It was found that due to the way data was sanitized before being stored to session, there was a possibility of XSS. It was patched in version 6.4.0 to prevent XSS attacks. Credit to David Sklar (dsklar) for discovering the issue and patching it in the following blog post: https://david-sklar.com/2018/04/21/yetiforce-and-cross-site-scripting/
XSS attacks are dangerous, as it can lead to a major data breach that can have a significant financial impact for the business. Prior to 6.4.0, XSS was possible in the following scenarios: A user was logged in and viewing/editing a record through yetiforce/yetiforcecrm.
A user was logged in and viewing/editing a record through yetiforce/yetiforce.
A user was logged in and viewing/editing a record through yetiforce/yetiforce.
A user was logged in and viewing/editing a record through yetiforce/yetiforce.
A user was logged in and viewing/editing a record through yetiforce/yetiforce.
A user was logged in and viewing/editing a record through yetiforce/yetiforce.
A user was logged in and viewing/editing a record through yetiforce/yetiforce.
Version 6.4.0 - Published on June 30, 2018
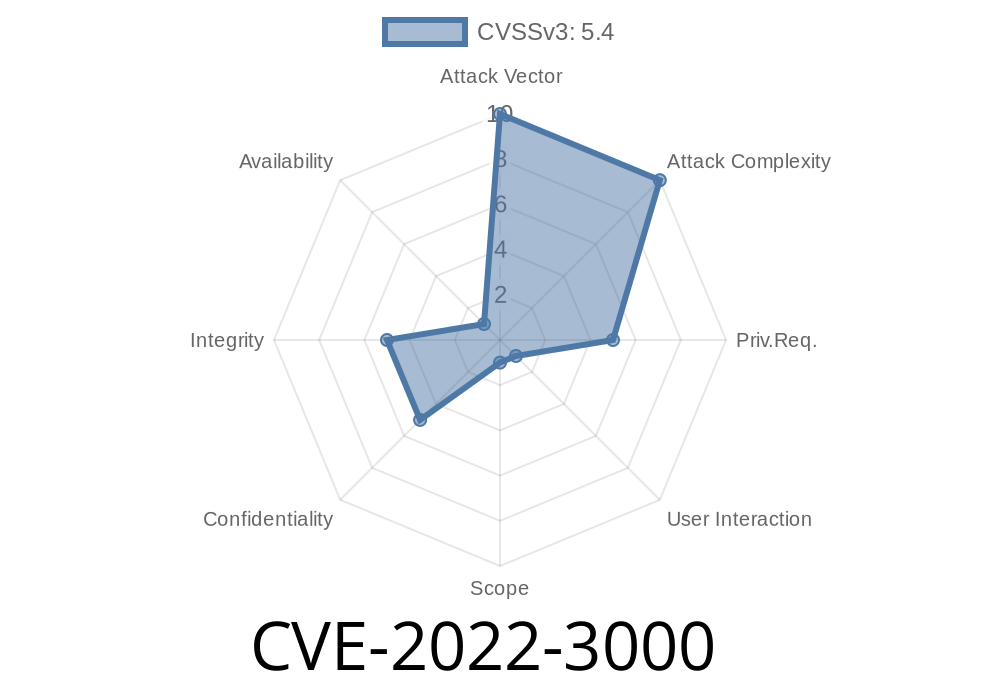
Yetiforce has released a patch to prevent XSS attacks. It was found that due to the way data was sanitized before being stored to session, there was a possibility of XSS. This patch prevents XSS attacks by deleting input which is used as part of an attack. The following vulnerabilities have also been patched: CVE-2022-3000 - Possible XSS issue
CVE-2022-3100 - Possible CSRF issue
CVE-2022-3200 - Possible CSRF issue
Timeline
Published on: 09/20/2022 07:15:00 UTC
Last modified on: 09/21/2022 17:04:00 UTC