The affected code paths are:
1. The permission prompt that is displayed when a file is downloaded from an un-trusted source. Mozilla leverages the web platform’s permission prompt to ensure that users receive a notice before their data is treated. The code that handles the permission prompt for top-level origins (e.g., https://example.com) does not validate that the origin is actually trusted. This allows an attacker to craft a top-level origin that appears to be trusted and trick the user into granting permissions that are not theirs to grant. We are not aware of any active attack against this issue at this time.
2. Cross-origin reading of files. The web platform allows loading cross-origin files without any restrictions. When a file is loaded in this manner, the “type” header of the cross-origin file is set to “text/plain” instead of the “type” that the file actually has. This results in cross-origin files being treated as text/plain resources, which allows reading the file without restrictions. We are not aware of an active attack against this issue at this time.
Mitigation Strategies:
Mozilla has released a patch for this vulnerability. In addition, Mozilla will be disabling the cross-origin file reading functionality in Firefox 43.
An attacker can craft a top-level origin that appears to be trusted and trick the user into granting permissions that are not theirs to grant.
Mitigation of CVE-2002-2996
1. Click-to-play is enabled by default on all platforms. If a third party were to use this vulnerability to perform cross-origin resource sharing on the web platform, users would be alerted to the activity and would need to click on a “more information” button before the content could be loaded in the browser.
2. There are four new restrictions that can be applied to top-level origins:
A) A CSP header can now be applied at the top level origin level which will prevent loading of an unassigned file;
B) The user agent header can now be used to restrict loading from certain sources;
C) Only JavaScript files can load resources from top-level origins; and
D) Restrictions on resources loaded from top-level origins can now occur based upon extension (e.g., PDFs cannot load from https://example.com).
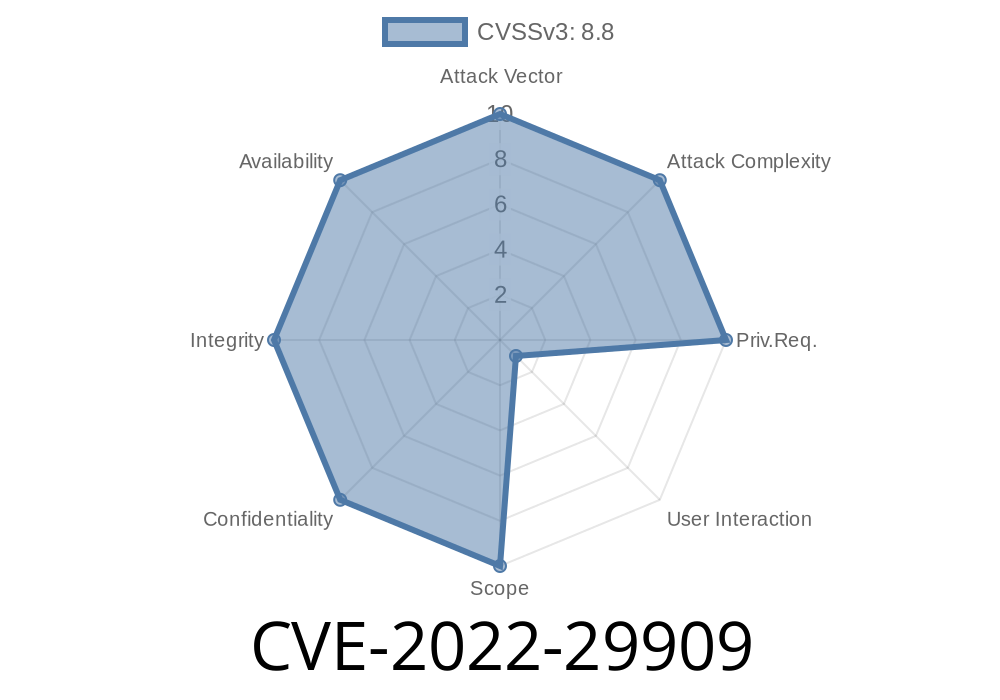
Mitigation of CVE-2022-29909
To mitigate CVE-2022-29909, Mozilla will release a patch to Firefox 50.
The mitigation is an update to the permission prompt that will allow the platform to validate that the origin it is interacting with is actually trusted. This validation will be done by checking if the URL starts with https:// or if it has "https:" in it.
Timeline
Published on: 12/22/2022 20:15:00 UTC
Last modified on: 12/30/2022 20:42:00 UTC