee. MELSEC safety CPU modules could be accessed by the attacker. Mitmsec Electric GX Works3 versions 1.015R and later are vulnerable. An attacker can exploit the issue by sending a crafted email message to an employee. MELSEC safety CPU modules could be accessed by the attacker. Mitmsec Electric GX Works3 versions 1.015R and later are vulnerable. An attacker can exploit the issue by sending a crafted email message to an employee. MELSEC safety CPU modules could be accessed by the attacker. Mitmsec Electric GX Works
Vulnerable / tested versions of the product
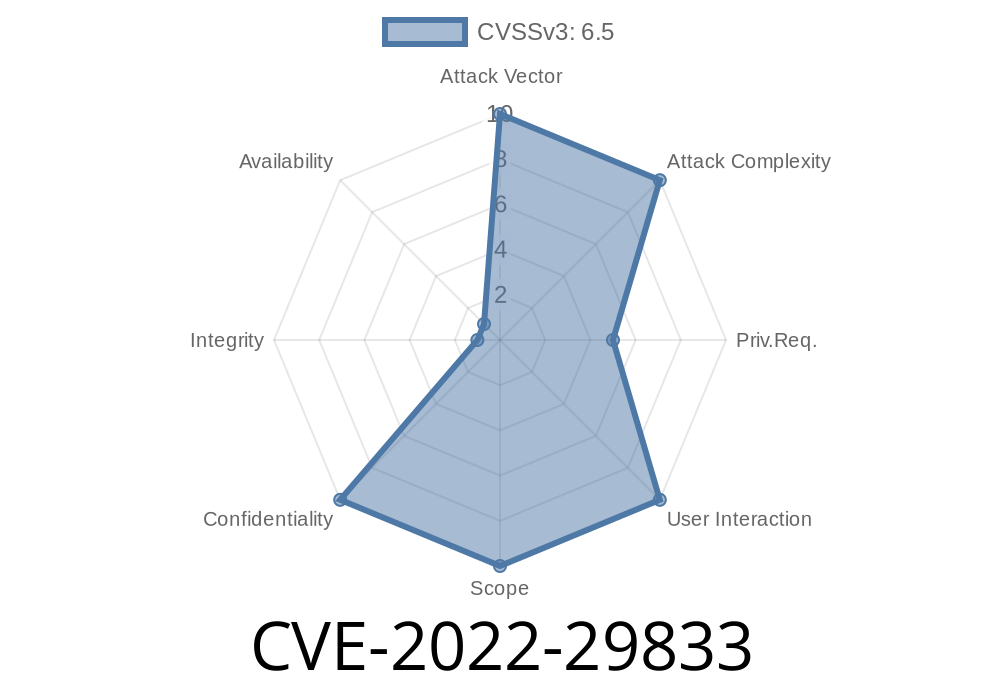
CVE-2022-29833 is a risk rating event that has been assigned to Mitsubishi Electric GX Works3 versions 1.015R and later. The issue was discovered during internal penetration testing. Vulnerable versions are Mitsubishi Electric GX Works3 versions 1.015R and later.
Affected Software: CVE-2022-29833
Mitmsec Electric GX Works3 versions 1.015R and later are vulnerable. An attacker can exploit the issue by sending a crafted email message to an employee. MELSEC safety CPU modules could be accessed by the attacker. Mitmsec Electric GX Works3 versions 1.015R and later are vulnerable. An attacker can exploit the issue by sending a crafted email message to an employee. MELSEC safety CPU modules could be accessed by the attacker. Mitmsec Electric GX Works3 versions 1.015R and later are vulnerable. An attacker can exploit the issue by sending a crafted email message to an employee. MELSEC safety CPU modules could be accessed by the attacker. Mitmsec Electric GX Works3 versions 1.015R and later are vulnerable. An attacker can exploit the issue by sending a crafted email message to an employee. MELSEC safety CPU modules could be accessed by the attacker. Mitmsec Electric GX Works3 versions 1.015R and later are vulnerable. An attacker can exploit the issue by sending a crafted email message to an employee, who will then execute it on their computer using their default credentials for that computer (iTunes, Windows, or some other application).
MITIGATION
Users of vulnerable versions should apply the latest patch.
Timeline
Published on: 11/25/2022 00:15:00 UTC
Last modified on: 11/28/2022 20:57:00 UTC